Who’s Ready for the CMMC? What Data Reveals About Defense Sector Cybersecurity
Tags:

In the upcoming months, the Cybersecurity Maturity Model Certification (CMMC) will go live. Thousands of third party assessors will begin cybersecurity assessments of hundreds of thousands of U.S. Defense contractors. What will the assessors find?
There has never been a comprehensive, objective assessment conducted of the security posture of the U.S. Defense Industrial Base -- reportedly exceeding 300,000 companies. How is the Defense sector actually doing with respect to cybersecurity? Are there areas of strength? Vulnerability? Common issues among companies? Are improvements possible? If so, how?
By continuously and non-intrusively collecting security performance information across the global Internet, Bitsight can help answer some of these critical questions. For this study, Bitsight analyzed the data of more than 3,500 Department of Defense (DoD) contract holders, many of whom will be subject to the new CMMC requirements. Among the findings from our assessment:
- Defense sector cybersecurity performance is on par with other sectors. In comparing Defense to other sectors, there’s not much difference in the average cybersecurity performance. But should the DoD expect stronger performance given the criticality of the data?
- “Critical” vulnerabilities persist among Defense contractors at high rates. The Defense sector is challenged to remediate “Critical” and “High” vulnerabilities, as measured by the CVSS, raising questions about whether organizations can satisfy certain requirements in the CMMC. Analysis shows that some of the most important vulnerabilities that have been announced by the National Security Agency (NSA) and Department of Homeland Security (DHS) in the last year still persist within the sector. For example, the rate at which the Defense sector remediated the major BlueKeep vulnerability underperforms other sectors.
- Open port exposure puts Defense contractors at risk. Configuration management -- particularly with respect to managing risky Internet exposure through “open ports” -- is a challenge for Defense contractors. In reviewing the Defense contractor cohort, Bitsight finds a large number of open ports that we would characterize as highly risky activity.
- Defense contractors with larger networks underperform contractors with smaller networks. Conventional wisdom is that smaller Defense contractors have weaker security compared to large Defense contractors. But the data suggests there is more to the story. According to Bitsight analysis, on average, Defense contractors who operate larger networks have weaker security performance than contractors who operate smaller networks.
Background
There are reportedly over 300,000 companies that comprise the U.S. Defense Industrial Base (DIB) -- a sector that enables R&D, designs and produces military weapons systems, sustains military operations, delivers technology and support to the warfighter, and many other critical functions.
For years, policymakers and military officials alike have raised deep concern about the cybersecurity posture of the organizations that comprise the DIB, warning that foreign countries and malicious actors are jeopardizing U.S. national security by actively stealing secrets and data. Officials warn that the theft of both classified information and sensitive, unclassified information poses a threat to the United States.
In an effort to gain visibility into the cybersecurity posture of the DIB, the DoD began work in 2019 on the Cybersecurity Maturity Model Certification (CMMC), a program requiring any company doing business with the DoD to have its cybersecurity hygiene assessed by an independent third party assessor. The CMMC is administered by the CMMC-AB, an organization that trains and certifies assessors and collects the data gathered by its assessors. Assessments are performed onsite and are valid for approximately three years. There are also plans to supplement data collected through the assessments with real-time, continuous data collection.
The CMMC is not optional. Required CMMC levels will be specified in each contract, clearly stated in all RFPs, and will be a “go/no go” decision. In other words -- if a company fails to meet the required Level, they can’t win the contract.
Bitsight Analysis of the Defense Sector
Policymakers are hoping that assessors will help the DoD develop a better understanding for the Defense sector’s cybersecurity performance. But what will the assessors find when they go into the market?
Bitsight analyzed the security posture of more than 3,500 DoD contractors to better understand the current state of DIB cybersecurity.
Bitsight continuously collects over 200 billion security events on a daily basis from around the global Internet in an automated, non-intrusive fashion, and leverages this data to create objective research and analytics.
