Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

I received the following questions from an inquisitive undergraduate student eager to learn more about Bitsight and security ratings. He posed excellent and insightful questions, and I thought that I would share our exchange in case others might be wanting to ask the same questions. Thanks, Nick!

The last few weeks have been a whirlwind of activities here at Bitsight! Between attending and speaking at RSA, participating in the latest Verizon DBIR report, preparing for our session at FS-ISAC, announcing our new partnership with AIG, and being featured as a vendor risk management solution in the Wall Street Journal, we were happy to see the second quarter off to such an exciting start. And then we got even more good news!

Today Bitsight published our most recent Bitsight Insights report, Beware the Botnets; Botnets Correlated to a Higher Likelihood of a Significant Breach. Within this report Bitsight has identified a solid correlation between botnet infections and publicly disclosed breaches. To arrive at this finding, Bitsight leveraged botnet grades that are available to all customers in the Security Ratings platform. These letter grades, which are available for a wide range of risk vectors, provide insight into a company’s performance relative to others. These grades also take into account factors such as frequency, severity, and duration (for events) as well as record quality, evaluated based on industry-standard criteria (for diligence).

In recent years, the US government has become a leading advocate for continuous monitoring of security threats and vulnerabilities. But how effectively are departments and agencies in implementing these programs? And how do we measure success?

Bitsight has released new capabilities and features in the Bitsight Security Ratings portal to widen the data breadth offered to customers and give more detailed, granular performance analytics on specific risk vectors. These changes are available to all enterprise, team, and individual tier customers today.

Third party breaches have become a common occurrence in the last year. From Target to Home Depot and Goodwill, major organizations have been compromised from vulnerabilities present in their extended network ecosystems. Compounding fears surrounding third party vulnerabilities, the last year has also seen no less than three major security flaws affecting basic internet protocols. The first two, Heartbleed and Bash, grabbed media headlines and left businesses scrambling to ensure they weren't left vulnerable. Just this week, another major security flaw dubbed Poodle was uncovered by security researchers. This bug affects SSL v3, a widely used protocol to secure communications over the internet. With growing concern about third party security and the seemingly neverending revelations of internet bugs, organizations are left wondering how they can better gain visibility into the vulnerability of their third parties when it comes to basic configuration hygiene.

Last week we wrote about how to assess your risk and reduce your exposure when it comes to Shellshock. While all other products and vendors are helping customers discover Shellshock within their own environment, we uniquely help customers understand whether the vulnerability exists within their supply chain. Supply chain oversight is so fundamental that the Federal Financial Institutions Examination Council has already issued a warning to banks regarding their third party service providers, urging them to assess risk and “execute mitigation activities with appropriate urgency.”
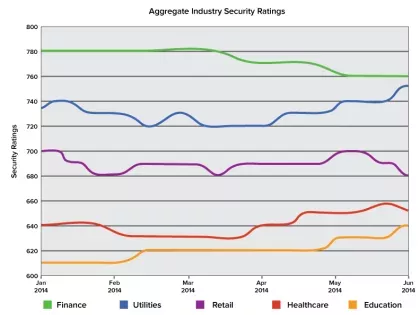
It is no secret that America's colleges and universities hold a wealth of personal and sensitive information that is frequently targeted by cybercriminals, as evidenced by some public data breaches in the past year affecting major universities. Today we at Bitsight published our quarterly Bitsight Insights report that analyzes the security performance of higher education insitutions in America. We conducted a thorough analysis of the largest and most prestigious collegiate athletic conferences in the nation: the ACC, SEC, Pac 12, Big 10, Big 12 and Ivy League. The member schools of these athletic conferences are large to medium sized universities that give a strong representative sample of the higher education industry in the United States, encompassing a student population of 2.25 million and a network space of more than 11 million IP addresses.
By analyzing the aggregate Security Ratings
By analyzing the aggregate Security Ratings

