Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

For the first time, cloud security breaches and incidents are more commonplace than on-premises attacks. According to the 2021 Verizon Data Breach Investigations Report (DBIR), in 2020, 73% of cyberattacks involved cloud assets, compared to only 27% in the previous year.

Explore how CISOs can secure supply chains and meet evolving cyber regulations with strategies from our new ebook on cybersecurity resilience.

Discover why millions of smartphones worldwide are at risk due to cluttered and outdated apps. Dive into our research to learn more about this critical issue.
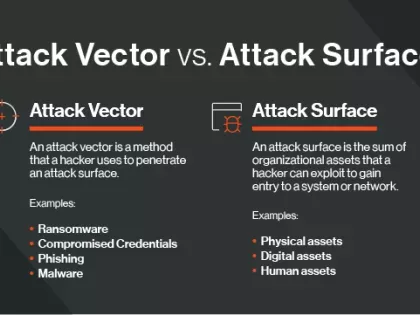
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

This blog post details one of these very unique cases: `CVE-2022-44877`, an unauthenticated Command Injection issue, flagged by CISA as a Known Exploited Vulnerability (CISA KEV).

Learn the difference between third-party vs. fourth-party risk and how you can extend your risk management program to cover both.

Discover how executives and investors are aligning to fortify resilience in the face of evolving cyber threats.

In an era of rapid threat expansion, proper storytelling by CISOs can be the key to build confidence with customers, regulators, board members, and other stakeholders.
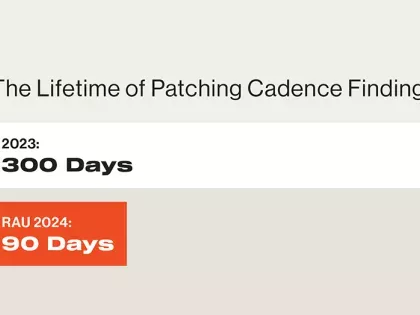
As we announced in January, Bitsight will conduct a ratings algorithm update (RAU) on July 10, 2024, as part of our ongoing efforts to optimize our methodology to provide the best external indicator of the performance of cybersecurity controls.

Developing a VRM plan from scratch or looking to scale your existing program? Here are some cybersecurity IT risk assessment templates to help you get started.

Dive into the realm of cybersecurity excellence, harnessing the power of exposure management and benchmarking to drive proactive resilience with peer insights.

Aujourd’hui, les violations de données provenant de tiers représentent le plus grand risque cyber. Découvrez les violations les plus importantes et les mesures que vous pouvez prendre pour protéger votre organisation.

Highlight cyber exposure management's role in risk control and urge collaboration between security experts and business leaders for improved cyber risk management.

Today’s opportunistic hackers are seasoned professionals who are getting more adept at exploiting your organization’s digital attack surface. To do this they employ a variety of attack vectors.

For the first time ever, Diligent and Bitsight have partnered to see just how well the board level effort is translating into reducing Cyber Risk for their company.