DoD Contractors Perform Similarly to Non-Defense Companies in Other Sectors
The first thing apparent in our analysis is that, overall, U.S. Defense contractor cybersecurity performance actually looks very similar to the performance of other companies and sectors. Bitsight continuously rates organizations on a 250-900 scale, similar to a credit rating model. The lower the score, the greater the likelihood of breach. Bitsight also divides security performance into 3 segments: Basic (250-640), Intermediate (640-740), and Advanced (740-900).
The chart below shows the distribution of security performance across nearly 180,000 companies in all sectors.
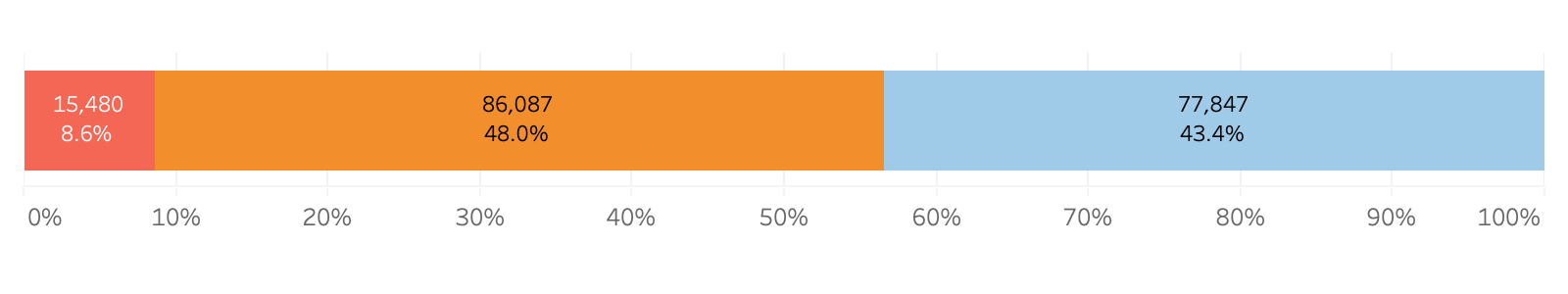
When Bitsight reviewed the security posture of a cohort of 3,661 companies that held DoD contracts in FY2019, we found a very similar breakdown in overall security performance, albeit with a slightly smaller percentage of organizations performing at the “Advanced” level and slightly greater percentage of organizations performing at the “Intermediate” level.
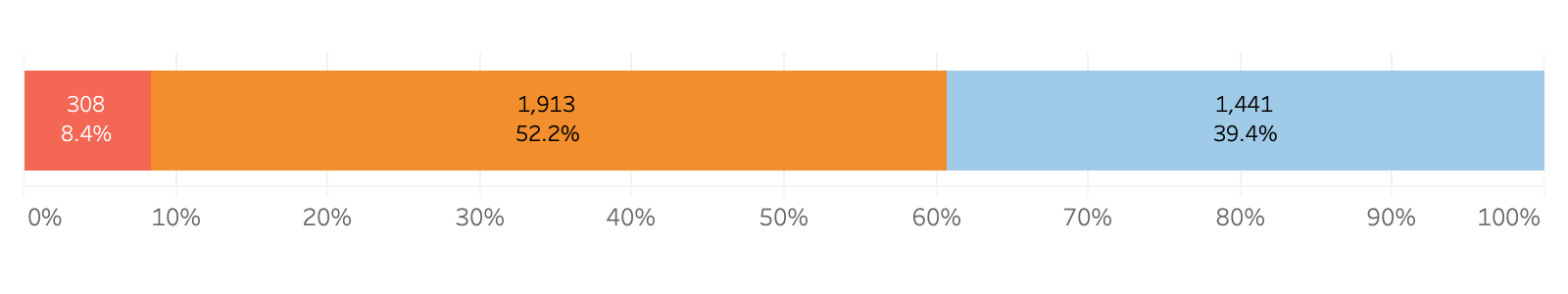
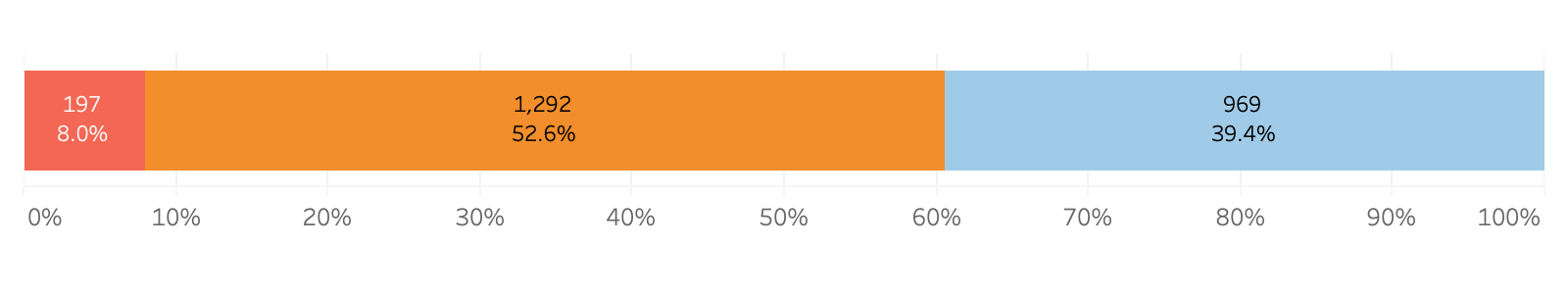
Bitsight took a closer look at organizations who possess “Controlled Unclassified Information” -- sensitive but unclassified data that is often a target of malicious actors. Bitsight reduced the broader cohort of 3,661 “DoD contract holders” down to the companies that were most likely to possess CUI data (e.g. aerospace companies, manufacturers, healthcare organizations), leaving us with a cohort of 2,457 companies. These “CUI Likely” companies performed nearly identically to the larger DoD contractor cohort.
Critical Vulnerabilities Persist Within Defense Contractor Ecosystem
CMMC assessors will soon be reviewing the risk and vulnerability management programs of Defense contractors. This is an important area of focus within the CMMC Framework, which includes various requirements for risk and vulnerability management. For example, the Framework requires any organization at Level 2 or higher to develop plans, scan for, and remediate vulnerabilities within their systems. Organizations are also required to monitor security controls for effectiveness.
