Request your free Security Rating Snapshot to find the gaps in your security program and how you compare to others in your industry.
Easy Security Wins: How Patching and Software Updates Impact Your Cybersecurity
Tags:

As companies continue to try and manage the massive changes to work driven by COVID-19, security teams have faced immense pressure to rise to the challenge and keep companies secure. In the face of the large scale shift to work from home, expansion of the vendor ecosystem and digital attack surface, and disruptions to operations, it’s vital that security teams focus their efforts on areas of risk concentration.
Focusing on reducing risk can often mean going back to fundamentals. There are typically a lot of surprising “gimmes” lurking with your ecosystem, low hanging fruit that is low effort to resolve but can have a large impact on reducing the overall cyber risk your organization faces.
Recently, Bitsight took a look at the performance of a few of our most impactful risk vectors to see how they correlate with breach.
Bitsight Risk Vectors
Methodology
Unlike a security rating, Bitsight grades risk vectors-- the externally observable factors that are indicators of an organization’s security hygiene-- on an A-F scale. Generally, the lower the grade, the greater the likelihood of that factor being a vector for a security breach. Periodically, we compute the probability of a company experiencing one or more data breaches if they have a given grade for the risk vector in question.
An “A” grade is typically assigned a breach likelihood of 1, while a lower grades reflect the increased likelihood of the vector resulting in a breach. So for example, an organization with a lower grade in User Behavior is 3x more likely to suffer a breach via that vector than a company with an A.
Here are how some of the some of the most important 2020 risk factors break down:
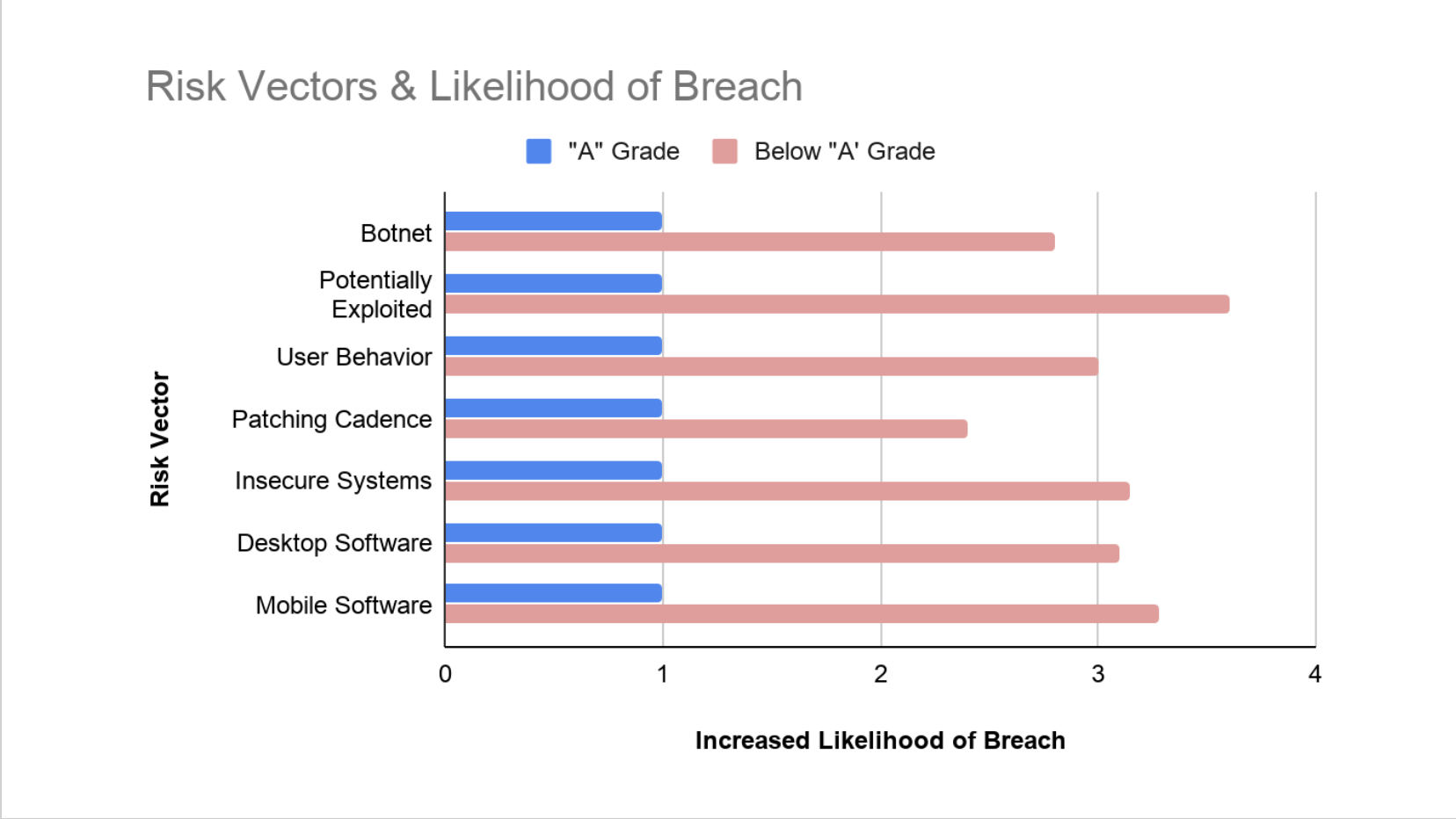
Some of these are clearly more serious issues than others, and the remediation can be complex for Botnet infections, Potentially Exploited systems and User Behavior. However, looking further down the list we can see that simple things like regularly patching systems and updating desktop and mobile software can have a huge impact on the risk an organization faces. These are low hanging fruits that usually require few resources to remediate and deliver easy wins to reduce risk.
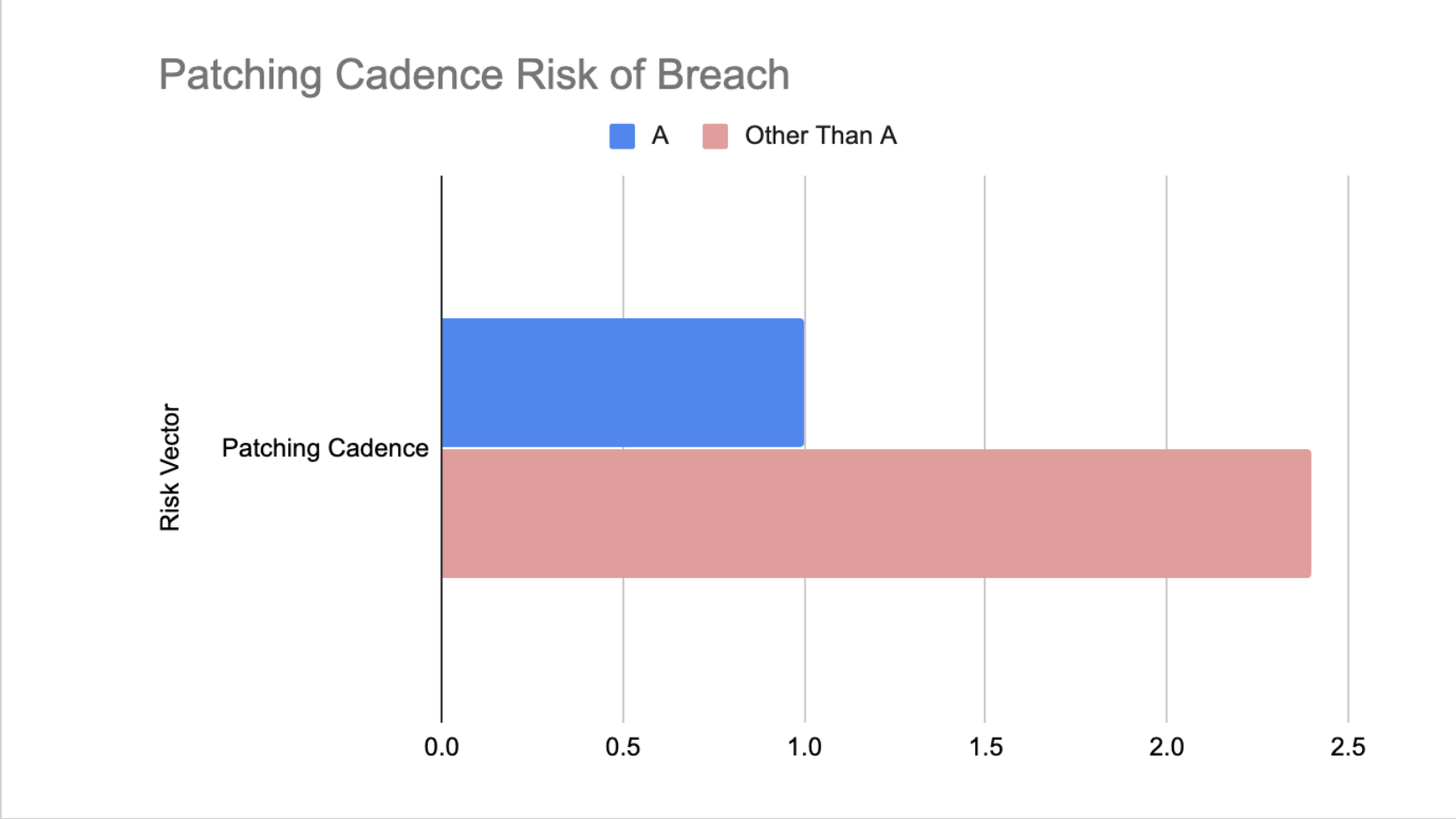
Why Patching Matters
