New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
Zerologon: Bitsight Observations on a Dangerous Vulnerability


New vulnerabilities emerge daily... but not every vulnerability is being actively exploited by nation state actors. Zerologon (CVE-2020-1472) is one such vulnerability. Zerologon was recently identified by the National Security Agency (NSA) as one of 25 vulnerabilities actively being exploited by Chinese state-sponsored actors.
Security and risk leaders should act immediately to determine whether their organizations -- and the organizations that comprise their supply chain -- are vulnerable to Zerologon. This blog contains analysis from Bitsight’s global telemetry to help organizations understand the impact and risk of Zerologon.
What is Zerologon (CVE-2020-1472)?
Zerologon is a vulnerability that affects Windows servers, specifically Domain Controllers. This vulnerability allows an unauthenticated attacker to gain administrative access to the Domain Controller by taking advantage of a cryptographic vulnerability in the Windows Netlogon service.
In September, Secura posted a whitepaper describing Zerologon. Later it was discovered that this vulnerability also affects Linux Samba servers in a certain configuration.
Why is Zerologon significant?
As Secura mentions in their whitepaper:
This attack has a huge impact: it basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain.
It is possible for this vulnerability to be exploited over the Internet. Many have suggested that this vulnerability can only be exploited from the inside of a corporate network. But an attacker only needs to be able to reach the Netlogon service on the target machine and know the computer name of the target machine in order to execute this attack. In fact, there are new reports about Zerologon being leveraged by Ransomware groups.
Is there an Alert and/or Patch?
The vulnerability has been patched by Microsoft in their Patch Tuesday cycle in August 2020.
The attack is serious enough that the United States CISA has issued an alert for it, urging administrators to patch all domain controllers immediately. The NSA recently issued an alert highlighting Zerologon as a Top 25 vulnerability being exploited by Chinese state-sponsored actors.

How did Bitsight identify exposed systems?
In order to identify Internet exposed systems with the Netlogon service running, we:
- Scanned the Internet for port 135/TCP, Microsoft’s RPC Endpoint Mapper service;
- For each port opened, interacted with the above service and queried it for NRPC bindings (Netlogon);
- If the Netlogon service is running, the system will provide us with the available bindings.
- The Endpoint Mapper service will also inform the client of the target systems computer name (which is needed for exploitation).
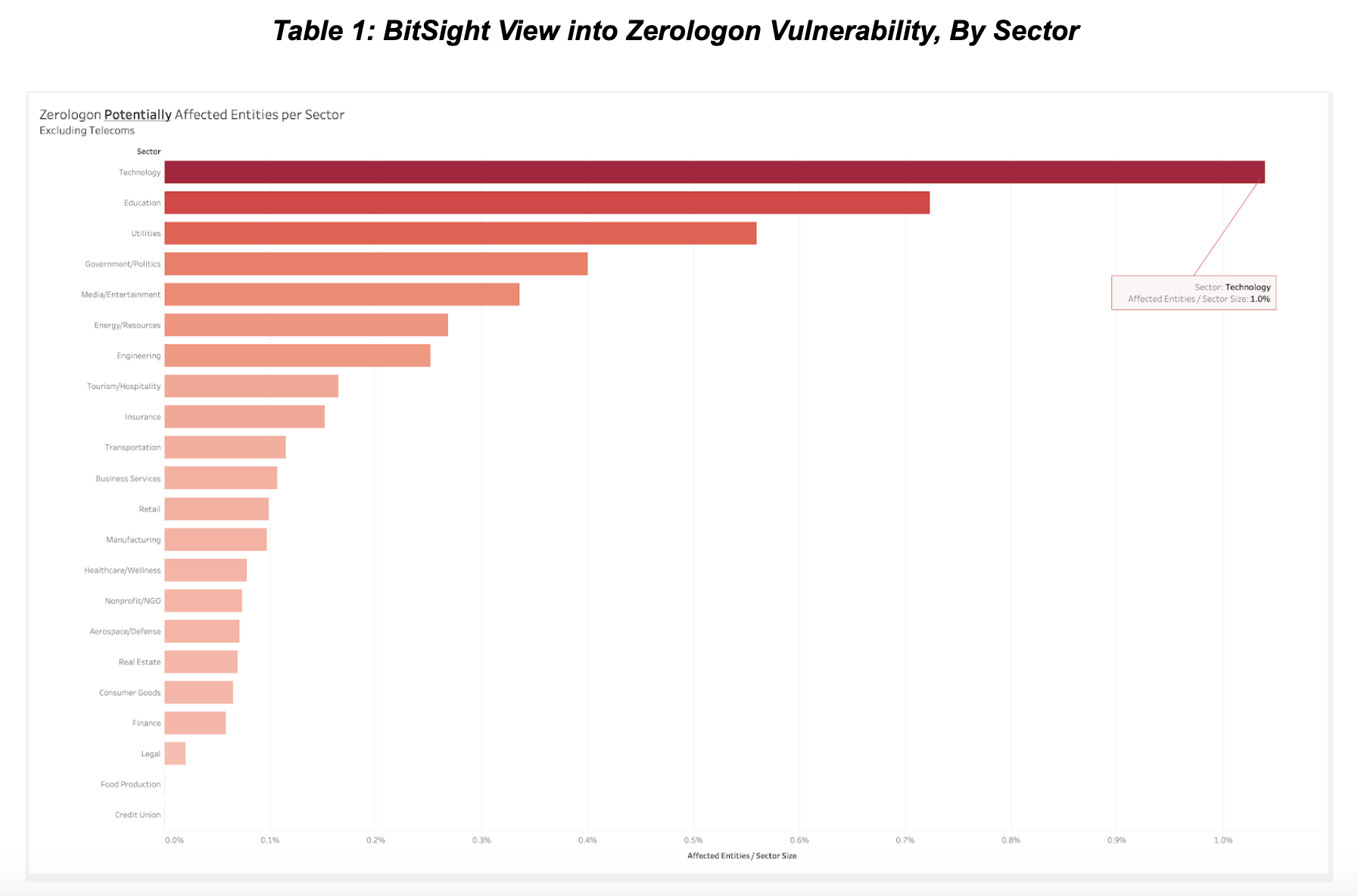
What did Bitsight see?
In October 2020 we were able to identify at least 17,000 systems with Netlogon enabled and available for remote connection over the Internet, indicating that these systems have a Domain Controller role and are potentially vulnerable to this attack (if they have not already been patched). We did not try to directly connect to the Netlogon port on all of these systems, but manual testing on a small subset shows that the Netlogon port is unfiltered in the vast majority of cases.
Next Steps for Security and Risk Professionals
Our research indicates that Zerologon can be exploited remotely over the Internet and that there are thousands of exposed and potentially vulnerable systems ready to be attacked by malicious actors. We emphasize that this threat is not necessarily restricted to attacks from inside the corporate network. There is a non-negligible number of systems exposed to attacks from the Internet.
The NSA has recently warned of the dangers associated with Zerologon. Organizations must act now to gain visibility into these vulnerabilities within their own organization, as well as their supply chain partners. System owners should ensure that their systems are patched and that mission critical systems such as domain controllers are properly protected from attacks from outside their network. By identifying and mitigating these critical risks across their ecosystem, they can reduce the risk of becoming the next victim of a state-sponsored cyber attack.
To learn how Bitsight can help you manage these and other risks to your organization and your third party ecosystem, contact us for a demo and receive your complimentary vendor portfolio risk report to see where your vendor cyber risks are.


