Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Want to capture your board’s attention? Add these seven KPIs to your cybersecurity dashboard.

Here are some key tips for presenting the outcomes tracked by exposure management in a way that will be most helpful to the board and business stakeholders.

Cyber risk mitigation and remediation are often talked about in the same terms. But they are different. Learn how you can optimize both.
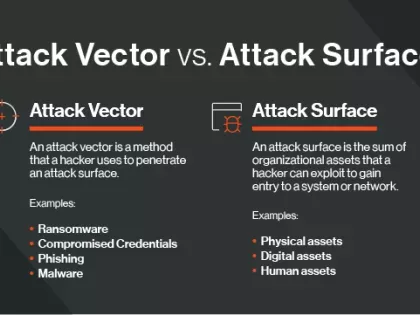
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

Consider these three best practices for mapping your digital footprint and using these insights to better assess cyber risk and drive continuous improvement in your security program.

Give your security teams critical digital risk monitoring tools to discover, prioritize, and remediate risk across the expanding attack surface.

To improve cyber resilience, you must first measure it. Learn the 4 metrics to track to gain insights into your cybersecurity posture.

Here are four best practices for maintaining cyber vigilance as your attack surface expands—to the cloud, across remote locations, and your supply chain.

Taking back control of your network in light of hackers’ growing sophistication can be time-consuming. Even well-established organizations with money to spend on solid cybersecurity programs are still falling victim to some of the new sneaky breach attempts, as seen with this year's ransomware attacks.
But as your digital infrastructure expands, understanding where cyber risk lies hidden can be challenging. In this increasingly diverse environment, your security team ends up buried in a sea of data and alerts — and may end up missing something important. They are also hopping between multiple tools and lack a complete picture of your company’s security posture.
Rather than play whack-a-mole with threats, here are three reasons you should focus on attack surface scanning to mitigate risk.
But as your digital infrastructure expands, understanding where cyber risk lies hidden can be challenging. In this increasingly diverse environment, your security team ends up buried in a sea of data and alerts — and may end up missing something important. They are also hopping between multiple tools and lack a complete picture of your company’s security posture.
Rather than play whack-a-mole with threats, here are three reasons you should focus on attack surface scanning to mitigate risk.

A vulnerability scanner evaluates security weaknesses and gaps in your digital infrastructure. Learn what to look for in a robust solution.

Discover five practical cyber risk reduction strategies including understanding your attack surface, continuous monitoring, keeping software updated, and more.

Learn about the four pillars of cyber preparedness and why it’s everyone’s responsibility to get involved.

Explore actionable attack surface reduction examples that can reduce risk across your expanding digital environment.

Learn what you can do to defend against cyber attacks and achieve a state of cyber resilience.

Organizations remain concerned about the potential implications to their own security posture as a result of the Okta cyber attack. It's important to identify where risks are present throughout your third parties landscape.