- The Bitsight Investigative Platform detected attacks against 645 organizations in March 2025, in comparison with 793 in February.
- The group Babuk who came back to action with a new website in January 2025 was responsible for the highest number of ransomware attacks this month.
- Babuk, first observed in January 2021, is a sophisticated Ransomware-as-a-Service (RaaS) malware targeting major enterprises. It is compiled for multiple platforms, including Windows and ARM for Linux. Babuk has been linked to sectors such as healthcare, manufacturing, and critical infrastructure, with notable incidents in the United States, France, and the United Kingdom. The group created a new website in January 2025.
March 2025
Threat Intelligence Report

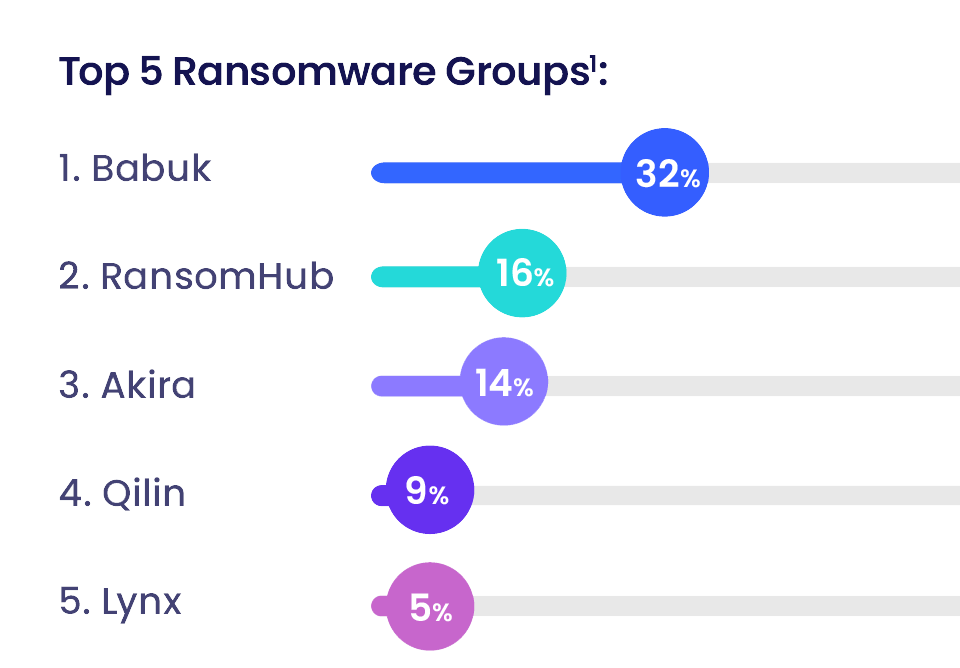
1The listed groups above accounted for 76% of all ransomware attacks among the top 10 operations in March 2025. The other five groups in the top 10 consisted of INC Ransom (6%), Clop (5%), Play (5%), Medusa (4%), and KillSecurity (4%). |
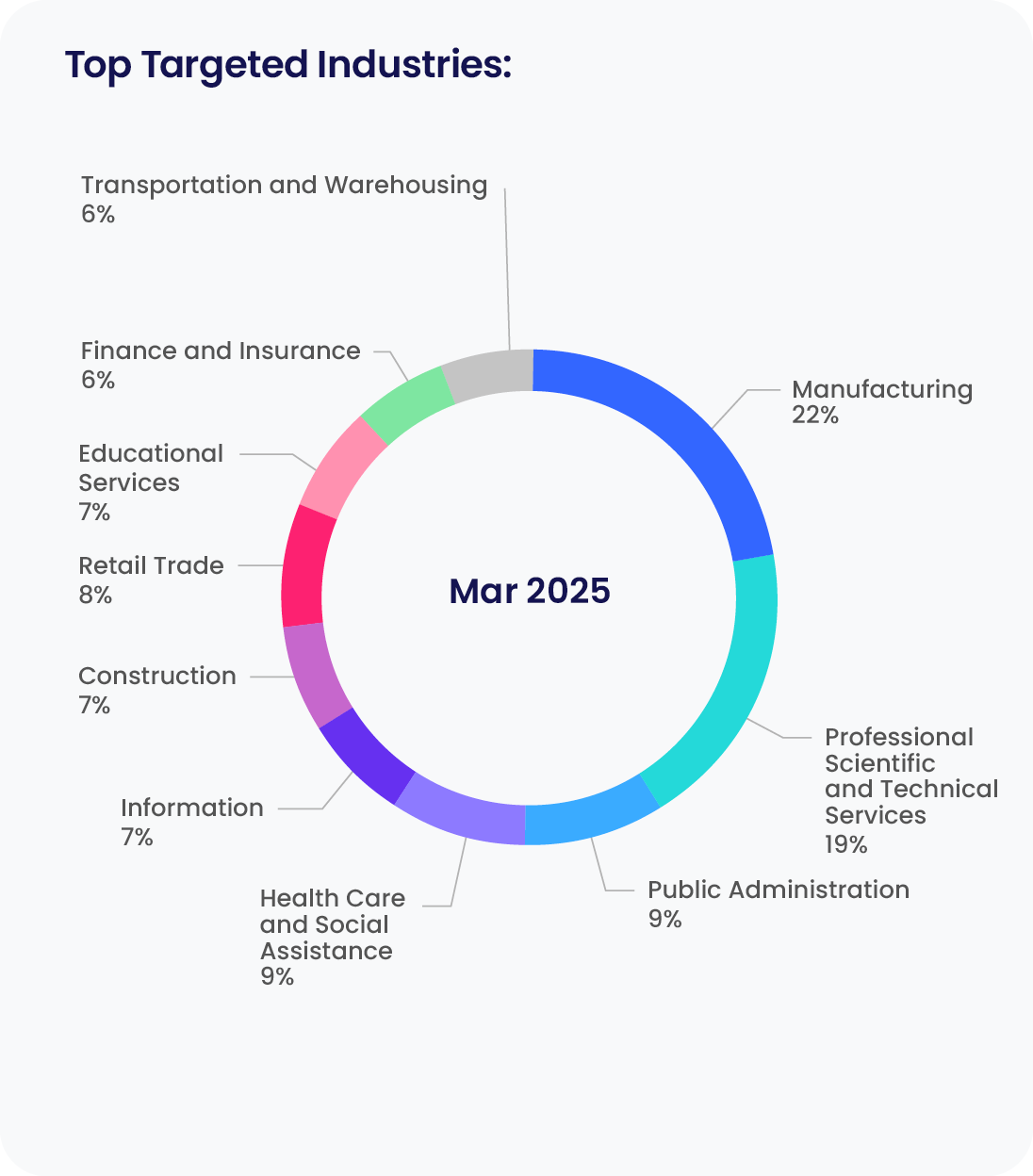
|
March 2025
Trending topics of the month

