What ended up on the cutting room floor after we sliced and diced the KEV
Tags:


In the course of a major research rollout like my recent whitepaper on KEV vulnerabilities, I frequently end up doing some bit of analysis that doesn’t make it into the final doc. Usually, it is because I am dealing with limited space and attention spans, and I gotta stop sometime. The stuff that gets cut is usually not terribly compelling or surprising or is maybe more an artifact of the particular bias in our sample or is only interesting to a very small audience. Things that don’t rise to the consideration of the Gray Matter Presidium1 here at Bitsight.
Inevitably, when the decision gets made to cut a bit of analysis, the universe chuckles a bit and ensures that some of the first people who see the research will ask “hey have you thought about…” and I gotta go back and double check the analysis and clean up the charts to make them presentable like I’m expecting company. In this case two pieces of information folks are curious about are:
- Which vendors produce software that have the most KEV exposures and at what speed are they remediated?
- Can you dip into the alphabet soup again and slice things by Common Weakness Enumeration?
The reason vendor analysis didn’t end up in the report is there was a view that calling out specific vendors might make it appear like we are casting aspersions on the quality of the software they produce. This couldn’t be further from the truth. Appearing in the KEV Catalog may actually be an indication that a particular vendor is making popular enough products that actors think it’s worth their while to try to break. Moreover, we can’t necessarily blame vendors if organizations are slow to patch software. Remember, nothing goes on the KEV unless a fix is available2. One last caveat here is which vendors show up the most (or at all) in Bitsight data is a function of the type of software they produce. As we mention in the report we are generally scanning for things that are externally accessible, and not every vendor on the KEV makes products that are.
So with 153 words of caveat in the preceding paragraph, here are the vendors present in the KEV catalog that Bitsight detected vulns from the most in 2023.
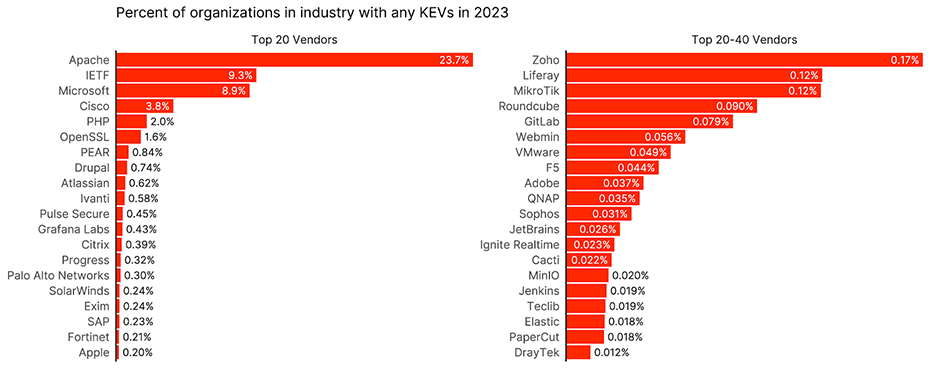
Figure 1 Vendors with KEVs that appear the most in organizations in 2023. Note the right hand side has a different scale than the left.
Things here are pretty unsurprising. Apache is at the top because they make very popular web servers that can provide attackers with a foothold within organizations. Microsoft Exchange vulnerabilities were very prevalent and we see that in aggregate here. Read on and find your favorite.
The other major measure we looked at was median remediation time, so let’s combine the above with a sprinkling of ransomware information in Figure 2.
