The third-party risk management solution backed by the security rating that started a whole industry.
Third-Party Risk Management Tools
As the global supply chain landscape grows more complex, organizations increasingly depend on third-party relationships, inevitably expanding their attack surface. Effective third-party risk management (TPRM) tools have become essential, helping cybersecurity teams reduce risk, meet compliance requirements, and enhance visibility across their vendor ecosystem.
Effective third-party risk management, however, can be extremely challenging for even the most mature organizations. Many providers offer tools that claim to make TPRM easier and more comprehensive — but which of these solutions and tools do you really need?
In this guide, we'll explore ways to help you understand, evaluate, and implement the right third-party risk management tools for your organization.
What are third-party risk management (TPRM) tools?
Third-party risk management tools enable cybersecurity teams to assess, monitor, and mitigate risks posed by external partners. Unlike traditional vendor management systems, TPRM solutions offer cybersecurity-specific capabilities designed to handle complexities associated with third-party cyber risk, compliance, and security assessments. These tools automate processes, reducing manual effort and allowing organizations to scale risk management effectively.
Key features and capabilities of third-party risk management tools
When evaluating TPRM tools, look for these essential features:
Automated risk assessments
Streamline the assessment process, minimizing manual efforts and human error.
Continuous monitoring
Real-time alerts and insights into third-party security posture.
Risk scoring & benchmarking
Provides actionable insights by quantifying and prioritizing risks.
Integration capabilities
Compatibility with your existing security architecture, such as GRC, SIEM, and IAM solutions.
Advanced TPRM tools also offer intuitive dashboards and reporting functionalities, empowering cybersecurity teams with actionable data for decision-making.
Common TPRM tools
There’s no one-size-fits-all approach; a number of variables will determine the best course of action for your business. However, whether you’re launching, growing, or optimizing your TPRM program, there are certain tools that any organization should have.
Integrated risk management software
Even if your organization only has a handful of third-party vendors, it’s still important to use a management system to keep track of objectives and progress. This system can be as complex as integrated risk management (IRM) software, or as simple as a well-organized spreadsheet.
If your organization only has five vendors, for example, a spreadsheet would likely suit your needs and be easy enough to manage. However, if your organization has 500 or 5000 vendors, investing in a dedicated TPRM software platform is probably a better solution — in the long run, it will make the process of scaling your TPRM program much simpler.
Regulations are another factor. Companies in heavily regulated industries like healthcare, finance, and utilities — even if they don’t have a huge vendor roster — might need full-featured TPRM software, which can be used to track the delivery and receipt of security risk assessment questionnaires, schedule penetration tests and on-site visits, manage review and assessment tasks, and generate reports for compliance purposes. Wide-reaching regulations like GDPR are also making TPRM-specific software more essential.
Without a solid cyber security risk assessment tool, it’s easy for things to fall through the cracks, especially as a third-party vendor roster grows. In an area as high-stakes as cybersecurity, organizations can’t afford to let even the little things slip.
Questionnaires
Though they’re not necessarily a “tool,” vendor risk questionnaires are the backbone of most comprehensive TPRM programs. Thorough, consistent, and well-designed security questionnaires for your vendors to complete and return are critical to reducing third-party risk.
While questionnaire templates are a good place to start, the questions should always be tailored to your particular industry and concerns. As your TPRM program matures, you’ll want to start adapting questionnaires for each vendor or partner, taking into consideration their past performance and the systems and data to which they have access.
Traditionally, administering a questionnaire during the onboarding process and following up at regular intervals to ensure that security is being maintained (or better yet, improved) has been best practice. While this may change in the future thanks to third party monitoring technologies, it’s still an important part of TPRM for many companies.
However, questionnaires should not be the only component of a TPRM program — they can become inaccurate fast as new threats emerge and third-party security performance changes. Relying solely on questionnaires to assess cybersecurity gives you an incomplete picture of a third party’s security posture, so questionnaires are best utilized in addition to other TPRM tools.
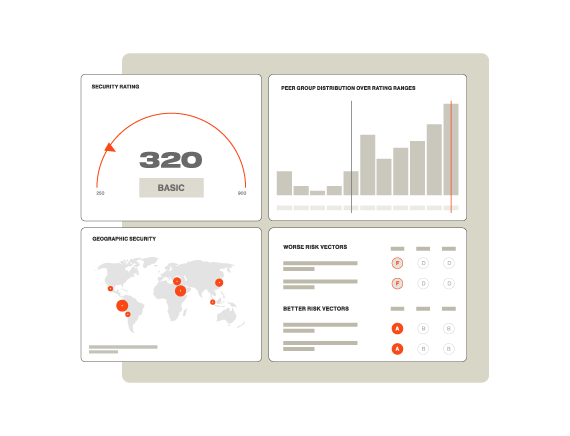
Security ratings
A 2018 study found that for 88% of organizations, it took over two weeks to assess vendors’ cybersecurity using manual methods such as a cyber security risk assessment questionnaire. When each assessment requires this much effort, it’s not possible to maintain a continuous picture of third-party risk.
