How the Impact of WannaCry Ransomware Was Felt Around the World


After the initial analysis of the WannaCry ransomware attacks, our Research & Development team put together a global assessment of the impacts and repair process needed for affected systems to recover.
This post explores the countries hit hardest by WannaCry, the network composition of IP addresses exhibiting the infection, the industries and company sizes affected most, and how Bitsight Security Ratings changed across industries for organization’s infected with the malware a month after the attacks occurred.
Global Coverage
In the four day period between May 12th and May 15th, the WannaCry ransomware was observed on over 160,000 unique IP addresses. This animated graphic shows the WannaCry events originating from each country as a ratio against events worldwide.
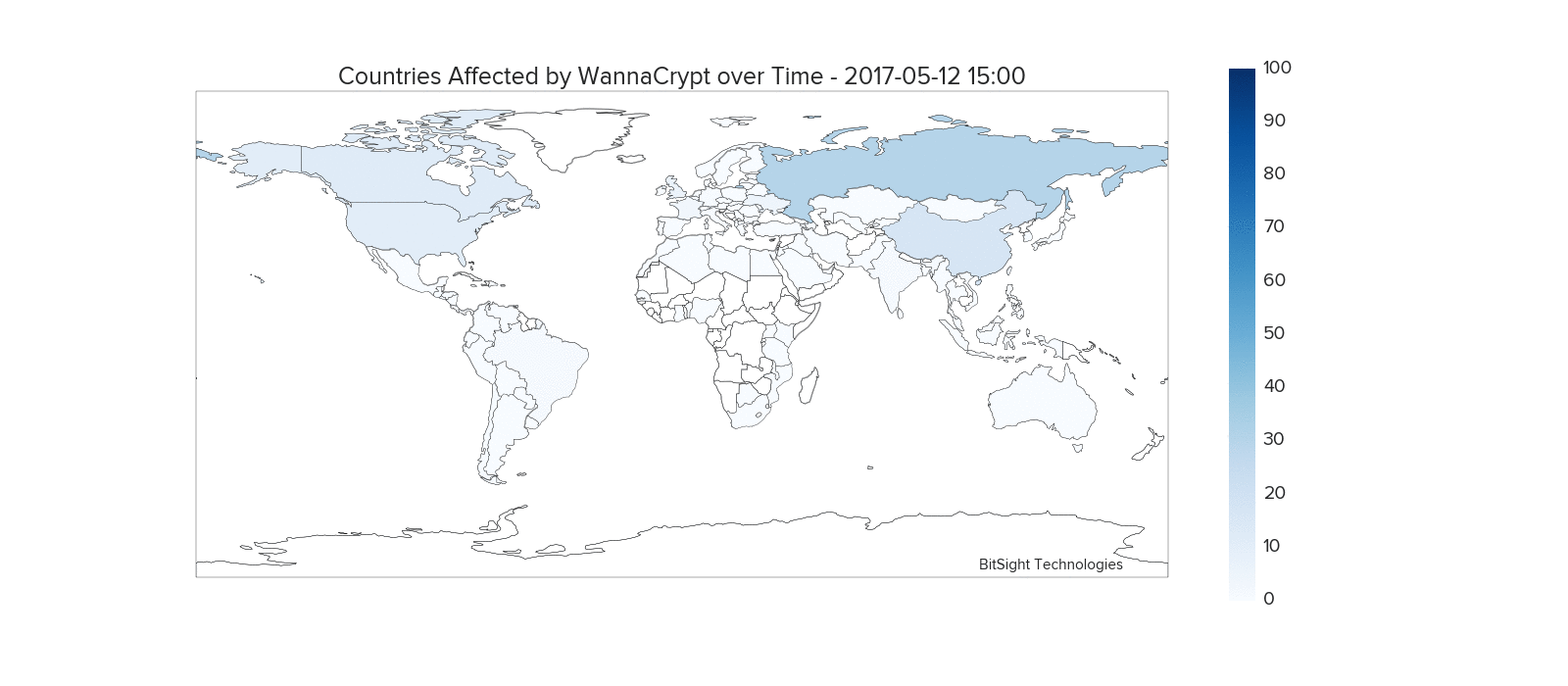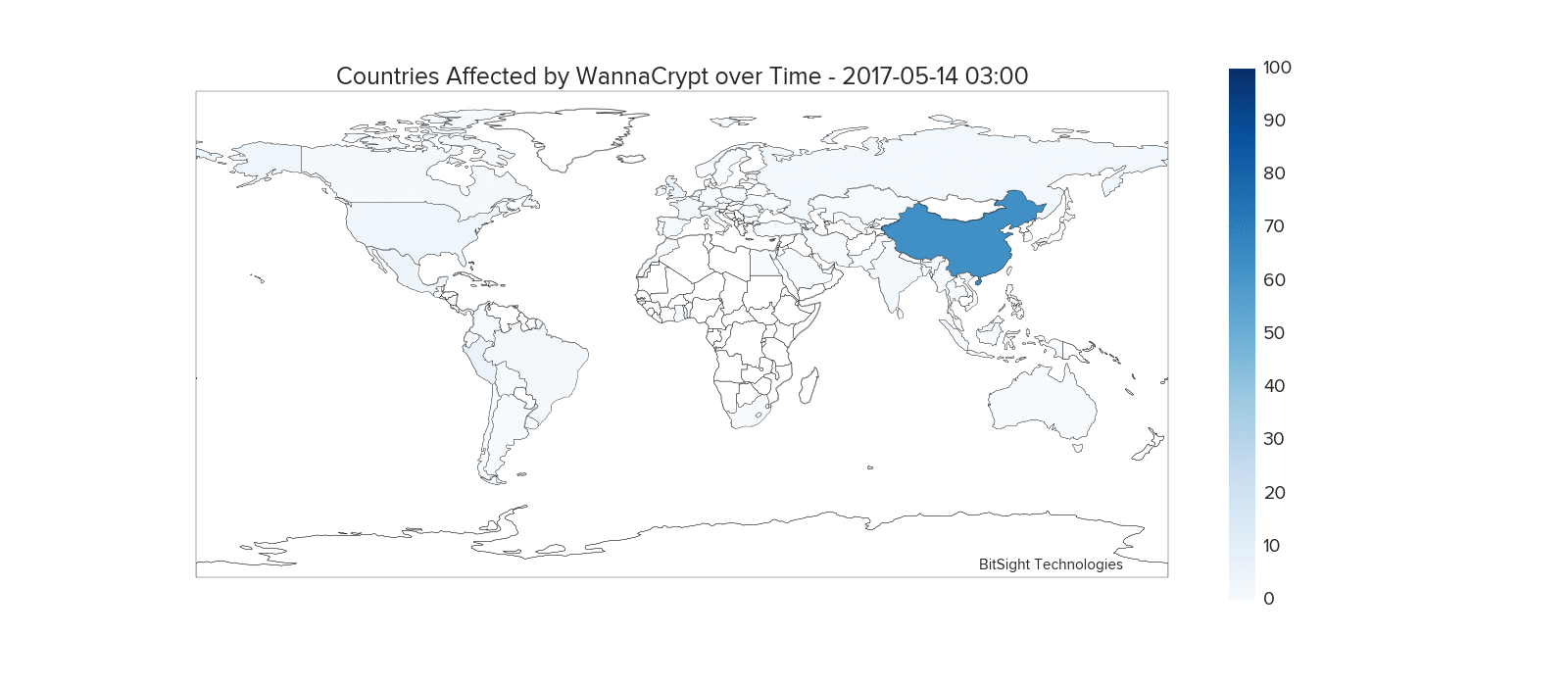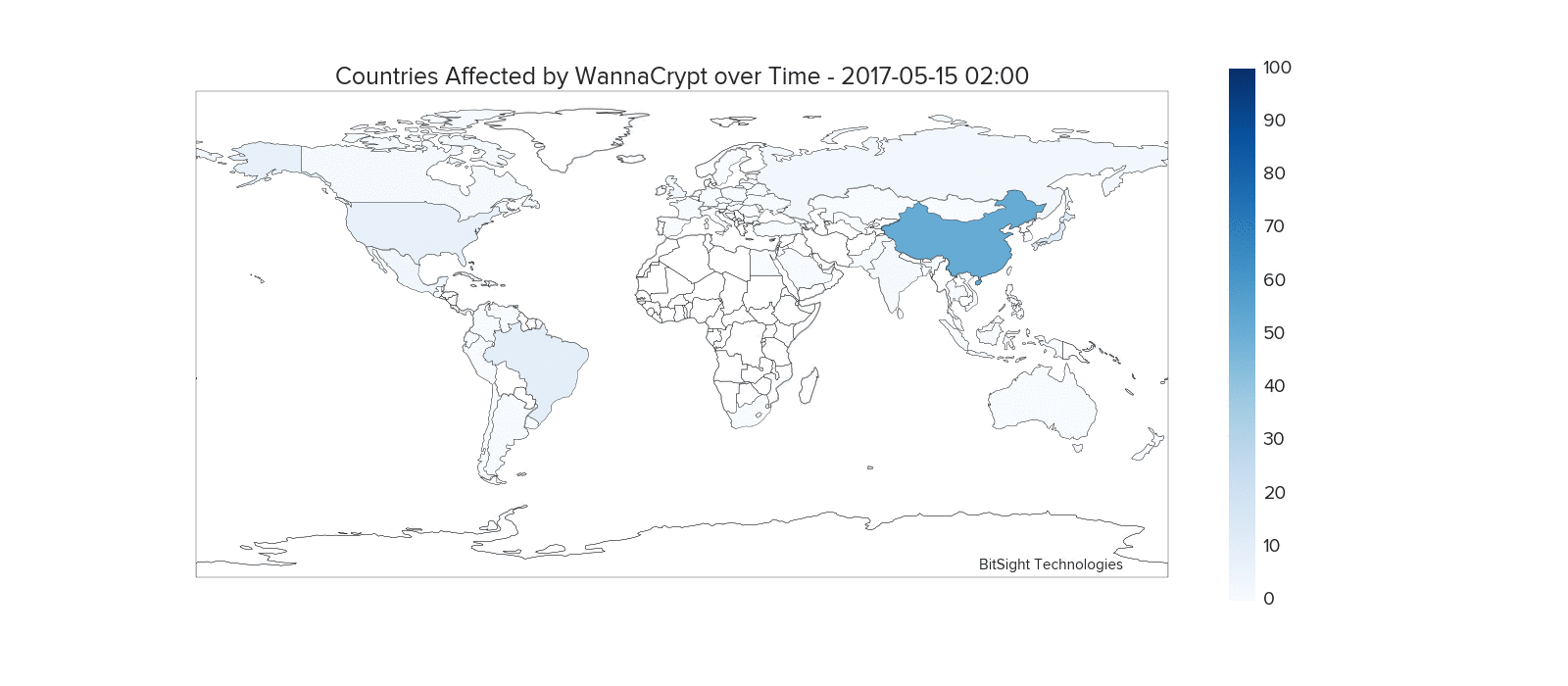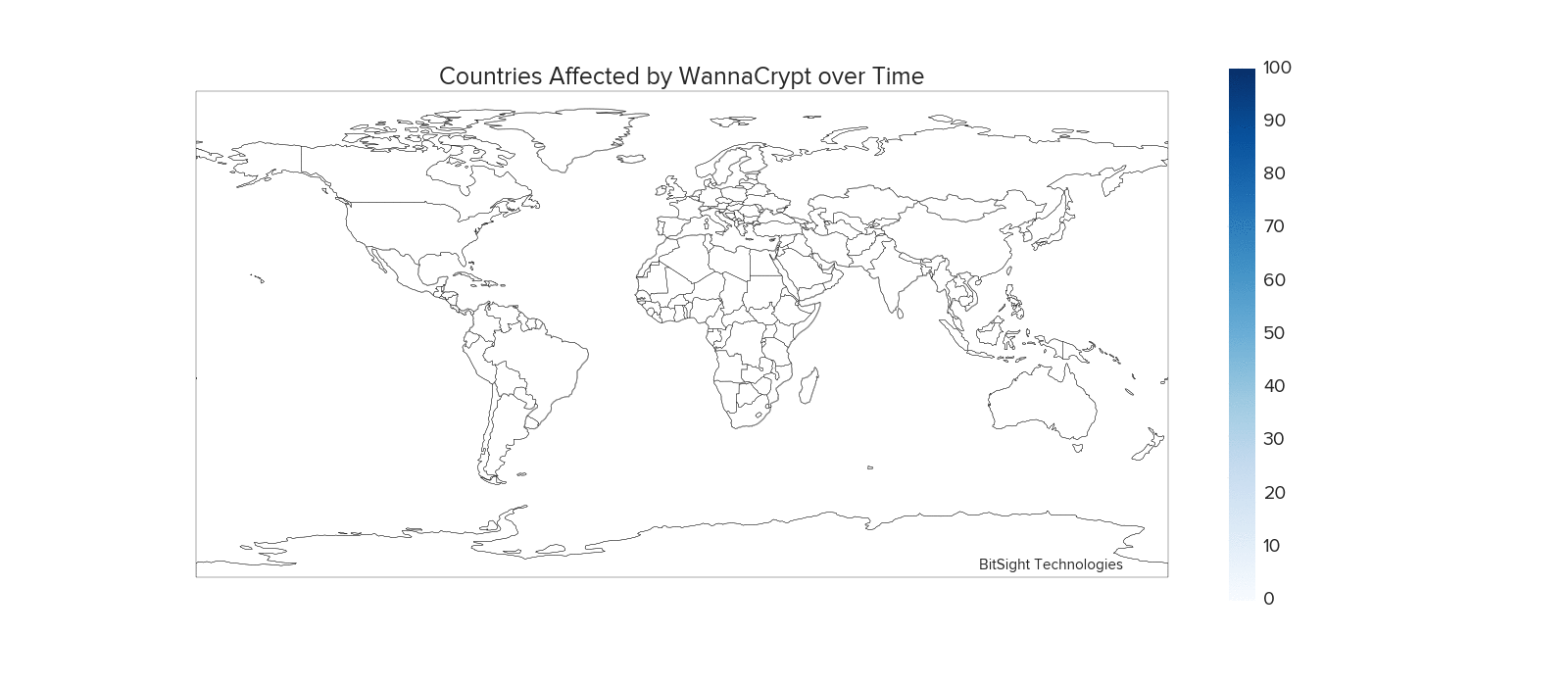
Various countries were impacted at different periods, with China, Russia, the United States, France, UK, Brazil, and Peru having notable periods of a high number of infections compared to other countries.