In his talk “CISOs Talking SMAC (Social, Mobile, Analytics, Cloud)”, Jim Routh, CISO at Aetna recounted a lunch conversation that he shared with eight recently hired CISOs. Through the course of the lunch discussion, the CISOs ascertained the following three facts: 1) Each CISO was interviewed for their current position by the CEO, 2) they were all being very well compensated, and 3) the lowest amount of budget increase was double.
Routh’s lunch time anecdote makes it clear that the role of the CISO is evolving. The elevated importance of the CISO within the enterprise shows an increased enterprise awareness and focus on information security risk, but it also speaks to the new nature of the CISO’s role. Traditionally, the CISO was more a of a “back-office” manager focused on network and security operations. The role has evolved. The CISO is in many ways on par with other “C-level” executives. The new CISO is customer-facing and revenue-generating.
Security has been historically classified as a business expense with
Routh’s lunch time anecdote makes it clear that the role of the CISO is evolving. The elevated importance of the CISO within the enterprise shows an increased enterprise awareness and focus on information security risk, but it also speaks to the new nature of the CISO’s role. Traditionally, the CISO was more a of a “back-office” manager focused on network and security operations. The role has evolved. The CISO is in many ways on par with other “C-level” executives. The new CISO is customer-facing and revenue-generating.
Security has been historically classified as a business expense with

Businesses often undertake a check-box approach to cyber security by purchasing security products, meeting compliance standards and performing quarterly or yearly audits. While these methods have proven value, they are often not enough. This leaves businesses vulnerable to threats in a constantly changing risk landscape. To overcome these obstacles, businesses should gain expanded visibility into security performance through data-driven comparison and continuous monitoring.

Last week Stephen Boyer, CTO and Co-Founder of Bitsight, and Oliver Brew, VP of Professional, Privacy and Technology Liability at Liberty International Underwriters, hosted a webinar titled, "Security Ratings: A Big Data Approach to Measuring and Mitigating Security Risk". During this webinar, they discussed the challenges to measuring security risk and how Security Ratings can give businesses the tools to proactively identify and mitigate risk.

On April 7, the open-source OpenSSL project issued an advisory regarding a critical vulnerability identified as CVE-2014-0160 and called “Heartbleed.” This flaw, which takes advantage of OpenSSL’s heartbeat feature, has been present in OpenSSL for over two years, but was only recently discovered. It allows an attacker to trick systems running any version of OpenSSL 1.0.1. from the past two years into revealing 64 KB of data sitting in its system memory per request. There is no limit to the number of requests an attacker can make. Attackers can gain access to private keys, user names, passwords, credit card data, and other sensitive information. They can spoof a website by launching a more effective man-in-the-middle attack. What is both scary and brilliant about attacks exploiting this vulnerability is that they leave no trace in the server logs.

Last week I had the opportunity to be in San Francisco for the RSA conference and Metricon 9. The discussion at the conference and what is now coming out in news reports is that this was the largest RSA event to date in terms of attendance and exhibitors. I agree with what Morgan Stanley cited in their RSA Conference takeaways report: the attention that recent high profile breaches have received contributed to the increased interest from attendees. Cyber risk has finally become a board level issue. The heightened awareness and consequently anticipated increases in security budgets evidence the recognition that organizational cyber security performance is a critical business issue.

With increased emphasis on third party risk management coming down from regulators and executive boards alike, cyber risk in the extended enterprise is shaping up to be a hot topic in 2014.

On December 20, 2013, soon after news of Target’s data breach broke, Venky Ganesan (Managing Director at Menlo Ventures and Bitsight Board Member) talked about Bitsight on CNBC. When asked about cutting edge technology in the cyber risk management space, Venky responded, “I think the most important thing we find right now is that security has become a board room issue. Everybody in the board room wants to know how secure are we, how can we measure security, and how can we manage it. We have an investment in a company called Bitsight that lets us get a rating on how secure your infrastructure is.”