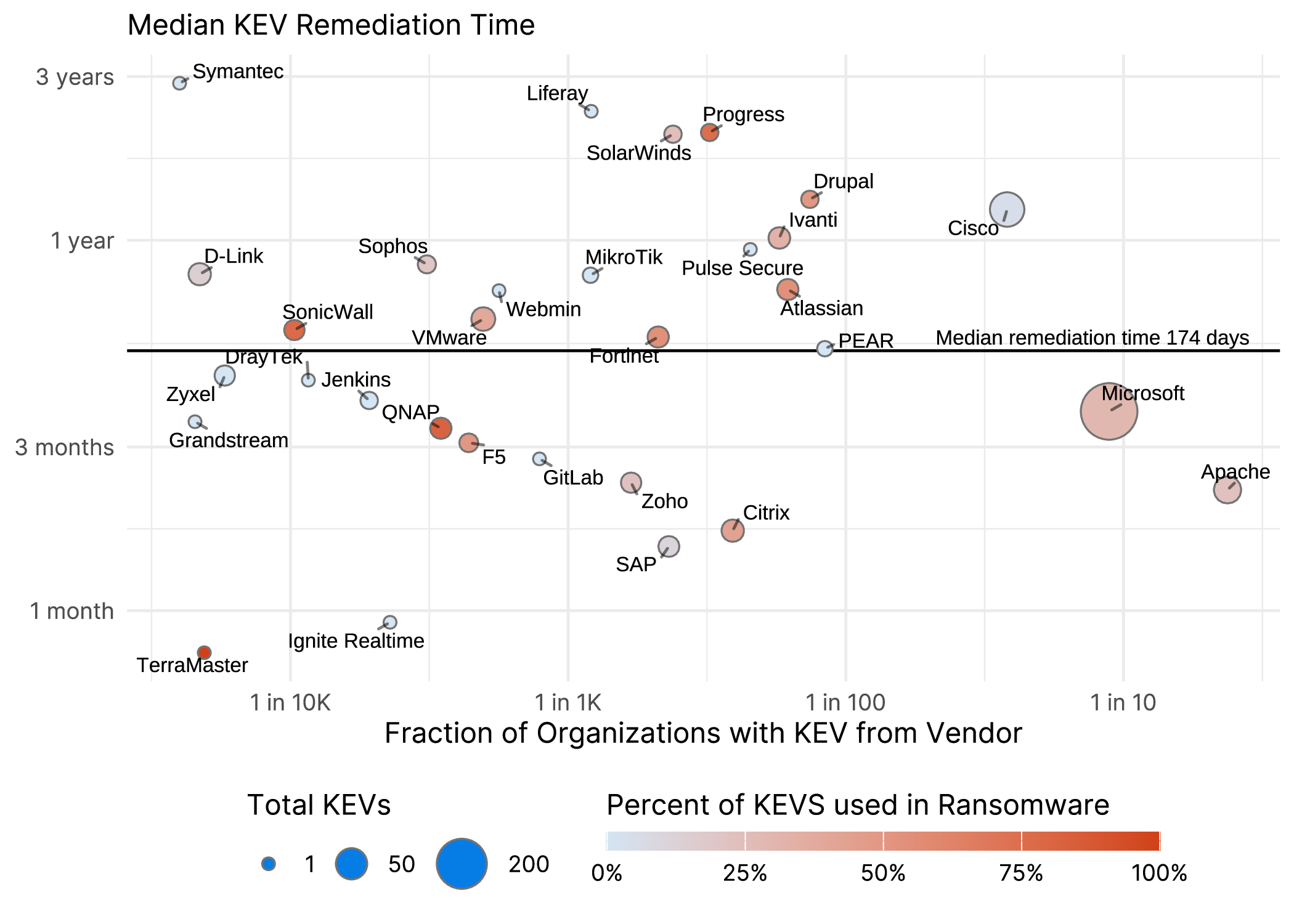
Figure 2 Vendor KEV Prevalence and median remediation time.
Again, we should be careful about what conclusions we can draw from the chart above. Microsoft and Apache being below the median time and Cisco is above doesn’t say anything about their quality. You can give an organization a patch but you can’t make them apply it. Regardless, you can find your favorite vendor3 above.
What about CWEs? First a quick primer on what exactly those are. In an attempt to en-MITRE-ify all aspects of CVE assessment a number of “Common [insert your vulnerability related noun] Enumeration” frameworks have been created. CVE being the granddaddy of them all, but Common Product Enumeration CPE is particularly useful in trying to understand exactly what software a particular CVE affects. Common Weakness Enumeration (CWE) attempts to classify exactly what went wrong when writing the initial bit of software that led to the bug. We actually talk about the completeness (or lack thereof) in a recent other bit of research.
Now, not to say that CWE’s aren’t interesting. They are! But usually to the folks writing the software, not necessarily the folks responsible for cleaning up the mess. Sometimes it’s useful for someone working in vulnerability management to understand the nature of the mistake that led to them having to get up in the middle of the night to patch some things, but usually they just want to batten down the hatches. Now there are 679 CWEs currently used in the vulnerability data today, but only 103 in the KEV data. Here are the ones that are most likely to occur.