After the malware has infected a specific machine, it scans for other vulnerable systems both external and internal to the network. Strong concentrations of infections within countries often occur due to the worm making headway by infecting a large number of machines behind a set of IP addresses.
Operating Systems
Data from Kaspersky has shown the majority of infections affected Windows 7 platforms, also validated by our research. When we looked at the set of IP addresses affected by WannaCry in May of 2017, we extracted the operating systems that are typically used on the machines behind those IP addresses. The following graphic shows our data representing the composition of networks affected by WannaCry.
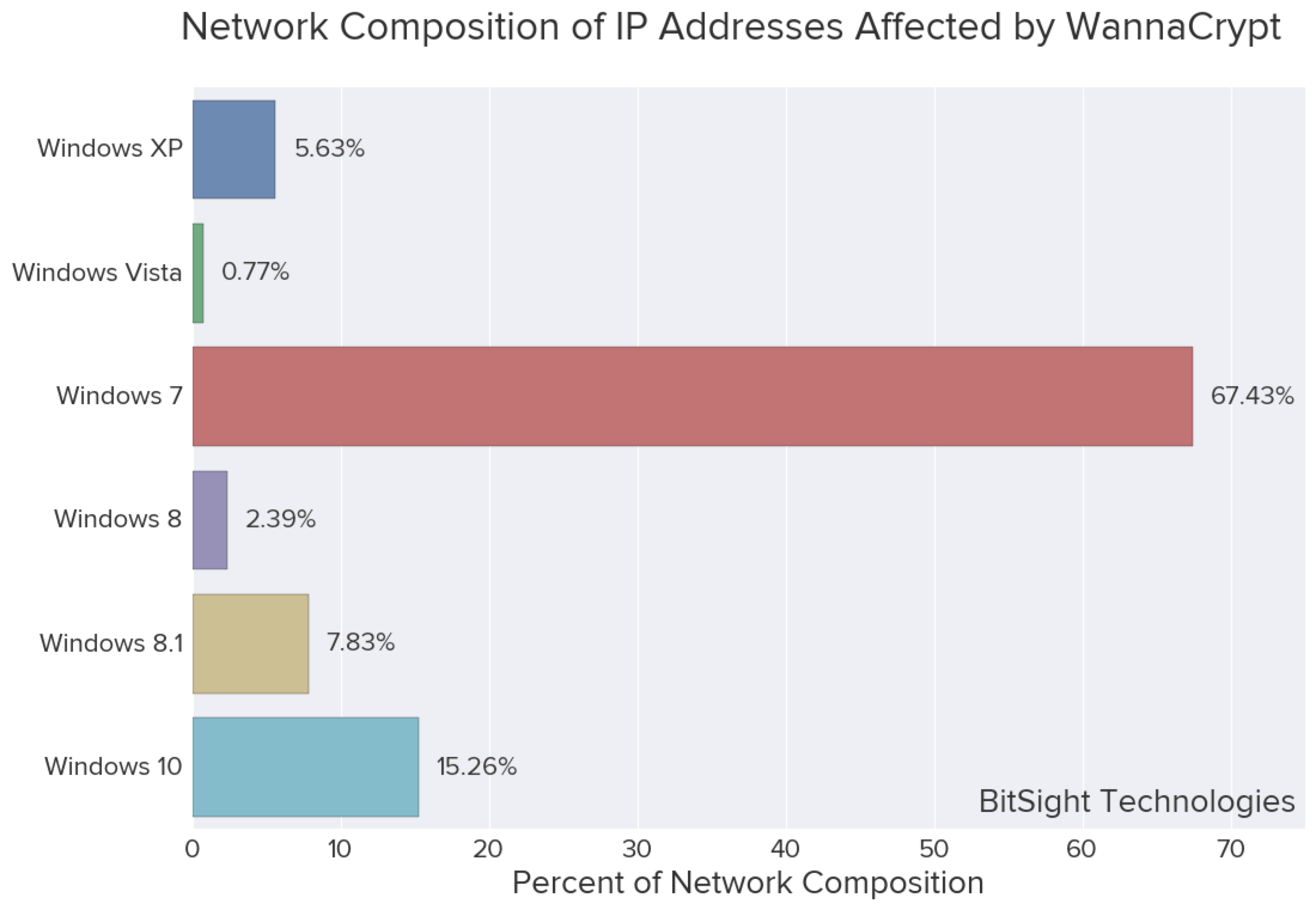
Note: Recall that this is a distribution of operating systems on machines behind IP addresses that were observed to be affected by WannaCry in 2017, and not the individual infected machines. Thus, there might be unaffected machines behind the same IP address as affected machines, and would be present in the distribution above.
There is still ongoing research regarding why Windows 7 is the most popular operating system among victims. It is known that the worm had difficulty infecting Windows XP machines and spreading as it often caused the machine to crash when it attempted to exploit the vulnerabilities. Microsoft has also designed a more seamless automatic update experience for Windows 10 that would have allowed for the MS17-010 patch to be installed on a much larger population of Windows 10 machines compared to older operating systems.
