Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

The threat of ransomware has been increasingly prevalent, especially within the high-stakes industries like healthcare and those involved in the election.

Malware can gain entry to your network in many ways. Once malware has penetrated a network, threat actors can use it to steal information, encrypt systems, spy on users, and remove files. Learn how to prevent dangerous malware.

In 2021, ransomware attacks on government agencies globally increased by 1,885% over 2020 attacks, and the trends are continuing so far in 2022. Learn how to protect your organization from ransomware with three best practices.

Learn about the top ransomware attack vectors favored by hackers and the steps you can take to protect your organization.

What is cyber resilience vs. cybersecurity and why in today’s digital economy you need a plan for both.

Want to capture your board’s attention? Add these seven KPIs to your cybersecurity dashboard.
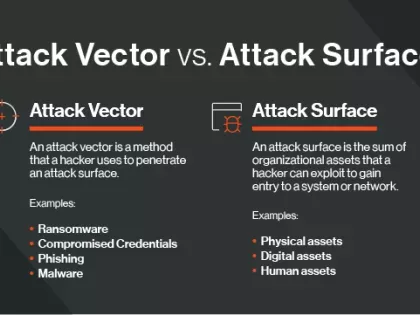
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

We’re back again with a monthly-ish blog reflecting on major goings on in the security world.

Recent Bitsight research shows that 76% of healthcare organizations may be at increased risk of ransomware attacks due to poor TLS/SSL configuration management.

Cyber insurers regularly get requests for new business and increased limits. Insurers need to measure an applicant's cyber hygiene with cyber metrics that are categorically proven to stand out.

How do cyber insurers determine which organizations are going to be a risk worth taking? It’s more important than ever to continue underwriting good and opportunistic risks, while not overcorrecting for the high loss ratios the industry is seeing. Insureds need to answer two questions: what is good cyber hygiene and how do you measure it?

People’s perception of your cyber risk will outweigh its actual performance. And when trust in cybersecurity takes a nosedive, it can make a big dent in your financials. Learn how to prove protection and build trust with three key stakeholder groups.

On the surface, the Bitsight Rating and associated Risk Vectors look self-explanatory, but there's an artistic element as well. In the case of Bitsight, that means having a thorough understanding of cybersecurity and drawing inferences from the data.

Bitsight teamed with Moody’s Investors Service to discuss the cybersecurity trends to watch in 2023 and how security leaders can adapt their programs to increase preparedness.

Ransomware can gain access to your network through your third party ecosystem - and it may be more likely than you think. Read our latest blog to learn the three most effective ways to defend against third party ransomware risk.