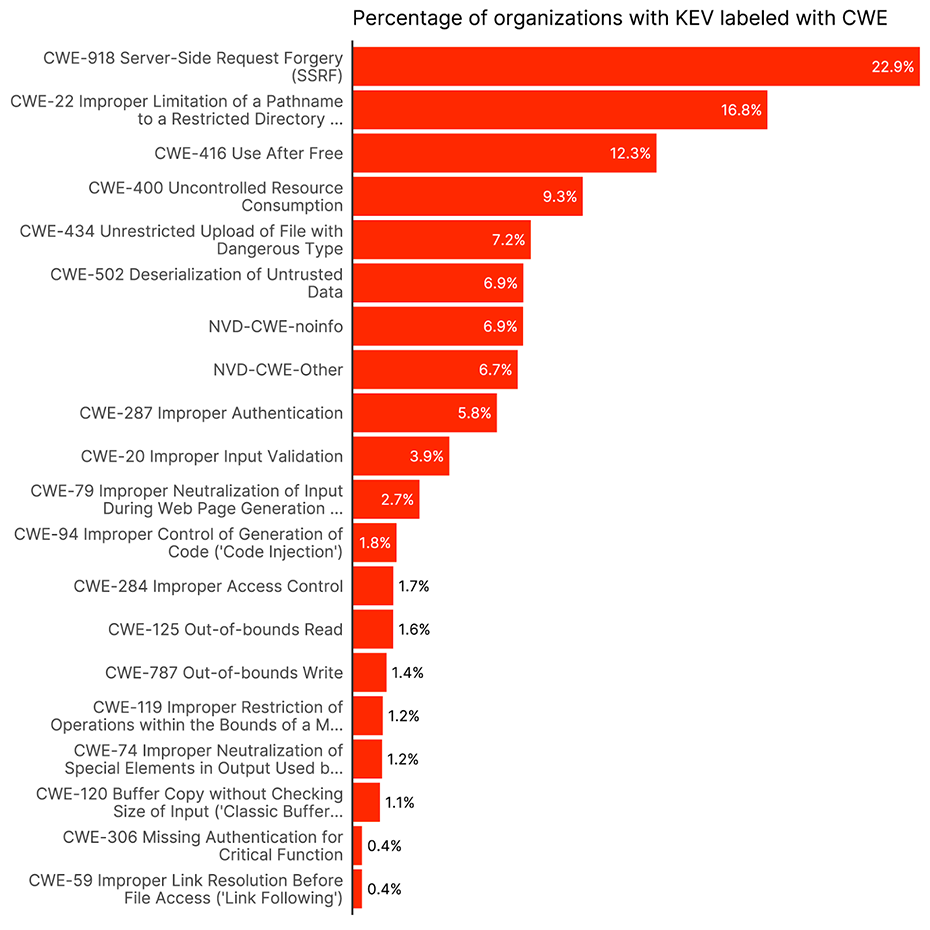
Figure 3 Percentage of organizations with detectable KEVs that have a particular CWE.
I think maybe what’s most interesting here, is that many don’t have a “good” CWE and end up with the less than informative “NVD-CWE-noinfo” and “NVD-CWE-Other”. Among the ones that have real names, we are mostly looking at problems that plague network accessible software. Of course, because I am a completist, here are all those CWEs along with their time to remediate.
