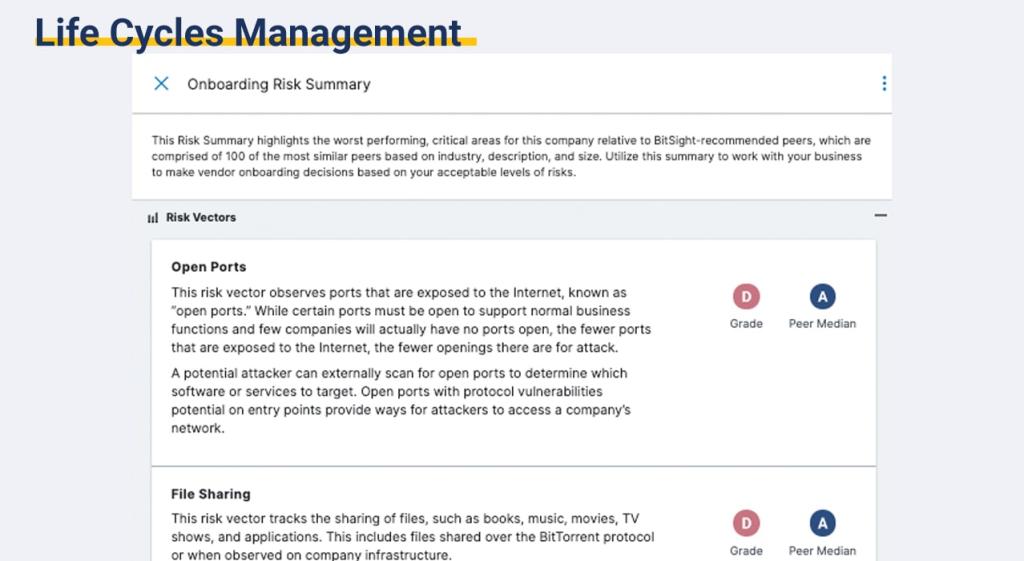
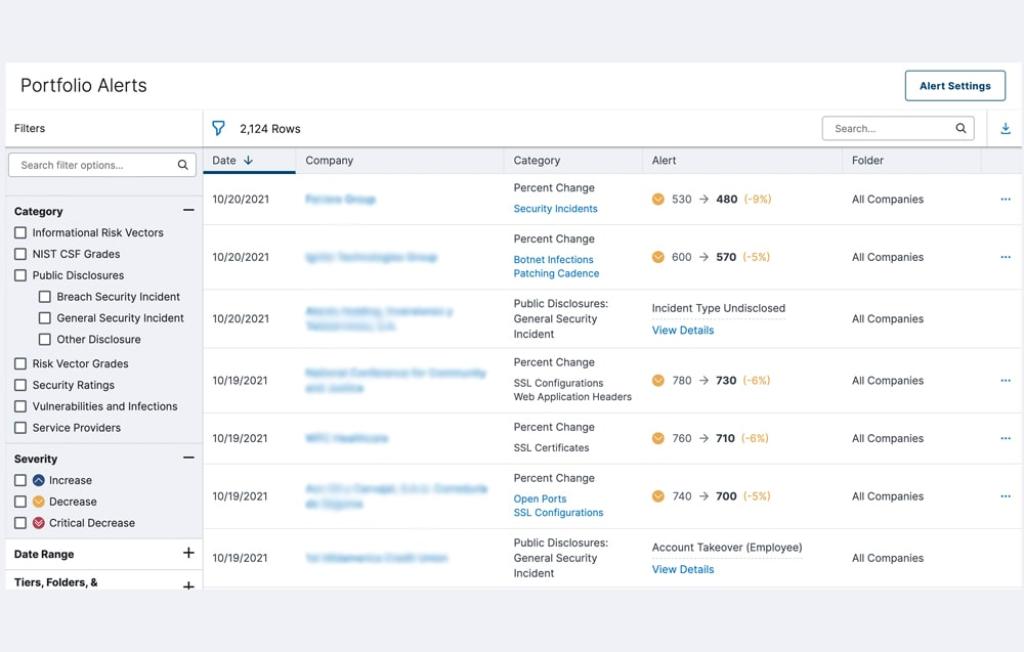
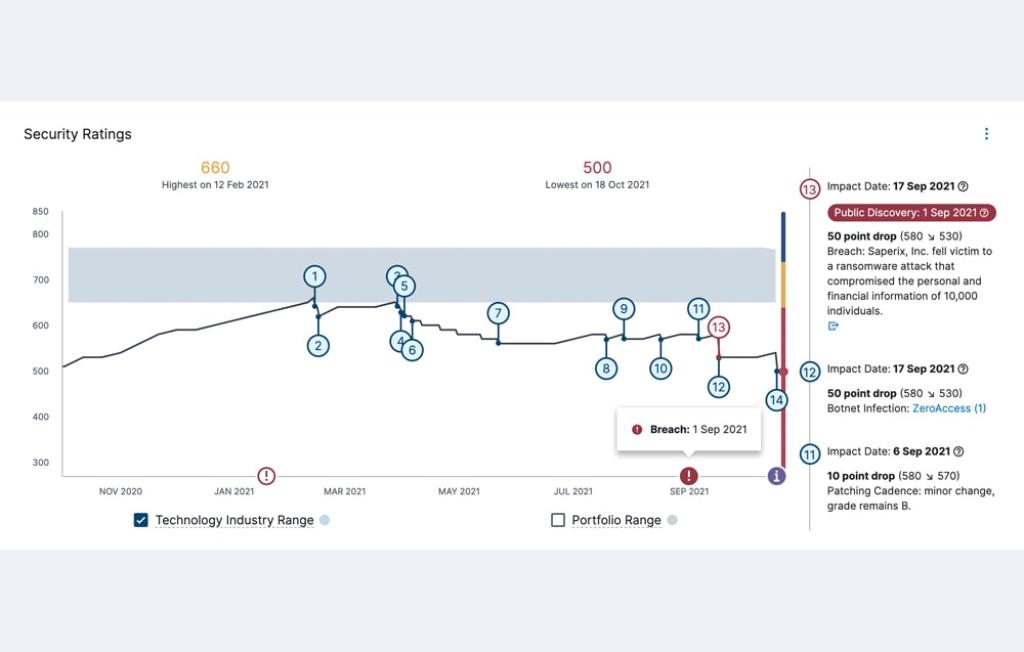
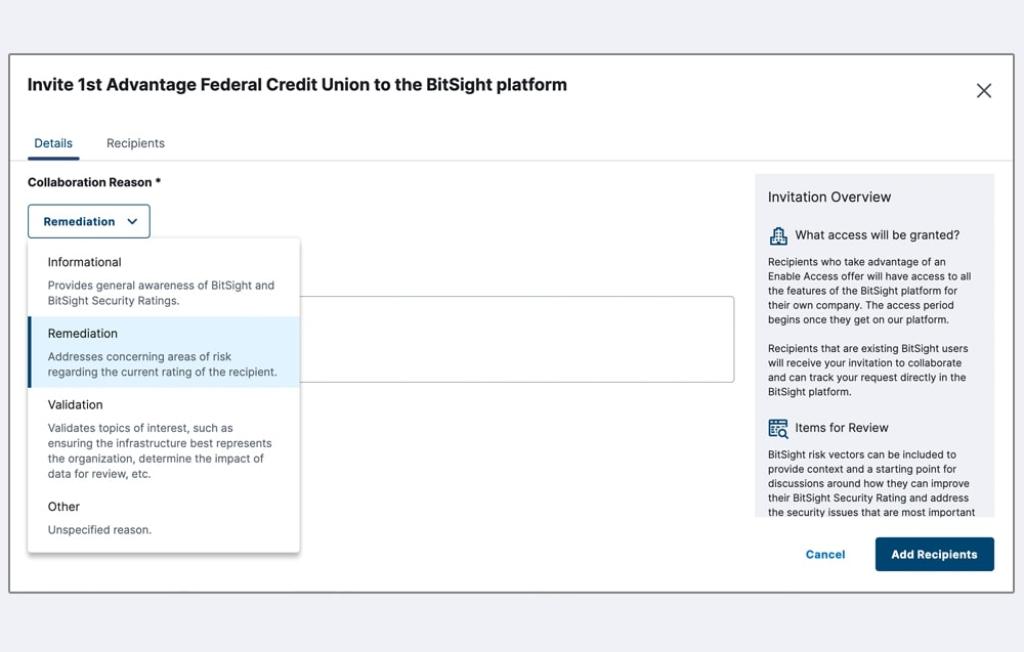
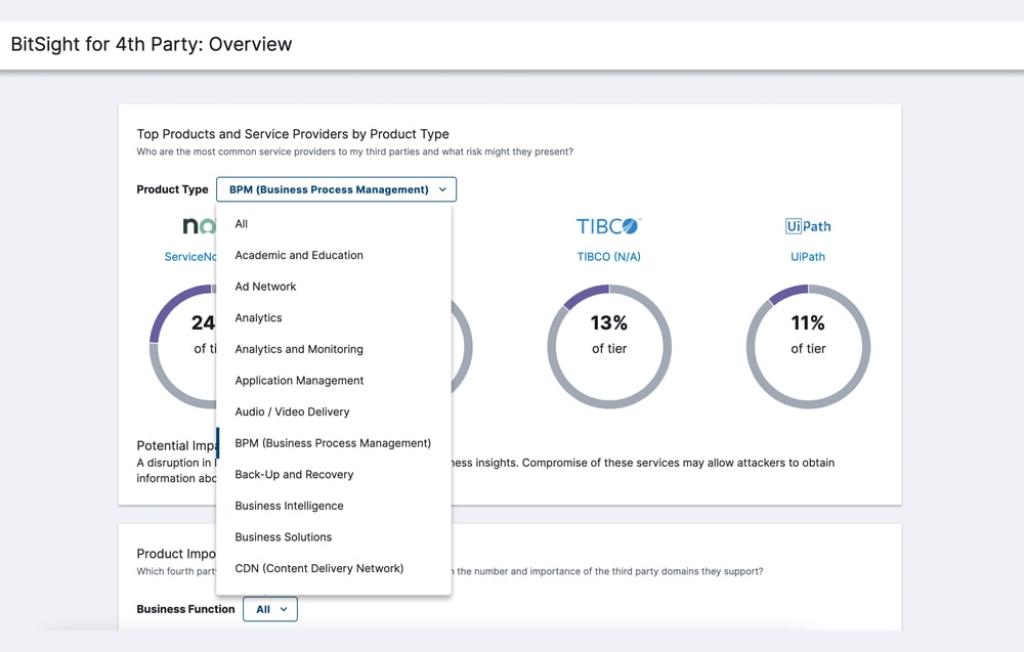
Vendors and third-party partners help your business grow and stay competitive. But they also expose your organization to cyber risk. From the SolarWinds hack to the Target breach, the supply chain can house weak links -- an attack avenue of choice for hackers.
That’s because malicious attackers tend to look for the weakest link in an organization’s security posture. Often, this resides in your company’s interconnected supply chain. When you’re dealing with potentially hundreds of vendors — some who handle sensitive data — third-party and supply chain risk management can be overwhelming, but a necessity to manage.