Get a deeper understanding of the risks and remediation strategies around Known Exploited Vulnerabilities (KEVs) with our comprehensive report. Dive into detailed analyses and gain insights that go beyond the basics—perfect for security leaders aiming to enhance their defense strategies.
Slicing through CISA’s KEV Catalog
Tags:


Who’s most at risk and who’s fastest at the fix
KEV! KEV! KEV! No, you aren’t standing outside a frat house while some college kids encourage their buddy Kevin to finish his beverage. Rather, it’s the sound of people extolling the virtues of the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities(KEV) Catalog. CISA’s KEV Catalog is a list of vulnerabilities known by those crafty Feds to be used in active exploitation, and for those of you who don’t spend much of their free time scrolling through Infosec LinkedIn, Mastodon, and Bluesky, it’s been the subject of a lot of mucking about in the last year or so.
So why is Bitsight getting in the game? Well, because we have a lot of things to say in a brand new, fancy, shiny white paper2. In particular, Bitsight’s global, advanced scanning and detection capabilities provide insight into these actively exploited vulnerabilities that others just can’t touch. Because Bitsight spends most of its resources on the outside looking at the risk surface of various organizations, our view is similar to that of all those ne’er do wells out there trying to breach our perimeter. So when we can detect a KEV at your organization, chances are that attackers can as well.
So what did we see when we used Bitsight’s massive data collection and analysis capabilities? The paper goes into all the down and dirty details, but we’ll give you a few highlights, before you go get your hands dirty.
The KEV catalog is growing
In fact, Bitsight itself added to the KEV Catalog when we found a vulnerability lurking in SLP protocol and being actively exploited in the wild. But how does that growth look overall? Take a look at the interactive graphic below (and maybe poke around a bit.)
After a big burst of additions to the KEV within the first year of creation, we see a trickle of increase over the course of the next few years. Most things in the KEV Catalog have high or critical CVSS Scores, but a few Mediums and even a handful of Lows are mixed in there. Since then, the KEV Catalog has grown at a pace of roughly 17 vulnerabilities a month, or a new one every other day.
KEVs are common
In the paper, we break down exactly which KEVs show up the most, but we can say this: some KEVs are found in as many as 20% of organizations, and that 35% of organizations had a detectable KEV on an externally facing asset in 2023. Moreover, we detected that 20% of organizations had a KEV known to be used in Ransomware. Beyond just the top line numbers, we also find that a typical KEV is 2.7x more likely to be detected in organizations than non-KEVs.
KEVs get fixed faster
Having those KEVs detectable on external assets is one thing, but perhaps more important is how quickly organizations get them fixed. After all, often KEVs are zero days and come as a surprise even to the most diligent of organizations. So how quickly do things get fixed? The answer is, it depends on the vulnerability of course, but KEVs generally get fixed faster than their non-KEV counterparts.
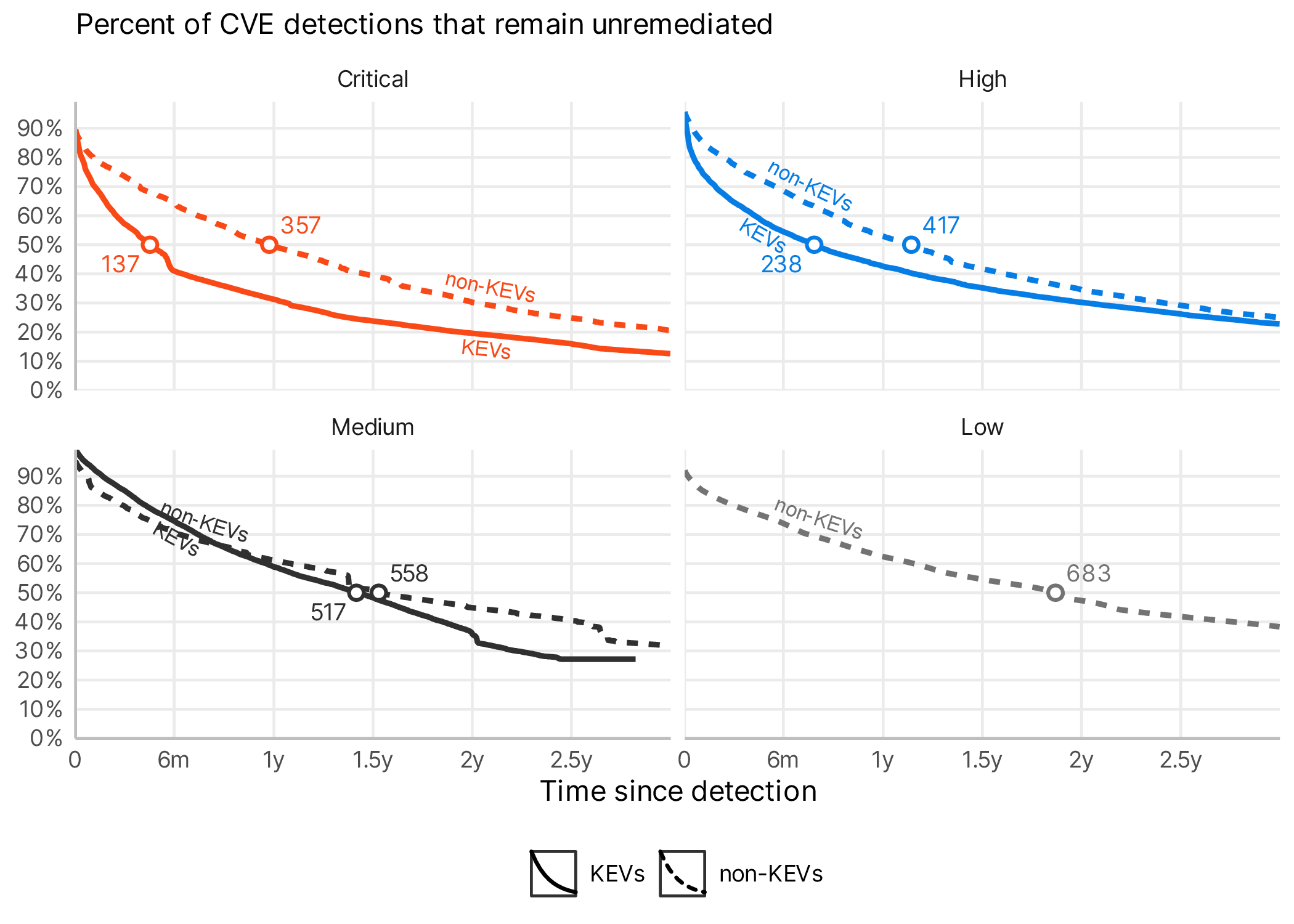
In fact, critical KEVs get fixed 2.5x faster than critical non-KEVs and high severity KEVs get fixed 1.7x faster. This means that folks' ears are definitely perking up when they hear that CISA says “this is serious”. But whose fixing things the fastest? Ah once again we’d like to point you to that nice shiny pdf, and have you get in touch with us to learn what this means for your organization.
1Remember folks, infosec Twitter, I mean X, is dead.
2The author of this blog post understands that the author of the white paper is an especially gifted research scientist. It’s me, I’m both authors.



