Two Years Later, Still at Least Twice as Likely

In 2015, Bitsight published a report, Beware the Botnets: Botnets Correlated to a Higher Likelihood of a Significant Breach. In that report, researchers discovered that companies with botnet grades of ‘B’ or lower were more than twice as likely to experience a significant data breach. Now two years since that study, researchers examined more than 70,000 organizations and found similar results, including additional risk vectors that correlate to an increased likelihood of an organization experiencing a breach. Organizations have begun to take action based on these findings by communicating with trusted third parties who are likely to experience a data breach based on their security posture.
File Sharing
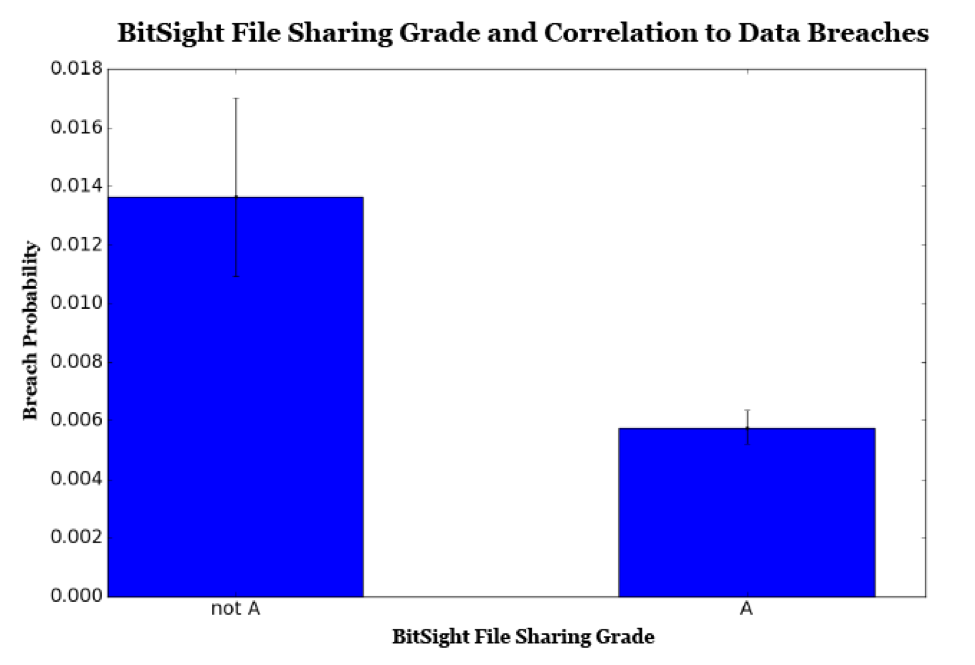
Last year, Bitsight published a Bitsight Insights report, Peer-to-Peer Peril: How Peer-to-Peer File Sharing Impacts Vendor Risk and Security Benchmarking and observed that 23 percent of companies examined had some form of file sharing activity on their networks. Although many organizations explicitly ban this activity, researchers found that in some industries, over a quarter of companies share files over the BitTorrent protocol. New findings by Bitsight show that the likelihood of experiencing a publicly disclosed data breach more than doubles if an organization has a Bitsight File Sharing grade lower than an A.
Botnet Infections
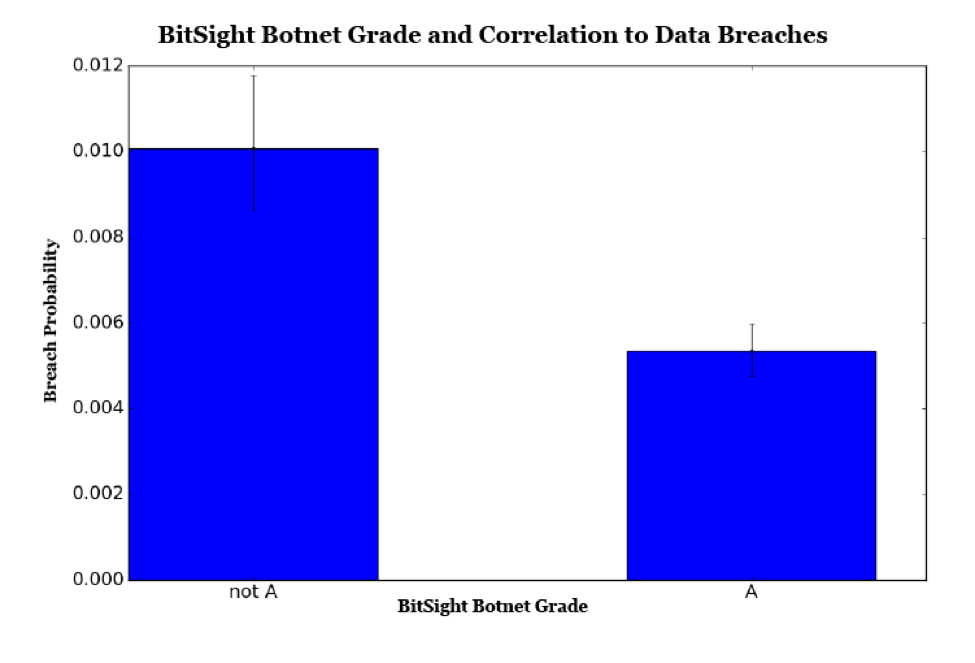
Botnets are networks of computers that have been compromised or infected with malicious software and are controlled by an adversary without the owner's knowledge. Although a botnet may not always lead to data loss, it is usually a sign that protective controls have failed and that at least some data or system confidentiality is at risk. With this year’s research, Bitsight continues to find that companies with a Bitsight Botnet grade lower than an A are nearly twice as likely to have experienced a breach.
