Download this guide to learn how exposure management can transform CISOs from protectors to strategic risk leaders, providing the tools needed to prioritize security efforts effectively.
The Race to Secure Operational Technologies is On
Tags:

Whether it's because industrial control systems remain quite vulnerable to attacks, or because these systems manage valuable physical resources and uptime is essential—or a bit of both—attackers are increasingly targeting operational technology (OT) and industrial control systems (ICS).
Consider a recent warning by the FBI, CISA, the NSA, the EPA, and Israel's National Cyber Directorate that highlighted the threat actor behind the attack that occurred last year against the Municipal Water Authority of Aliquippa, Pennsylvania. Those attackers targeted a programmable logic controller from the manufacturer, Unitronics Vision. According to the reporting agencies, the attackers attempted to strike several US-based water facilities within multiple states that relied on devices from that manufacturer.
The attacks are growing. In this Washington Post story, China's cyber army is invading critical U.S. services, and threat actors have targeted power and water utilities, telecommunication, and transportation systems. While these attacks won't subside soon, those companies that run critical control systems are taking steps to secure their systems better.
Yet, even as attacks rise, organizations that own and operate ICS environments are decreasing the amount they spend on their security budgets and a fifth of such organizations don’t even have a security budget. This is despite the fact that the vast majority see threats against ICS devices as serious threats.
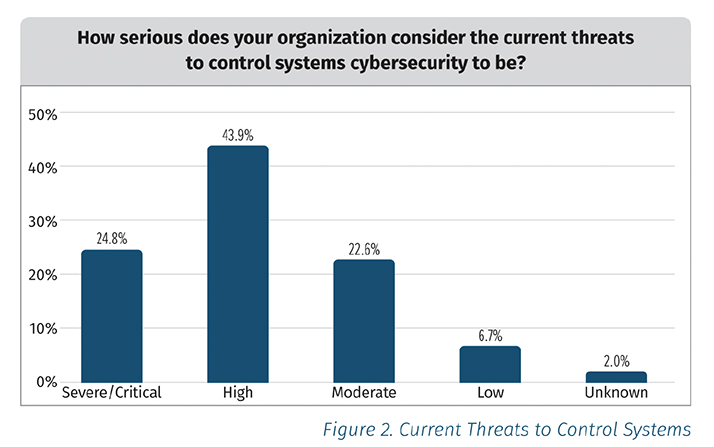
Consider the findings from a recent SANS ICS/OT survey, which revealed that 43.9% of respondents believe that the current threats against ICS are “high” and 24.8% believe the current threats are severe/critical. Shockingly, when asked to characterize their ICS/OT cybersecurity funding: 21% said they don’t have a budget.
Research shows hundreds of thousands of exposed ICS devices
Research published by Bitsight and Schneider Electric last fall identified roughly 100,000 exposed ICS. These ICS devices within OT environments control manufacturing systems, chemical plant systems, power grids, traffic light systems, security and water systems, and more. Critical infrastructure firms rely on ICS to control cyber-physical systems, compounding concerns that the exposed systems identified in this research could present significant risks worldwide. According to the Bitsight & Schneider Electric research, Fortune 1000 companies are exposed, including organizations from 96 countries and various sectors.
To identify and measure device exposure, Bitsight found Internet-exposed ICS systems and mapped those systems to its inventory of organizations worldwide. Interestingly, and in the face of commonly accepted best security practices, the company found thousands of organizations use ICS systems that are exposed directly to the public Internet. This, no doubt, creates significant security risks for devices that control how these organizations interact with the physical world: electric and water utilities, manufacturing plants, transportation systems, and more.
Bitsight focused on commonly used ICS protocols, such as BACnet, KNX, Modbus, and Niagara Fox, for its analysis.
Exposed Systems and Potential Consequences
ICS systems are typically essential—they help manage societies' electrical power generation, chemical manufacturing, wastewater treatment, oil and gas refinement, and more. However, because of the nature of these systems, they are often more challenging to patch than traditional IT systems.
For instance, many ICS environments run decades-old industrial devices, and the aging software on these systems makes them challenging to update. The software update process is often tricky and can require downtime, but these systems often run continuously because of their criticality, which makes it challenging to find acceptable downtime windows.
Many times, because of the age of these systems, the devices may have reached the manufacturer's end of life, and software patches won't be forthcoming from the manufacturer.
Many ICS devices can be critical to a region or organization's functioning. While 100,000 exposed ICS devices are a high number, fortunately, Bitsight also observed a downward trend in the number of publicly exposed devices. The reason for the decline? Perhaps organizations are updating aged devices and placing them behind their network firewall, or maybe they are removing at-risk devices from the Internet or finding ways to airgap their at-risk systems. Likely, it's a combination of all of these reasons.
The research showed that the top exposed vertical markets were education, technology, government, business services, manufacturing, utilities, real estate, energy/resources, tourism/hospitality, and finance.

Keeping ICS secure: off the public internet is not enough
While removing devices from the public internet is an excellent first step and a sign that organizations are taking the security of these systems seriously, it's not enough in itself. Security leaders within organizations responsible for securing ICS environments need to realize, and hopefully, they currently do, that these environments need to be connected even when patching isn't immediately feasible.
They also must recognize that the overall security strategy to secure these environments is different than traditional IT environments, and they should turn to an international series of standards that provide guidelines and best practices for securing ICS and operational technology networks, such as the Purdue Model and ISA/IEC 62443.
Security managers first need visibility into their environments to gather a comprehensive inventory of their ICS devices. Understanding the network topology is also crucial. This way, security controls that match the network's and networked devices' exact nature can be designed and implemented. Segmenting these ICS networks into smaller, more discrete networks is another good step. By segmenting networks, the attack surface of the overall network is compartmentalized and more easily secure. Also, should a threat actor gain access to a network segment or device, their widespread access is now limited to that network segment.
Further, ensuring strong access control in the network by ridding the environment of default and weak passwords and implementing multi-factor authentication when possible. Many experts also advise a zero-trust strategy in these environments.
Finally, because systems constantly change and new vulnerabilities are always uncovered, these environments should be continuously monitored. Here, while the SANS survey found one-fifth of organizations that have ICS environments have cybersecurity budgets, of those that are investing in cybersecurity: 60% plan on investing in areas that will help them to increase visibility into ICS assets and configurations.
The decline in internet-exposed ICS devices is also undoubtedly good news, and it's a sign that organizations are likely taking the steps they must take to secure these devices better. However, the question remains about who will get there first: the security practitioner or the threat actor.