Continuous monitoring solutions like security ratings help cover the gaps between questionnaires by allowing companies to track third parties’ cybersecurity performance in near real time. Security ratings are a data-driven, dynamic measurement of an organization’s cybersecurity performance. Ratings are derived from objective, verifiable information and created by independent organizations. Security ratings enable you to quickly ascertain a vendor’s cybersecurity posture, track changes to their performance over time, and identify their biggest vulnerabilities.
In addition, because security ratings are easy-to-understand numbers that reflect actual cyber risk, they provide a clear frame of reference and make it easier to communicate with stakeholders about cybersecurity.
How to evaluate and choose the right TPRM tool
Choosing the right third-party risk management tool involves aligning tool capabilities with your organization's unique needs. Consider these criteria during evaluation:
- Scalability: Ensure the tool can accommodate growth in your vendor ecosystem.
- Ease of use: Select user-friendly platforms that encourage adoption across departments.
- Integration flexibility: Prioritize tools offering seamless integration with your current cybersecurity tools and processes.
- Compliance support: Verify robust support for regulatory requirements like GDPR, HIPAA, ISO 27001, and SOC 2.
Remember, the best tool should simplify and improve your risk management process, not complicate it.
Benefits and ROI of third-party risk management tools
Implementing an effective TPRM solution provides substantial benefits and measurable returns, including:
- Reduced cybersecurity risk: Decrease likelihood and impact of breaches originating from third-party vulnerabilities.
- Time and cost savings: Automating assessments and monitoring saves valuable resources, allowing your team to focus on strategic security initiatives.
- Compliance management: Simplify regulatory compliance, avoiding costly penalties associated with non-compliance.
Organizations leveraging robust TPRM tools typically report improved visibility into vendor risk, better decision-making capabilities, and a notable decrease in third-party security incidents.
Though measuring ROI on TPRM programs is not always straightforward, trusted industry analysts can help point you in the right direction. For example, the 2024 Total Economic Impact™ of Bitsight, a commissioned study conducted by Forrester Consulting, found that Bitsight’s comprehensive External Attack Surface Management and Third Party Risk Management offerings reduced cyber risk, while delivering an investment return of 297% over three years. Additionally, the solution paid for itself in less than 6 months.
Top challenges and best practices for implementing TPRM tools
While TPRM tools provide significant advantages, implementation comes with common challenges, including tool sprawl, inadequate integration, and insufficient internal alignment.
Challenges include:
- Tool redundancy: Organizations often adopt multiple overlapping tools, increasing complexity and costs.
- Limited visibility: Without proper integration, organizations struggle to gain comprehensive views of third-party risks.
Best practices for overcoming these challenges:
- Tool consolidation: Regularly evaluate and consolidate overlapping tools to streamline your vendor risk management efforts.
- Clear internal alignment: Establish clear roles and responsibilities, ensuring collaboration between security, procurement, and compliance teams.
- Comprehensive integration: Prioritize tools that offer extensive integrations, ensuring full visibility across your security landscape.
By addressing these challenges proactively, organizations can optimize their use of third-party risk management tools and realize significant cybersecurity benefits.
Final thoughts
Third-party risk management tools are critical for modern cybersecurity practices. Choosing, implementing, and optimizing the right TPRM solution can significantly reduce your organization's cybersecurity risk, enhance compliance efforts, and deliver tangible ROI.
Stay proactive, continuously assess your toolset, and leverage TPRM solutions effectively to secure your organization's third-party ecosystem.
Bitsight Third-Party Risk Management
Bitsight for Third-Party Risk Management and other Bitsight technologies provide all of the tools required to develop and support a comprehensive TPRM program. With Bitsight, you can:
- Enable your business by bringing on vendors in a timely way: With Bitsight, you can help your organization enjoy the benefits of working with vendors while summarizing and communicating the risk that is associated with each relationship. Bitsight enables you to communicate technical details to stakeholders throughout the organization, using a common language and set of easily understood metrics that enable everyone to make outcomes-based, informed decisions.
- Onboard vendors faster: Smart tiering recommendations, workflow integration, and risk vector breakdowns that identify areas of known risk can help to accelerate onboarding and making your third-party risk management program more scalable.
- Mitigate third-party risk: Make confident, data-driven decisions to prioritize resources, improve operational efficiency, and drive efficient risk reduction across your vendor portfolio.
- Improve executive reporting: Bitsight facilitates data-driven conversations with senior executives and board members by streamlining the reporting process, demonstrating how investments in security directly impact performance, and providing essential metrics and context that enable oversight of your cyber security plan.
- See a clear picture of cyber risk aligned to risk tolerance: With a clear view of critical performance information across the entire portfolio, Bitsight enables risk managers to make confident, data-driven decisions to prioritize resources that drive efficient risk reduction.
- Personalize your monitoring options: Bitsight enables organizations to select the best level of monitoring for each vendor depending on their closeness to sensitive company data, as well as set alerts for when a vendor hits a concerning change in their rating, promoting greater efficiency without overspending or underutilizing risk management technology.