Third-Party Insight into Triada & Related Families


A few weeks ago Google confirmed that there was malware pre-installed on a number of Android devices due to a supply-chain attack. The latest installment was discovered by security researchers from Dr.Web who have been investigating this situation for several years as it was already theorized by security researchers back in July 2017 that these infections originated as part of a supply-chain attack. In this instance, these devices were pre-installed with Triada, a form of Android malware that has been studied and reported on by Kaspersky and most recently Google in its attempt to surface this critical information to users and the wider community.
Back in 2016 when Triada was analyzed by Kaspersky, it had been described as one of the most complex and sophisticated mobile malware families to date due to having the capabilities of injecting itself into the processes of other applications by compromising the core Zygote process for which each Android application is initiated. It also attempts to hide its presence by removing the downloaded modules from disk and modifying other processes to hide itself from other running applications.
The malware is also quite modular and easily configurable by the author in an attempt to monetize the injection in any way that’s suitable. While many mobile malware focus on ad fraud, Triada was focused on monetizing the botnet through sending premium-rate SMS messages at that time. Kaspersky also noted that other malware families, including Ztorg, had been used as a downloader to inject Triada onto the mobile devices. PrizeRAT, much like Triada, has also been observed to be pre-installed on mobile devices as investigated by Sophos. Triada and other mobile malware are generally installed on devices through malicious applications that were downloaded from Google Play, downloaded from untrusted third-party application stores, sideloaded by users, or included on the system image by default such as in this latest report by Forbes.
The ecosystem of low-cost Android smartphones has been suffering security and privacy setbacks for several years after numerous and continuous reports detailed various forms of device compromises, nearly all of which were compromised out-of-the-box with little ability for the user to remediate the situation without replacing their device entirely due to inaction by the manufacturer. Kryptowire reported that a number of BLU devices contained malicious code that siphoned user’s personal data and communications back to China. While a couple of days later, we reported on a potential backdoor installed on a similar set of BLU devices among many other manufacturers, including Leagoo devices. More recently, the German Federal Office for Information Security put out a statement warning about a backdoor in many Android smartphone models, which continue to mirror those mentioned in previous reports. Several years ago, Google introduced stronger standards and more rigorous evaluations the device image prior to a device being allowed to use Google applications. However, those standards do not necessarily address general backdoors not known to be associated to catalogued malware families.
Our smartphones have continued to be a bastion for sensitive information about their owners and their activity, which also extends into the corporate domain. As BYOD policies continue unfettered, the sensitive information on these devices might not be only limited to the user’s personal information. Malware such as Triada, as reported by Google and Kaspersky, and the RAT as reported by Sophos, pose clear risks to users and all data accessed and stored on those devices.
Our Insight
For the telemetry that we gather about these set of malware families, we can dive into the industries most affected by these families. We have been tracking Ztorg since November 2016, PrizeRAT since November 2018, and Triada since May 2019. It’s important to note that the telemetry we observe is not necessarily comprehensive across all botnets for a particular family, but it is a good representation of the risk profile. This is particularly noteworthy for Triada, which has manifested itself in different ways over the last couple years.
The following chart shows companies within a selection of industries that have had a compromised system on their network over the period of April, May and June, with the exception of Triada data which is only from May and June.