Patching is one of the easiest things security teams can do, yet one that carries outsized risk if left undone. Patching typically refers to installing software updates to address known vulnerabilities and security flaws in endpoints and on-premise systems. As seen in the graph above, failing to patch makes your organization at least 2x more likely to suffer a breach via an unpatched system. While some software patches are certainly routine and may address functionality issues, others remediate major vulnerabilities such as BlueKeep or DoubleKill that can lead to major business disruption.
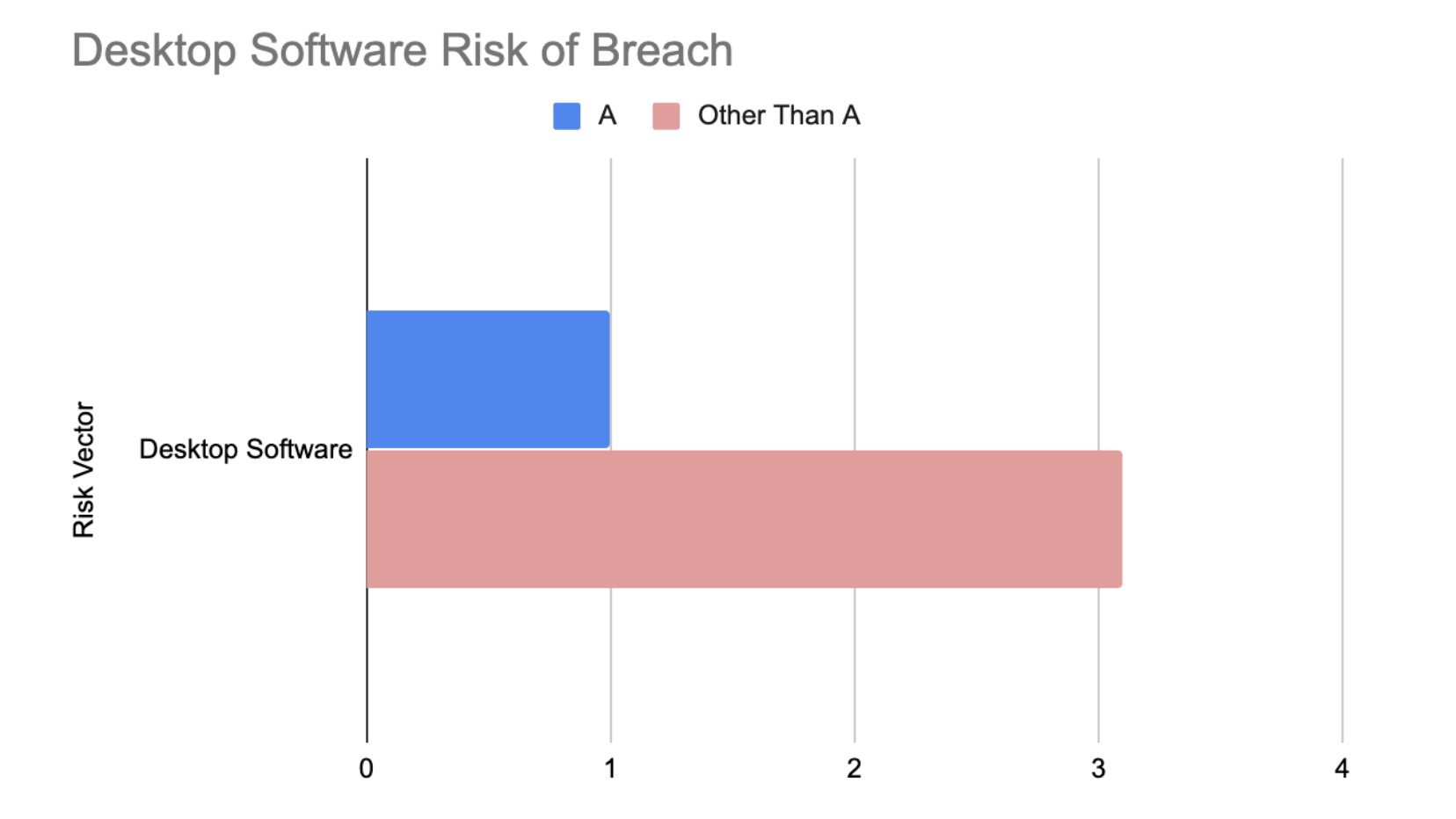
Why Desktop Software Matters
Odds are most of the end users in your organization are not exactly diligent about updating their software. It’s all too easy for most of us to click “Remind Me Tomorrow” when the reminder pops up during a busy work day. However this can pose a substantial risk to the business, as we can see any grade below an “A” is at least 3x more likely to suffer a breach. And it isn’t only routine updates that can pose a risk. As recently as January 2020, Bitsight research showed that 70% of organizations were still using Windows 7, an operating system no longer supported by Microsoft, and therefore no longer receiving security updates. Ensuring that all endpoints are up to date is another must, but also an easy “win” for security teams.