In an effort to assess the effectiveness of current vulnerability management programs, Bitsight reviewed the “CUI Likely” cohort to understand whether any significant vulnerabilities may be present within this group. Bitsight turned to the Common Vulnerability Scoring System (CVSS), an open framework for communicating the characteristics and severity of software vulnerabilities. Bitsight specifically looked at a number of known “Critical” (CVSS 9.0+) and “High” (CVSS 7.5+) vulnerabilities identified recently by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
The below chart identifies examples of significant vulnerabilities that currently exist within the DoD contractor ecosystem. Red circles indicate the most Critical vulnerabilities (CVSS score of 9+) compared to orange (CVSS score of 8+) and blue (CVSS score of 7.5+). The size of the circle corresponds to the company’s employee count.
According to Bitsight’s analysis of the CUI cohort of 2,457 companies, some of the most critical vulnerabilities are still resident within the DoD contractor environment:
- 2% of the companies analyzed still have not remediated the BlueKeep vulnerability, more than a year after warnings from NSA, DHS, and Microsoft.
- 1.4% of the companies analyzed are still vulnerable to a major Citrix vulnerability, despite warnings from DHS and Citrix earlier in 2020.
- 0.3% of the companies analyzed are still vulnerable to the Pulse Secure vulnerability, despite alerts from DHS in 2019.

A closer examination of the Defense sector’s approach to the BlueKeep vulnerability reveals that the sector as a whole has been slower to remediate this vulnerability when compared to efforts taken by other sectors like Legal, Insurance, and Healthcare/Wellness. According to the data, the Defense sector more closely mirrors the median response rather than industry-leading practices. The rate of patching is particularly interesting considering the public alerts issued by the NSA, warning of the danger of this vulnerability and the importance of patching.