Belsen Group
The Belsen Group became publicly known in January 2025, after exploiting the CVE-2022-40684 vulnerability in Fortinet devices to compromise over 15,000 FortiGate firewalls, releasing detailed configurations and plaintext VPN credentials.
The group has been involved in multiple attacks across various sectors, including construction, manufacturing, and finance, targeting companies worldwide.
Notable incidents include attacks on a building materials company in the UK and a manufacturing company in North Africa, with ransom demands ranging from $10,000 to $20,000.
Top 3 Vulnerabilities in March
Top CVEs of the month based on Bitsight Data Mechanisms
The Dynamic Vulnerability Exploit (DVE) Module score reflects the probability of a vulnerability being exploited by malicious actors over the course of 90 days.

An Analysis of the Top Mentioned Malware in March
Lumma Malware
In March 2025, Lumma malware had the highest number of mentions in the underground sources collected by the Bitsight Investigative Portal.
Lumma Stealer (aka LummaC2) is an information-stealing malware that primarily targets cryptocurrency wallets and two-factor authentication (2FA) browser extensions. It is written in C language and has been available through a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least August 2022.
The malware is believed to have been developed by the threat actor “Shamel”, who goes by the alias “Lumma” in some of the Russian cybercrime forums. Lumma Stealer steals sensitive information from the victim’s device, including user credentials, system details, browser data, and extensions.
Lumma Stealer has been distributed through various channels, including YouTube videos promoting cracked software. The malware is primarily designed for the Windows platform.
The credentials obtained from the Lumma malware are partially being sold in Russian Market, an automated logs marketplace where threat actors can purchase the stolen credentials from various malware.

Spotlight on a Threat Actor
rose_____
rose_____ is an active member of BreachForums, an online forum and marketplace specializing in the exchange or advertisement of stolen databases. Throughout March 2025, rose_____ published 31 posts or replies. rose_____ primarily posts in English, and made headlines when he advertised the hacked Oracle servers data and company names for sale in BreachForums on March 20, 2025. The leak allegedly includes ±6 million user records and over 140,000 companies allegedly affected from the leak. rose_____ continues the conversation and interest in the leak, offering a sample of 10,000 rows from the database to interested parties.

APTs During the Month of March
Lotus Blossom
Advanced Persistent Threat groups are nation state or state- sponsored hacking groups. They usually remain undetected for an extended period and gain unauthorized access to networks. APT Lotus Blossom (aka Lotus Panda, Spring Dragon, Bronze Elgin, Billbug, ST Group, BitterBug, RADIUM, and Raspberry Typhoon) is a threat group primarily targeting nations surrounding the South China Sea. They focus on government ministries, military entities, and corporate entities connected to critical infrastructure, particularly telecoms.
Their activities include intelligence collection and malware execution. Lotus Blossom has been active since at least 2015 and has targeted government and military organizations in Southeast Asia.
In March 2025, news reports reported the group started targeting government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with updated versions of a known backdoor called Sagerunex.
Sagerunex is a fairly resilient backdoor, targeting Windows operating systems.