From safeguarding intellectual property to managing sprawling digital ecosystems—get the insights and tools you need to protect your creations, ensure business continuity, and maintain the trust of your users and stakeholders.
Technology Cybersecurity
The cost of a data breach in the technology industry.
As a technology provider, customers trust you to help them create business applications, move to the cloud, and secure their systems and data. Your business can’t afford to be the target of a cyberattack.
Source: IBM Cost of a Data Breach 2023
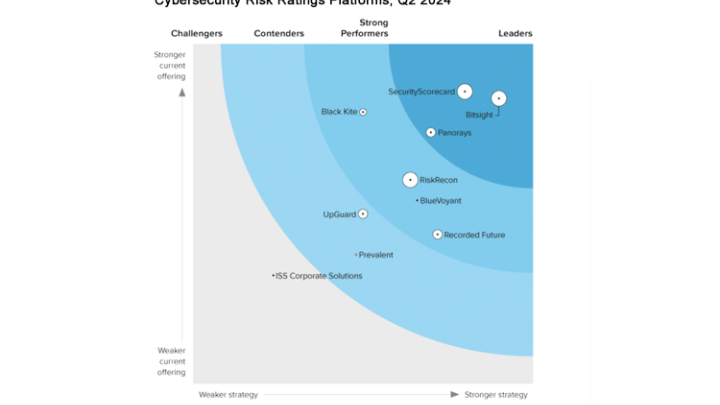
Why Bitsight for Technology Organizations
As a technology provider, customers trust you to help them create business applications, move to the cloud, and secure their systems and data. Your business can’t afford to be the target of a cyberattack.
Gain Continuous and Real-Time Insight into Cyber Risk.
Discover and continuously monitor the security posture of your entire digital ecosystem—on-premises, in the cloud, and across geographies. Compare security performance to your peers and optimize your strategies to outpace cyber threats.
Expose and Mitigate Third-Party Supply Chain Risk.
Vet the security performance of your vendors, partners, and suppliers without the need for time-consuming and unscalable point-in-time questionnaires. Continuously monitor their security posture at scale—from onboarding through the life of the contract.

Being able to show our board, leaders, and even customers and partners how Veracode is performing over time and relative to others in our space is a powerful tool for communicating our commitment to security excellence, and has also become a terrific competitive differentiator."
Featured Resources

A Critical Guide to Closing Your Exposure Management Gaps