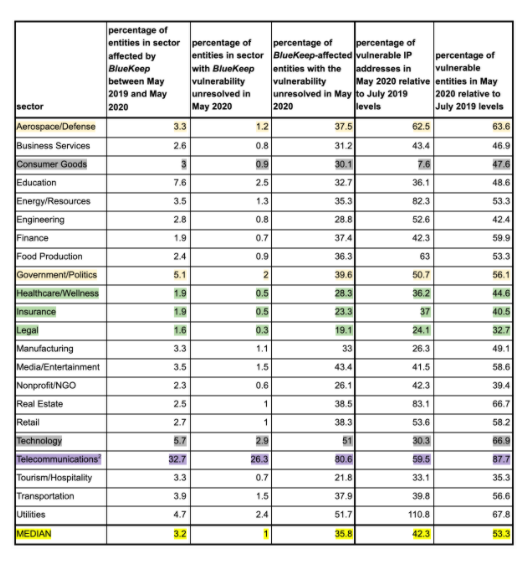
Bitsight expanded its analysis of “Critical” vulnerabilities (9.0+ CVSS) to FY2019 DoD contractor holders. We find a high level of exposure across the Defense contractor community:
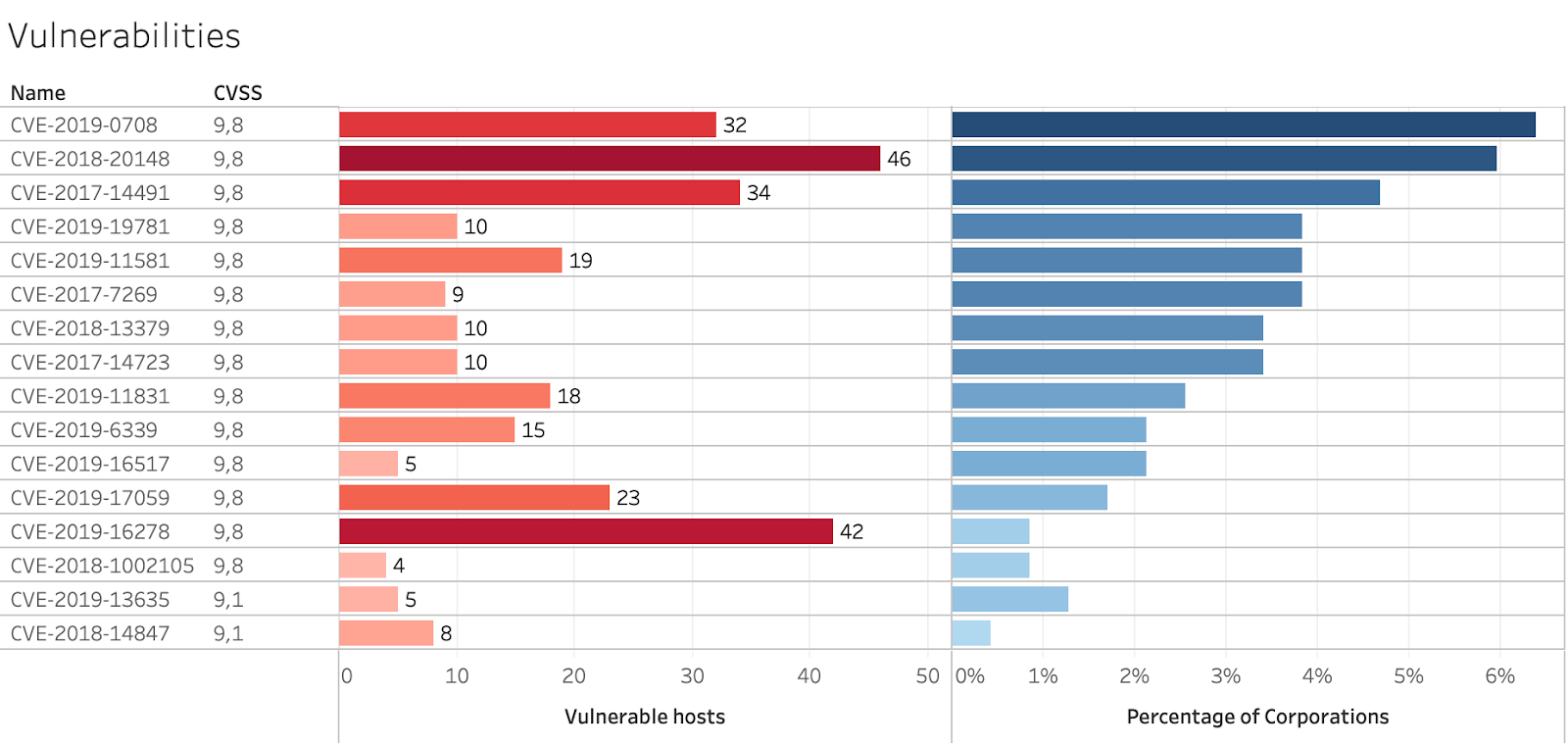
There is also prevalence of “High” vulnerabilities (7.5+ CVSS) across the broader DoD contractor community:

The data collected for this analysis represents a small subset of the total vulnerabilities and security performance issues that Bitsight observes and collects, and raises important questions about the implementation of the CMMC. Will CMMC assessors evaluate control implementation and test control effectiveness? Or will they focus only on reviewing control documentation? If the CMMC is to become more than a compliance exercise, controls effectiveness deserves scrutiny... but the data suggests that a number of security programs may not withstand this additional scrutiny.
Open Port Exposures Put Defense Contractors At Risk
In addition to reviewing risk and vulnerability management programs as described above, CMMC assessors will also be reviewing Defense contractors’ configuration management programs to determine risk and