Affected Industries
In an earlier blog post in 2017 describing the ransomware attack, we presented a breakdown of the percent of companies within each industry that have been observed to be affected by WannaCry. In order to observe any differences in industries by size, we can separate this data into three distinct buckets representing the number of employees at these organizations:
- Small = less than 250 employees
- Medium = less than 1,000
- Large = greater than or equal to 1,000
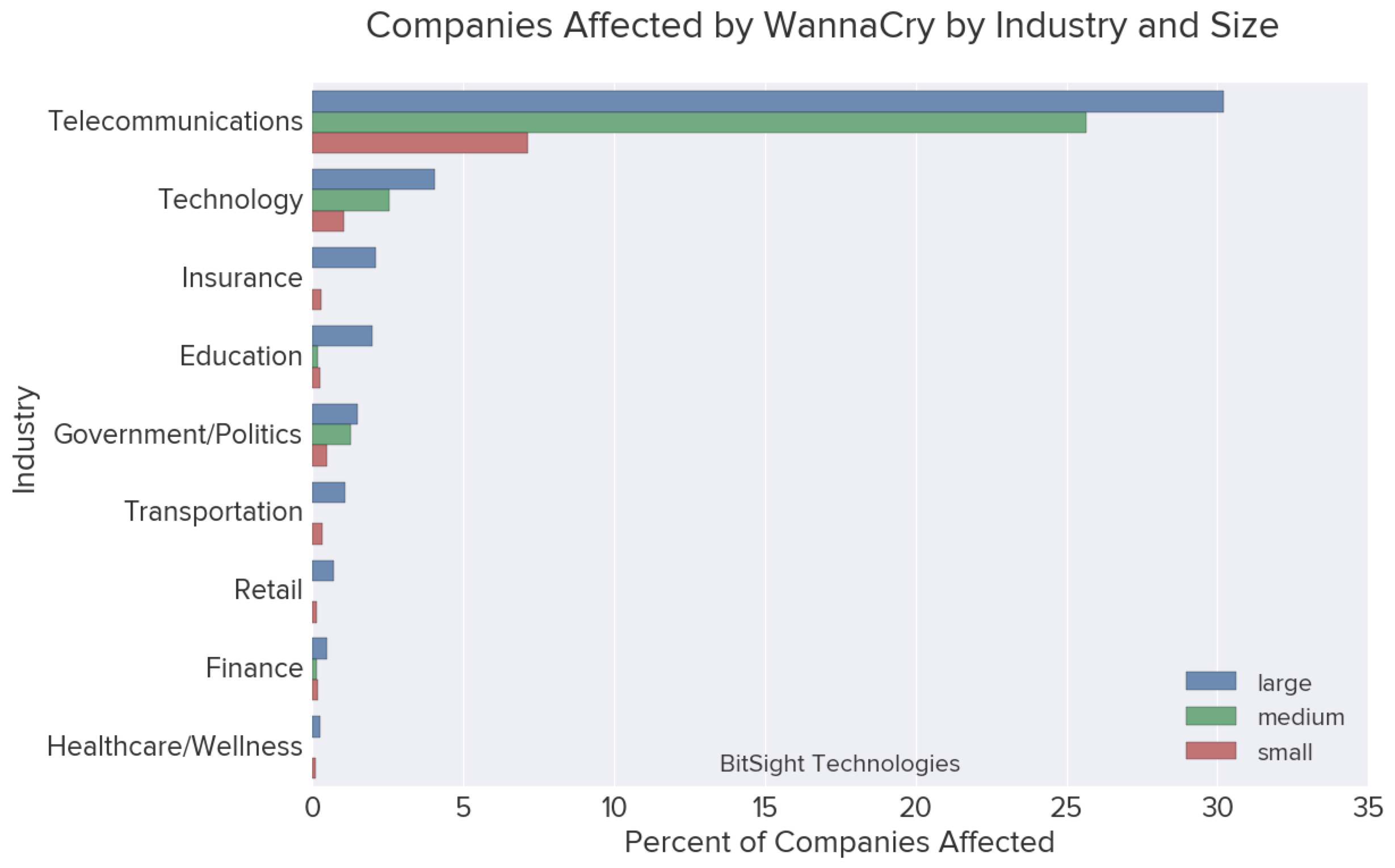
The utilities industry was in 3rd place for large companies affected by WannaCry. Excluding Telecommunications, there were roughly the same number of smaller companies affected as medium-sized organizations.