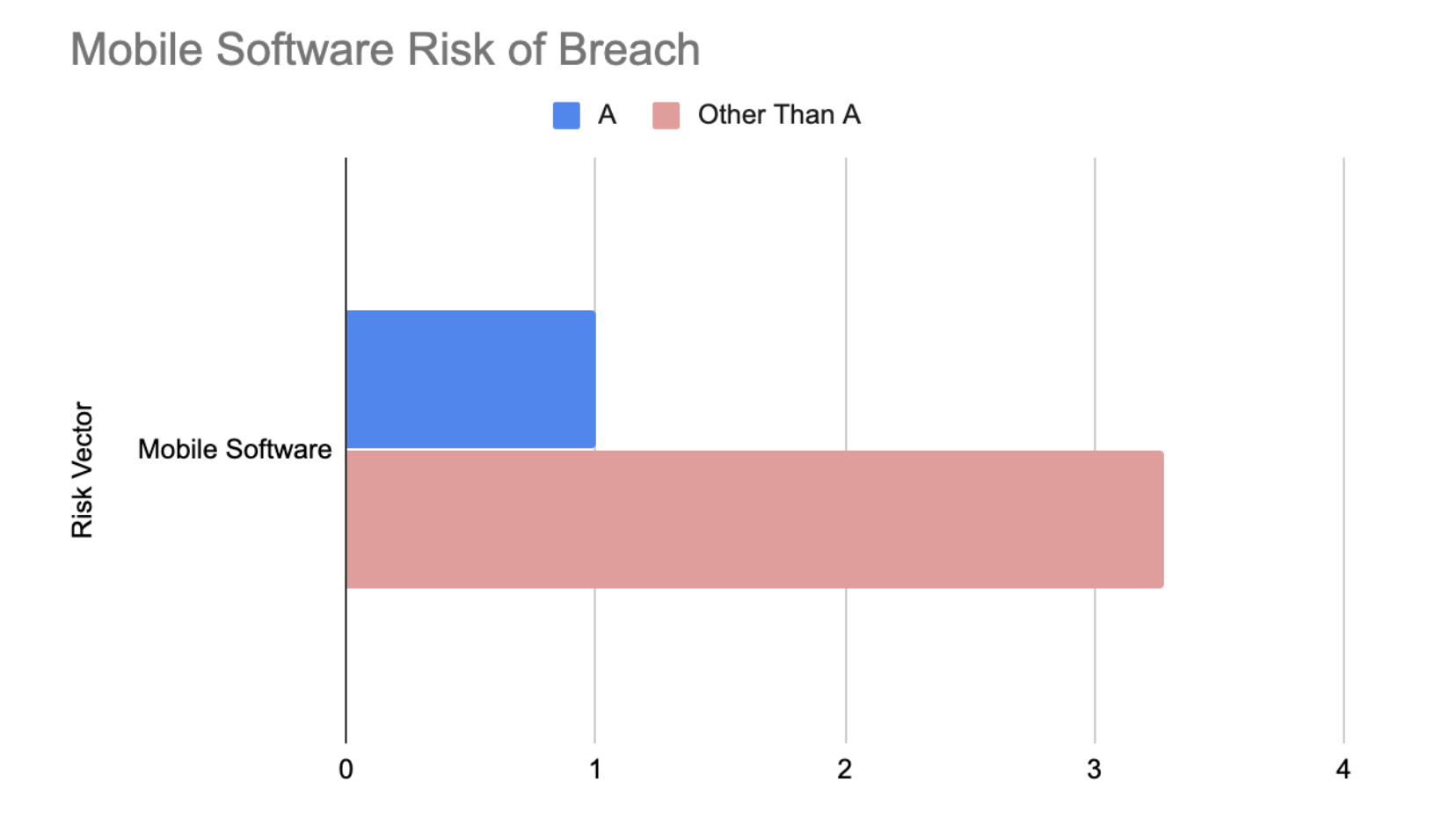
Why Mobile Software Matters
Unlike desktops, most users don’t really know when their mobile phones update or what version of the operating system they are on. However, since mobile phones are often BYOD, yet connect to the office network via WiFi, or have apps or cloud storage with access to potentially sensitive information, it’s imperative that mobile software be fully up to date. Interestingly, Mobile Software is one of the most dangerous of these risk vectors, since having any grade below an A correlated to a 3.28x increased likelihood of breach. Given the ubiquity of mobile devices, it is imperative that security teams develop sound policies and procedures to ensure the software on all corporate associated mobile devices is up to date.
What Can You Do?
Cyber criminals are constantly looking for weaknesses in your network. Continuously monitoring your own and your vendors’ security ratings and benchmarking your performance against your industry can give you the necessary insight to bolster your network’s security. Below are some best practices to consider:
- Identify Unpatched Systems: Unpatched systems can easily fly under the radar, especially on globally distributed organizations or those with many on-premise systems. It is important that your security team quickly identify and unpatched systems and update them immediately.
- Update Desktop and Mobile Software: Sometimes easier said than done (testing and migrating to new operating systems can be one of the biggest IT projects), but ensuring desktop and mobile software is up-to-date and ensuring all endpoints have the latest software installed can have a huge impact. Ensure your security team is monitoring endpoints for out of date software, and consider looking at network policies that take software versions into account.
- Continuously monitor your vendors’ cybersecurity posture: The security landscape is constantly evolving. To stay ahead of cyber threats, security and risk management teams should continuously monitor their vendors’ security performance and ensure that they identify changes in the security ratings, taking appropriate steps to remediate any issues that appear.
- Benchmark your performance against the industry: Security should not be measured in a vacuum. Organizations should establish benchmarks and compare their performance to their competitors or their industry. This approach helps facilitate cybersecurity discussions with the Board of Directors and other business line leaders across the company.