exposure. Configuration management includes maintaining baseline configurations and inventories of systems. It also requires restricting or disabling the use of nonessential ports and services, typically known as “open ports.” Port exposure scanning is also required for Defense contractors under the CMMC’s “risk management” section.
Open ports are a leading cause of breach. Attackers often seek to exploit Internet-exposed open ports that may have outdated protocols or vulnerabilities as a way of gaining entry to an organization. A recent study by MIT found that open port exposures contribute to the largest total losses from cyber attacks.
In reviewing the Defense contractor cohort, Bitsight finds a large number of open ports that we would characterize as highly risky activity. 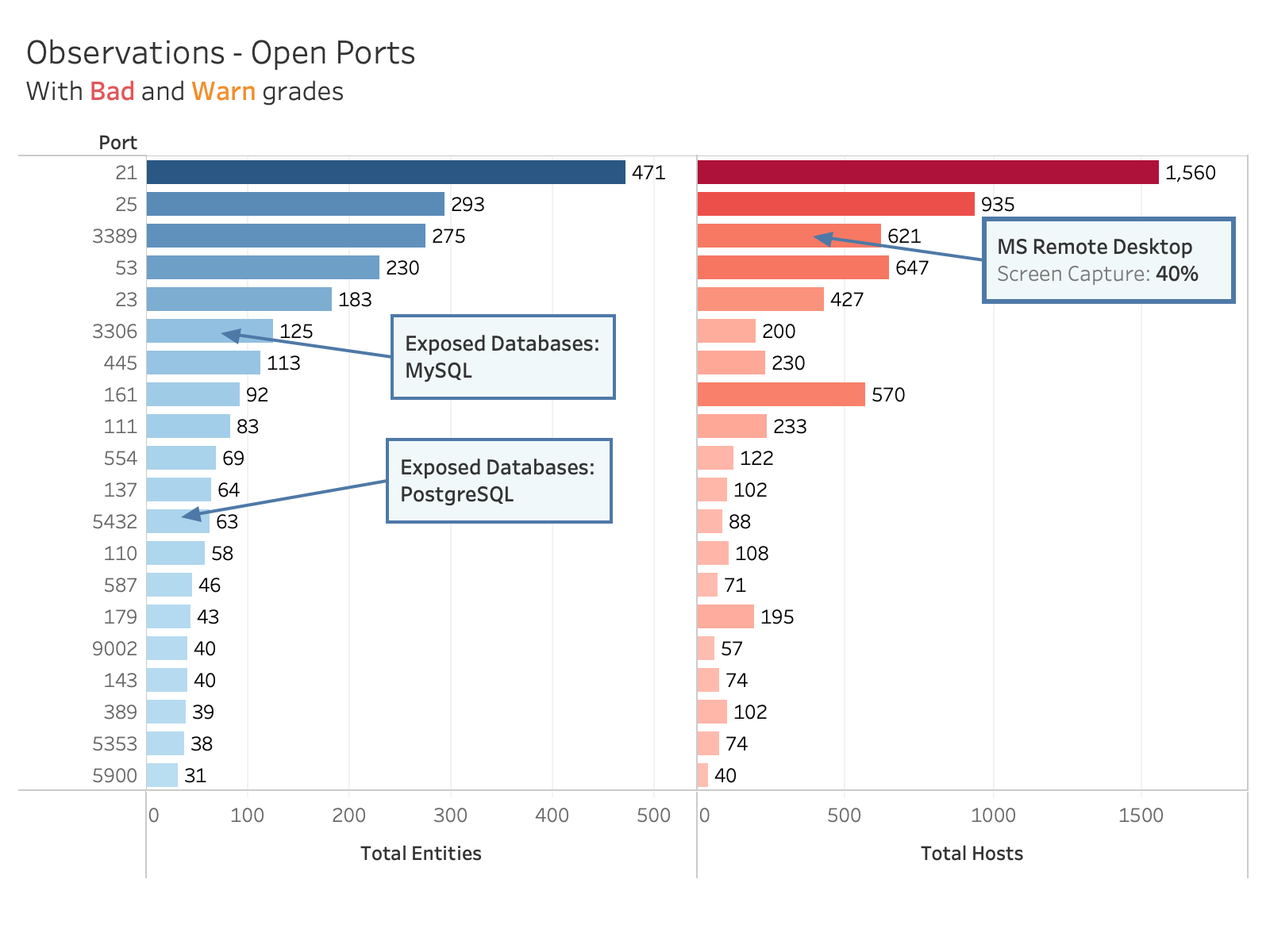
The data suggests that CMMC assessors will encounter significant exposure when assessing configuration management programs in Level 3+ organizations. How will CMMC assessors identify these risks? Will Defense contractors successfully close these gaps prior to their assessments? Or will open port exposure negatively impact the certification of Defense contractors?
Defense Contractors With Larger Networks Underperform Contractors with Smaller Networks
It is conventional wisdom that larger organizations with more employees perform better in cybersecurity than smaller organizations with fewer employees. It is often assumed that larger organizations deploy more resources and personnel to address cybersecurity issues and therefore must be doing “better” than their smaller, less-resourced counterparts. But the data suggests that a different segmentation may be more appropriate.
Bitsight finds that companies who operate large network infrastructure (measured by IP address space) generally have weaker cybersecurity performance compared to organizations operating smaller networks.
The below chart illustrates the relative performance of organizations operating networks of various sizes. Again, we analyzed the “CUI Likely” cohort. The Y-axis describes the size of the network infrastructure (by number of IP addresses) -- the top of the Y-axis shows organizations operating with more than 1 million IP addresses under its control. The data shows that organizations with smaller network footprints have stronger overall cybersecurity performance ratings than organizations with larger networks.