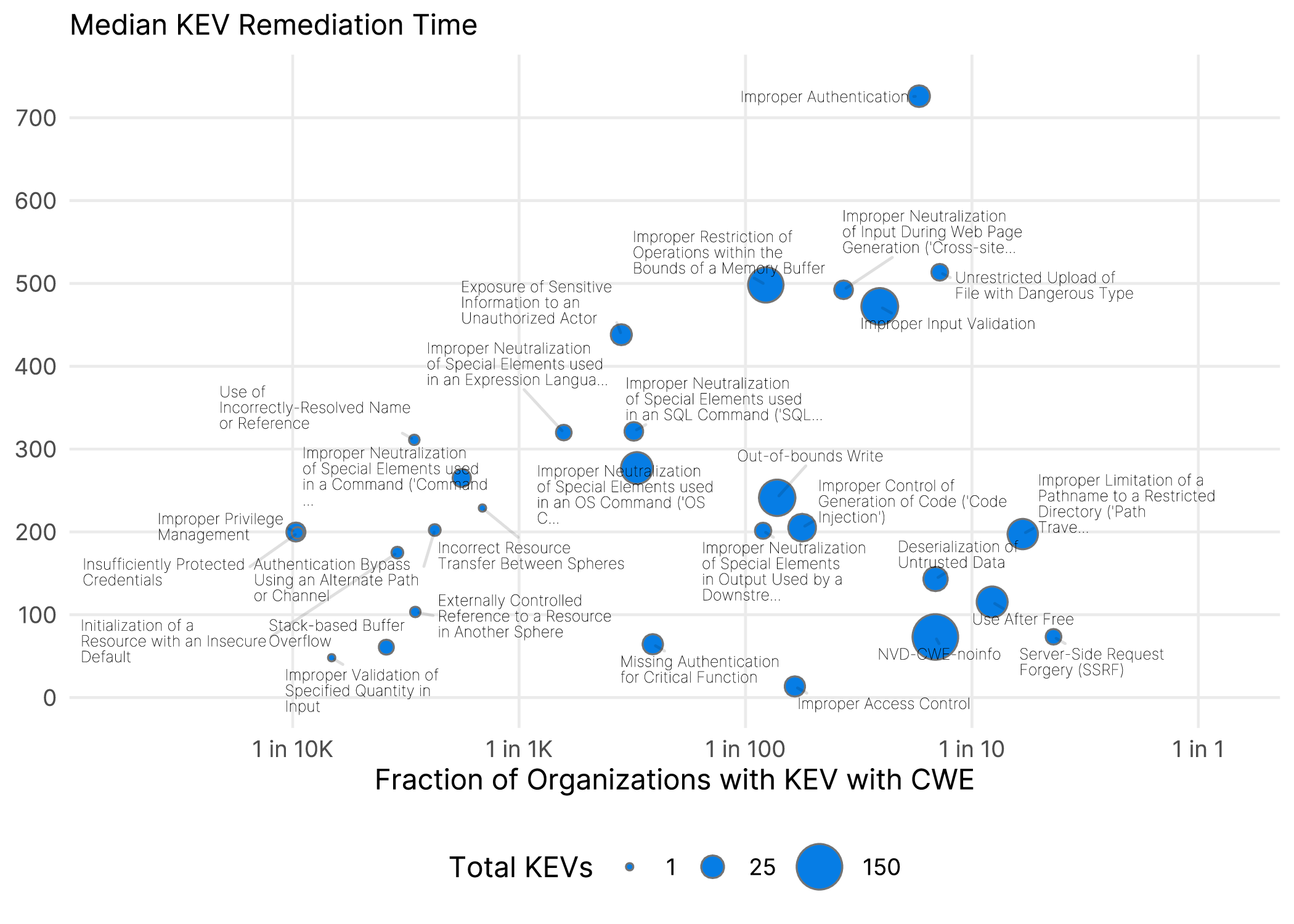
Figure 4 Prevalence and Remediation time of KEV catalog vulnerabilities broken down by CWE.
Here again we see the incompleteness of CWEs with a big honking dot for NVD-CWE-noinfo. While there is some mild correlation between the prevalence and remediation time, it’s not exactly overwhelming. Some contrasts might be though. Server-Side Request Forgery is common but gets fixed fast, driven largely by SSRF in Microsoft Exchange servers getting quickly patched, while “Improper Authentication” common-ish, but fixed at an absolute snails pace, driven largely by SolarWinds Orion and Ivanti Pulse Connect Secure seeming to stymy organizations patching efforts.
I’ll conclude here by simply saying that there are a huge number of ways to slice and dice KEVs (and CVEs in general). Some of them lead to real insights about the state of play of vulnerabilities, some are just going to be emblematic of the limited view we have of the world. Regardless, I’m always happy when something I thought was not all that interesting ends up raising someone’s eyebrows. It helps expand my worldview and starts dialogue as well as shows that what I am doing has people’s attention. So keep those questions coming and I’ll answer the best I can!
1Read: Thought Leadership.
2Whether that fix is easy to apply is a whole other conversation, and honestly a tough nut to crack.
3Do we have favorites? Is that a thing?