Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Last week we wrote about how to assess your risk and reduce your exposure when it comes to Shellshock. While all other products and vendors are helping customers discover Shellshock within their own environment, we uniquely help customers understand whether the vulnerability exists within their supply chain. Supply chain oversight is so fundamental that the Federal Financial Institutions Examination Council has already issued a warning to banks regarding their third party service providers, urging them to assess risk and “execute mitigation activities with appropriate urgency.”
The security community is abuzz with the news of the latest vulnerability to sweep the internet. Early yesterday morning, details about the Bash security bug, also called Shellshock, started to emerge, putting companies on high alert about the threat experts are calling “Bigger than Heartbleed.”

There is no denying that cyber security issues have captured headlines over the course of the year. From the highly public Heartbleed bug to major data breaches affecting some of the largest names in business, there has been increased focus on data security. As we have noted in previous posts, in the wake of these events and in the face of new threats, cyber insurance has emerged as a viable option to transfer the risk of financial losses related to data loss. In just the past week a White House official went as far as to say that cyber insurance will be standard for businesses by 2020, just as property or liability insurance is now. But as the cyber insurance market continues to grow, how will large scale breaches affect the industry?

ISACA and the Institute of Internal Auditors (IIA) recently released a report emphasizing the board’s role in overseeing security risk management. In particular, the report mentioned management of third party risk, arguing that boards should ask tougher questions about third party security. According to an IIA survey, only 14 percent of board members said they were actively involved in cyber security oversight. Even though the SEC has asked board members to get involved, 58 percent of board members admit that they should be doing more. If you’ve struggled to get your board to become engaged in your security risk management efforts, particularly related to third party risk, now is the right time to make them aware.

Data breaches at higher education institutions are becoming more and more common, putting them near the top of the list of industries most affected by cyber security risks. Hackers target .EDU networks because they tend to be left wide open for attacks, either because the schools fail to prepare against such intrusions or because network users fall victim to vicious phishing scams. As our latest Bitsight Insights report revealed, university security teams juggle diverse IT infrastructure needs and unique challenges, including BYOD culture and multiple network access points. This leads to a major slump in security performance throughout the school year. So how can universities overcome these challenges?
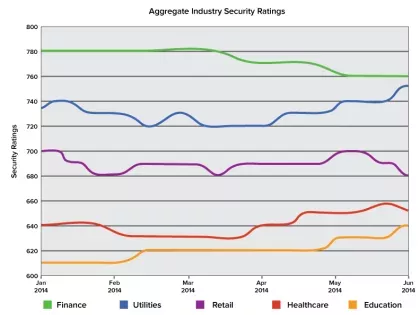
It is no secret that America's colleges and universities hold a wealth of personal and sensitive information that is frequently targeted by cybercriminals, as evidenced by some public data breaches in the past year affecting major universities. Today we at Bitsight published our quarterly Bitsight Insights report that analyzes the security performance of higher education insitutions in America. We conducted a thorough analysis of the largest and most prestigious collegiate athletic conferences in the nation: the ACC, SEC, Pac 12, Big 10, Big 12 and Ivy League. The member schools of these athletic conferences are large to medium sized universities that give a strong representative sample of the higher education industry in the United States, encompassing a student population of 2.25 million and a network space of more than 11 million IP addresses.
By analyzing the aggregate Security Ratings
By analyzing the aggregate Security Ratings

The last couple of years have been tough on higher education systems in terms of cyber security. In 2012, in particular, there was a near-record-high number of data breaches, with nearly two million exposed records reported. The following year saw Maricopa Community College in Arizona experience a data breach that affected 2.4 million people. In 2014, there have already been several high-profile .EDU data breaches. In our latest Bitsight Insights report, we found that many universities are struggling to secure their networks due to unique IT infrastructure requirements and persistent security problems.

In 2011, the SEC issued a set of disclosure guidelines that told companies to disclose any potential cyber risk, possible effects of that risk, as well as the status of internal controls and risk management procedures in place. It was a grand idea, one that had the potential to protect investors and boards by keeping them in the loop when it came to matters of security. Unfortunately, its grand potential wasn’t brought to fruition. The guidance was never updated to account for the growing frequency of security breaches, and companies were failing to report cyber incidents. Now, the SEC is revisiting the issue and considering turning those guidelines into standards so that companies will have to live up to the level of transparency their investors have come to expect.

On July 21, 2014, Brian Krebs (once again) broke the news of a potentially major retail breach. Goodwill Industries and its 165 independent agencies across North America appear to be the most recent victims in the seemingly plagued retail industry.

As executives and corporate boards are increasingly being called upon to act on cyber security issues, security practitioners need new tools to better communicate performance to upper level management. Benchmarking, a tool used by businesses to track performance, can (and should) be used to better communicate and understand security posture.