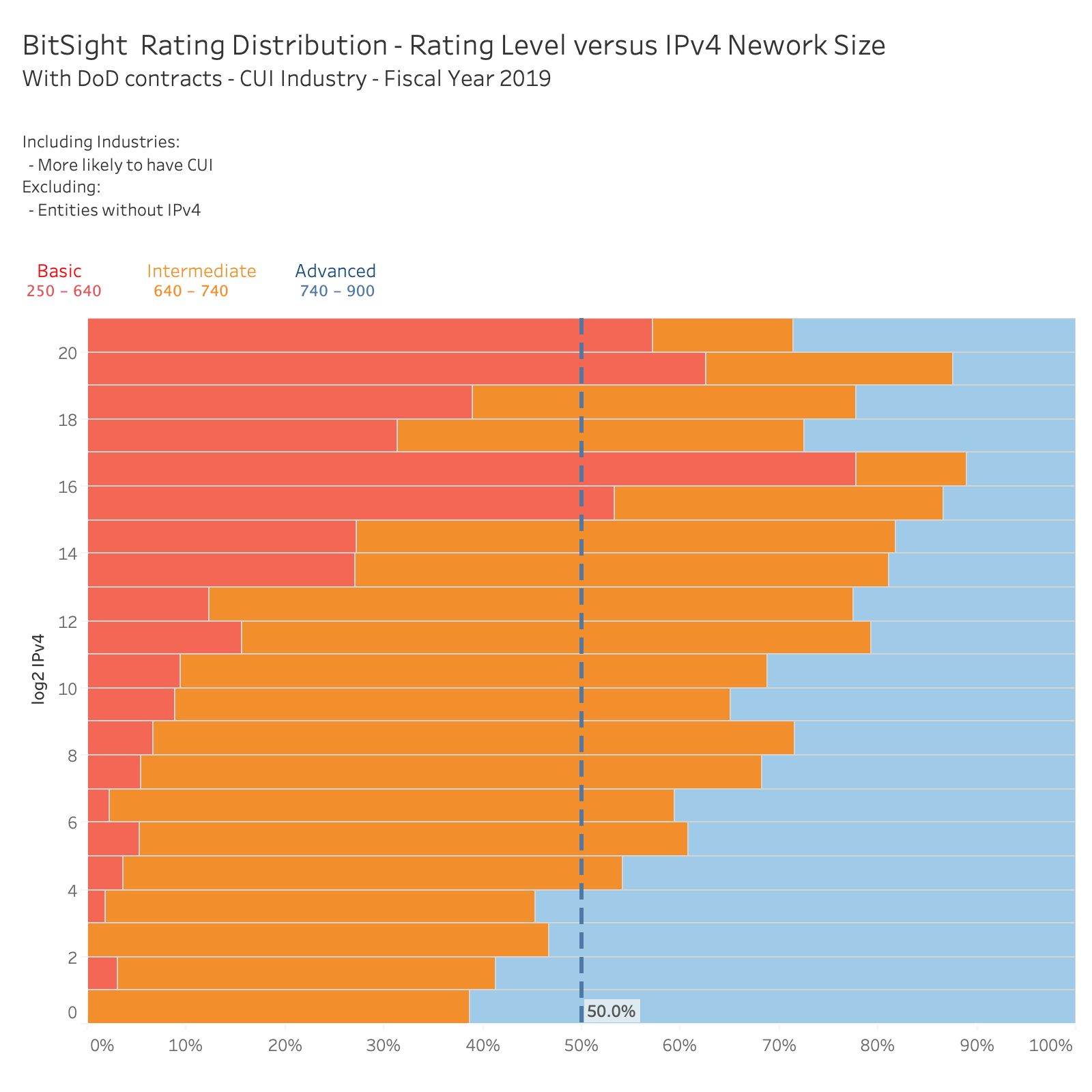
This finding has implications for CMMC assessors and Defense organizations alike. On the one hand, it is important for assessors to remain objective and avoid bias based on organizational size. On the other hand, DoD should not be surprised if larger Defense organizations -- who must manage and monitor a larger attack surface -- may actually face significant challenges in achieving their requisite CMMC certifications.
What’s Next?
For Bitsight, this analysis represents only the beginning of what is possible. Are there other common risks facing the sector? Can similar analyses be performed on Defense subsectors? Do certain military branch contractors perform better than others? Is contract value correlated with security performance?
In the months ahead, the CMMC will forever change the way that the Defense sector addresses cybersecurity. While much remains uncertain, one thing is clear: objective data about the security performance of Defense organizations that is continuously and non-intrusively collected can provide valuable insight and perspective to the DoD, CMMC assessors, and DIB alike.
Whether used during the assessment process to improve an evaluation, as a method of identifying changes in performance between assessments, as a basis for creating targeted remediation initiatives, or as a way of helping organizations benchmark the sector to improve their own cybersecurity performance, continuous monitoring data can help the Defense sector meet the challenges in cyberspace and ensure a more secure future.