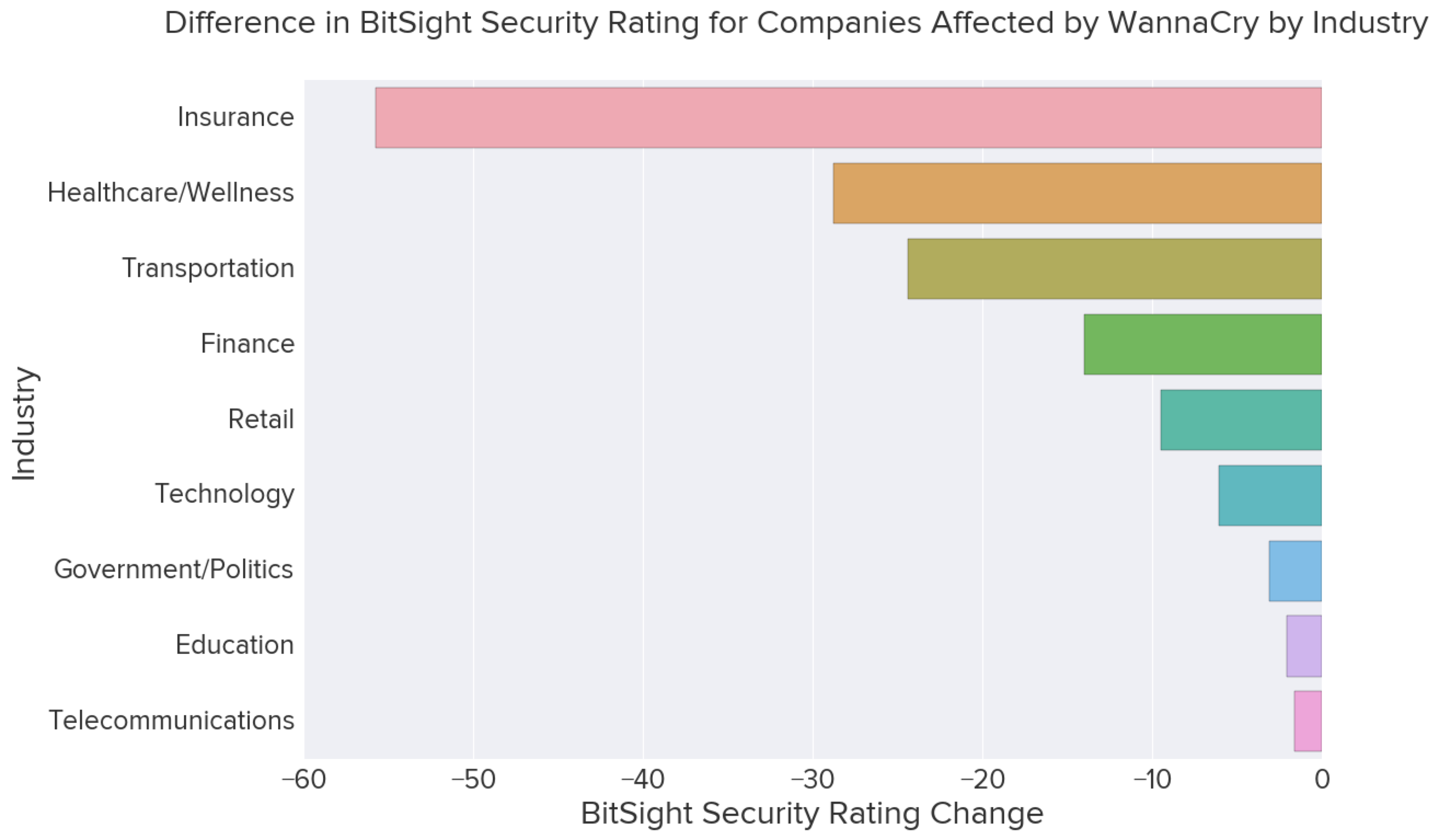
However, another way to view this data is not necessarily by the number of companies affected by industry, but the effect those infections caused by industry. Changes in cybersecurity health can be summarized by Bitsight ratings which take into account vulnerability points across both organizations and overall industries.
This bar chart shows the average change of the Bitsight security rating per company within each industry sector when the attack occurred in May of 2017.
While the Insurance sector ranked fairly low on the percent of companies affected by WannaCry by industry sector, Insurance industry performs better overall in comparison to Education and Telecommunications. Education and Telecommunication companies are usually rife with various forms of malware. On the other hand, industries like Healthcare and Finance perform better overall in comparison, but were also more severely hit.
Ransomware attacks are just as prevalent today as they were in 2017 with the WannaCry ransomware. Now, security leaders also have to monitor for malicious actors targeting the remote workforce. Learn how your organization could be at risk by referencing our Guide to Identifying Unique Work From Home Risks.
This post has been updated as of October 7th 2020.