Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

As more IT resources shift to cloud service providers, it becomes increasingly complex to get a full digital footprint picture. See how Bitsight helps.

Attacks targeting operational technology & industrial control systems are rising while many cut security budgets. Comprehensive strategies and monitoring are essential now more than ever.

With economic sanctions being levied by the US against Iran and a trade war heating up with China, some security experts are cautioning that attacks targeting US critical infrastructure may be inevitable. Are electric utilities prepared to defend themselves and their facilities against these attacks?

Cyber risk mitigation and remediation are often talked about in the same terms. But they are different. Learn how you can optimize both.
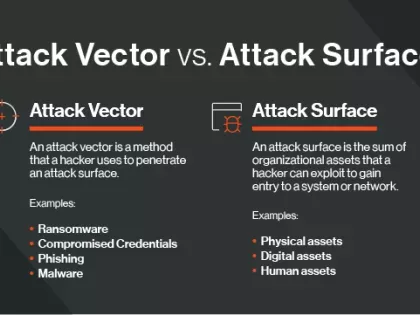
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

Discover how executives and investors are aligning to fortify resilience in the face of evolving cyber threats.

La mise en œuvre d'un plan de réponse aux incidents de cybersécurité peut vous aider à gérer efficacement un cyber-événement, à réduire les perturbations de votre activité et à garantir la conformité.

What is adaptive security? Explore the benefits of this approach to cyber risk reduction and how your organization can get started.

Key Risk Indicators (KRIs) können dabei helfen, Cyberrisiken zu überwachen und zu kontrollieren. Aber auf welche KRIs sollten Sie sich konzentrieren?

Les indicateurs clés de risque (KRI) peuvent aider à surveiller et à contrôler les cyber-risques. Mais sur quels KRI devez-vous vous concentrer ?

Bien que les évaluations de sécurité soient un excellent moyen de démontrer que vous prêtez attention à la cybersanté de l'organisation, vous devez également montrer que vous adhérez aux meilleures pratiques industrielles et réglementaires en matière de sécurité informatique et que vous prenez des décisions éclairées à long terme. . Un cadre de cybersécurité peut aider.

Während Sicherheitsbewertungen eine gute Möglichkeit sind, zu zeigen, dass Sie auf die Cyber-Gesundheit des Unternehmens achten, müssen Sie auch zeigen, dass Sie sich an branchenübliche und behördliche Best Practices für die IT-Sicherheit halten und fundierte Entscheidungen auf lange Sicht treffen . Ein Cybersicherheits-Framework kann helfen.

While security ratings are a great way to demonstrate that you’re paying attention to the cyber health of the organization you also need to show that you’re adhering to industry and regulatory best practices for IT security and making informed decisions for the long-term. A cybersecurity framework can help.

Open port vulnerabilities can increase cyber risk exposure. Learn what they are and how you can quickly find and fix them.

Consider these three best practices for mapping your digital footprint and using these insights to better assess cyber risk and drive continuous improvement in your security program.