It took a long time for the CISO role to emerge in corporate America (and maybe 25% of large enterprises have one), so it will be quite a while before it becomes a consistent board seat. In the meantime, corporate boards are made up of current and former CEOs, CIOs & CFOs, academia and distinguished public servants from civilian and military backgrounds. I believe they are all too aware of the implication of cybersecurity risk. Like many senior executives, boards have recently had a crash course in the impact of security breaches. Either because they have witnessed them first hand….or from ‘a safe distance’ as competitors and peers have struggled through cyber attacks and loss disclosures. But there is no existing framework for discussing cybersecurity risk among a corporate board, certainly nothing that equates to their existing framework for discussing growth, profitability, legal exposure, supply chain, M&A, HR best practices, geopolitical risk etc. For those perpetual board meeting topics there is a consistent push for internal data and instrumentation that can be compared and benchmarked with a peer group, an industry or a competitor.
For 'the practice' of board oversight to extend to cybersecurity risk, those same benchmarks must exist. Without objective comparison between peer/competitor/industry, how can the experience and advice of your celebrated academic, retired CEO, distinguished public servant or maverick CIO have any context? How can measurement be put in place?
Mr. Aguilar is on the right track. Boards must start taking responsibility for the cybersecurity of their companies. If not, there will likely be financial and reputational repercussions for board members that fail to place this issue as a critical priority in retaining and growing the value of a company. Yet, while the time for board level discussions on cyber security has come, it is also the time for new innovative solutions to enable this practice. This is where Security Ratings come in.
For 'the practice' of board oversight to extend to cybersecurity risk, those same benchmarks must exist. Without objective comparison between peer/competitor/industry, how can the experience and advice of your celebrated academic, retired CEO, distinguished public servant or maverick CIO have any context? How can measurement be put in place?
Mr. Aguilar is on the right track. Boards must start taking responsibility for the cybersecurity of their companies. If not, there will likely be financial and reputational repercussions for board members that fail to place this issue as a critical priority in retaining and growing the value of a company. Yet, while the time for board level discussions on cyber security has come, it is also the time for new innovative solutions to enable this practice. This is where Security Ratings come in.

In a previous blog post, we outlined federal initiatives to pass a data breach notification law that would simplify the current myriad of state regulations. In the wake of the Target and Neiman Marcus data breaches, legislators and government officials called for a national data breach notification standard. While bills have been introduced, little action has been taken beyond Senate or House subcommittee hearings. While high-profile breaches that brought this issue into the conciousness of the American public and government, the need for transparency is even more pressing due to the high volume of unreported breaches: Our own analysis found that just in our home state of Massachusetts, 1 million residents had their PII compromised from healthcare breaches during 2007-2011. Yet, just because there has been little movement in the US federal government does not mean data breach notification has been a stagnant issue in other countries and on the state level. In this post, we are going to round up some interesting legislative initiatives happening around the globe and in US state governments.

Companies are spending more and more on IT security. A recent report by Canalys found that the worldwide IT security market will grow 6.6% annually, becoming a $30.1 billion dollar industry by 2017. This increase in spending may have something to do with the heightened consequences of data breaches and security events. Another recent study, this one from the Ponemon Institute, found average data breach costs to be a lofty $3.5 million. But, as companies spend more and more money on IT security products and services, how can they verify that their overall security is improving?

In his talk “CISOs Talking SMAC (Social, Mobile, Analytics, Cloud)”, Jim Routh, CISO at Aetna recounted a lunch conversation that he shared with eight recently hired CISOs. Through the course of the lunch discussion, the CISOs ascertained the following three facts: 1) Each CISO was interviewed for their current position by the CEO, 2) they were all being very well compensated, and 3) the lowest amount of budget increase was double.
Routh’s lunch time anecdote makes it clear that the role of the CISO is evolving. The elevated importance of the CISO within the enterprise shows an increased enterprise awareness and focus on information security risk, but it also speaks to the new nature of the CISO’s role. Traditionally, the CISO was more a of a “back-office” manager focused on network and security operations. The role has evolved. The CISO is in many ways on par with other “C-level” executives. The new CISO is customer-facing and revenue-generating.
Security has been historically classified as a business expense with
Routh’s lunch time anecdote makes it clear that the role of the CISO is evolving. The elevated importance of the CISO within the enterprise shows an increased enterprise awareness and focus on information security risk, but it also speaks to the new nature of the CISO’s role. Traditionally, the CISO was more a of a “back-office” manager focused on network and security operations. The role has evolved. The CISO is in many ways on par with other “C-level” executives. The new CISO is customer-facing and revenue-generating.
Security has been historically classified as a business expense with

As a result of their major data breach late last year, Target has undergone a major house-cleaning to signify to the market just how seriously they are taking cyber security.