Open Ports
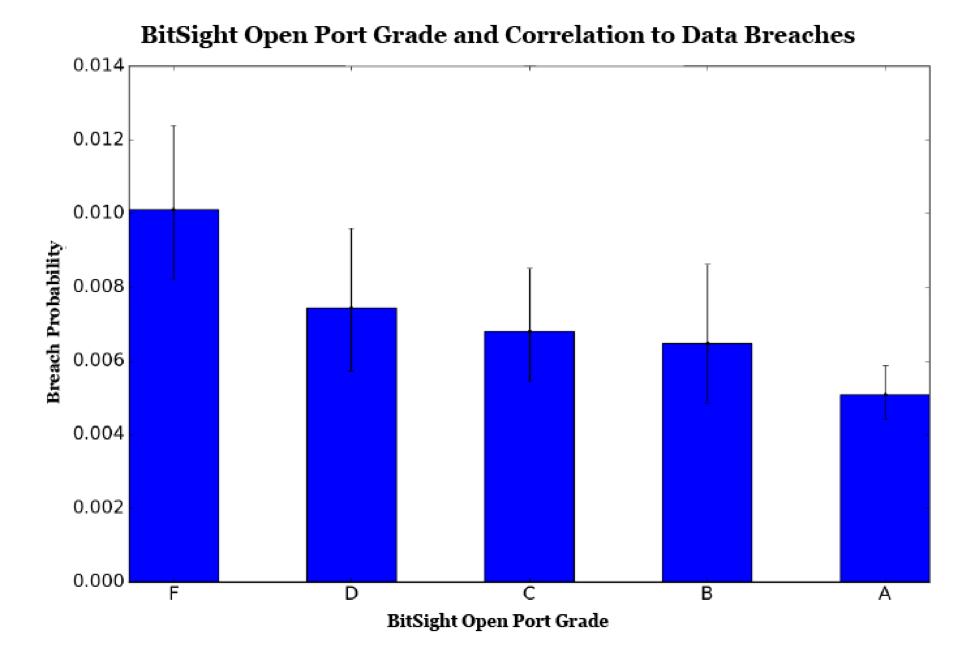
Earlier this year, a MongoDB vulnerability showed us that open ports exposed to the internet can expose organizations to cyber attacks. Organizations may be unaware of open ports on their network. Hackers can exploit this vulnerability to access a company’s sensitive data, sometimes even demanding payment before releasing the information back to the company. A study earlier this year between Bitsight and Advisen, Bridging the Gap: How Cyber Practices & Data Breaches are Connected, found that 60 percent of breached organizations had 10 or more ports susceptible to unauthorized use. Recent research by Bitsight finds that organizations with an F as their Bitsight Open Port grade are more than twice as likely to experience a breach than companies with an A.
What Can You Do?
Cyber criminals are constantly looking for weaknesses in your network. Continuously monitoring your and your vendors’ security ratings and benchmarking your performance against your industry can give you the necessary insight to bolster your network’s security. Below are some best practices to consider:
- Identify file sharing activity: Your information security team may be unaware that employees are engaged in file sharing activity. It is important that the team quickly identify instances of file sharing and take steps to block this activity from taking place.
- Continuously monitor your vendors’ cybersecurity posture: The security landscape is constantly evolving. To stay ahead of cyber threats, security and risk management teams should continuously monitor their vendors’ security performance and ensure that they identify changes in the security ratings, taking appropriate steps to remediate any issues that appear.
- Benchmark your performance against the industry. Security should not be measured in a vacuum. Organizations should establish benchmarks and compare their performance to their competitors or their industry. This approach helps facilitate cybersecurity discussions with the Board of Directors and other business line leaders across the company.
- Close unnecessary ports and fix insecure services: Unsecured protocols should be turned off or replaced with secure versions (e.g. replace Telnet with SSH). Enable authentication for services such as MongoDB (in general anything which is not a publicly used website should require authentication). When possible, use a firewall to prevent access by outside parties.