Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

2018 is right around the corner, and while we’re looking forward to what’s coming, we’re also thinking back on the best of this year. Here’s a look at 10 of our most frequently viewed cybersecurity articles in 2017.

As security and risk professionals work to finish out the year, they must also be thoughtful about planning for 2018. While it’s great to end the last quarter of the business year on a strong note, it’s even more critical for businesses to set themselves up for success when returning to work in January. One of the best ways to accomplish this is to be strategic about the extra budget they possess in Q4, and asking themselves this question: how can my organization be mindful about spending extra funds to benefit our security program later on?

October is Cybersecurity Awareness Month, which offers organizations the opportunity to thoroughly examine their security and risk programs and identify where any vulnerabilities might exist. Here at Bitsight, we talk about risk management every day. However, we have to practice what we preach — our IT Team offered some insight into areas where organizations can improve their network health not just this month, but regularly.

If you’re involved in a healthcare-based organization, you’ve likely noticed the push for stronger vendor security and vendor risk management (VRM) practices. There are a few reasons for this.

Security media is pervaded by seemingly ever-increasing and ever-worsening reports of data breaches at businesses ranging from your mom-and-pop corner store to large retail and internet giants. But how accurate is the perception that breaches are on the rise? Are more security events actually happening, or are we simply observing increased compliance with strengthening reporting requirements? More importantly, can companies learn from these incidents or are businesses doomed to repeat them?

You’ve heard it said that a chain is only as strong as its weakest link. When it comes to your cybersecurity team, this adage couldn’t be more appropriate. If you want this team to perform with both diligence and accuracy, it’s critical that you consider the following:

After the initial analysis of the WannaCry ransomware attacks, our Research & Development team put together a global assessment of the impacts and repair process needed for affected systems to recover.
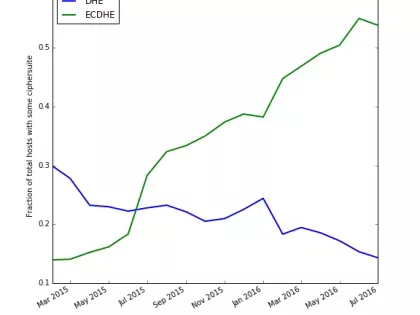
A number of leading torrent websites have gone offline recently, drawing attention again to the use of torrents to share copyrighted material. But the absence of these sites doesn’t mean torrents have stopped. Torrenting is a peer-to-peer technology that doesn’t have a single point of failure. Just because some sites have gone down, doesn’t mean you don’t have to care about torrents on your network. In this post, I want to look at the good, the bad, and the ugly of torrents.

It goes without saying that the following data breaches were incredibly damaging, both to the companies and to those affected. Each has resulted in some level of data loss, financial loss, and reputational harm. Below, we’re exploring what some of the top breaches in 2015, 2014, and 2013 were and examining the commonalities and differences between them.

When I was a young pup studying statistics, I remember reading about a study on weight loss that found three factors correlated with weight loss: weighing yourself daily, eating a good breakfast and having access to work out equipment at home. While none of these cause weight loss directly, together they indicate a passion for and dedication to a healthy lifestyle. Connections like this, where subtle observations can lead to a larger understanding, have always been an interest for me and have driven me forward in my career.