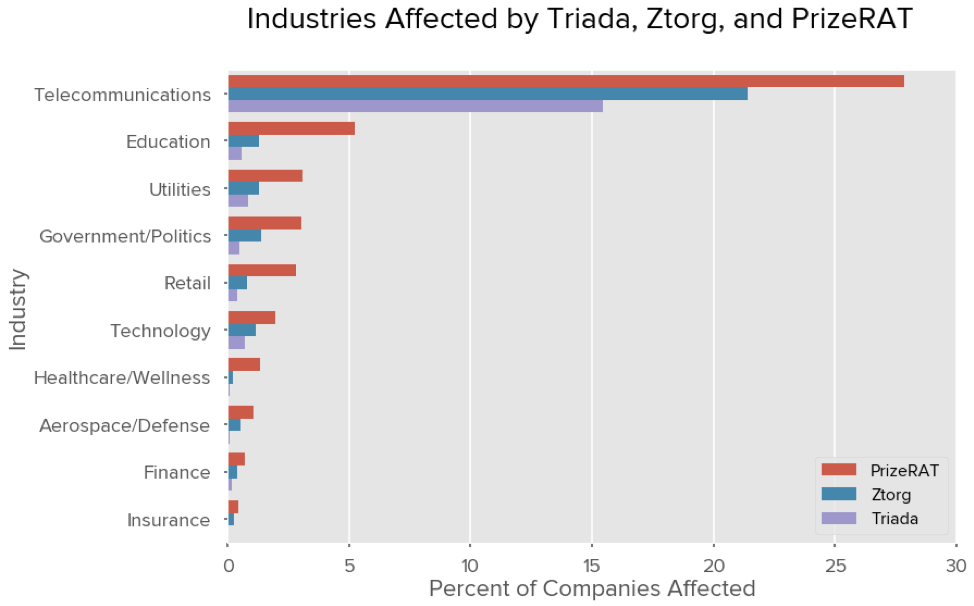
Telecommunications and Education typically lead affected industries at 15.46% and 0.57% of organizations affected by Triada due to the fact that they often provide transit services on behalf of their customers. Telecommunication companies are providing Internet service for an organization or for a residence; in Education, the largest group typically represents students. Utilities, Government/Politics, and Retail are respectively the third, fourth, and fifth most frequently observed industries with these malware families present on their network with 0.85%, 0.50%, 0.40% of companies within those industries affected by Triada respectively.
In comparison, Ztorg had a stronger impact to organizations with Utilities, Government/Politics, and Retail experiencing 1.27%, 1.40%, and 0.79% of organizations affected.
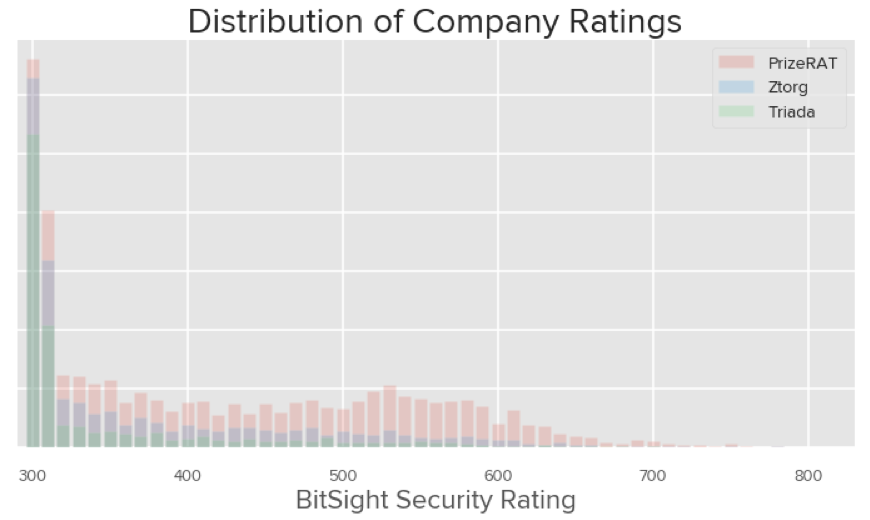
Across all industries we also observed that companies that have devices infected with these forms of malware also do a poor job in their security controls and have a lower security rating compared against the general distribution of ratings for companies that we monitor. For example, 82.7% of companies affected by Triada have a Bitsight Security Rating of 400 or lower, and 92.8% of companies have a Bitsight Security Rating of 500 or lower.
In addition, the average Bitsight Security Rating of companies affected by Triada, Ztorg, and PrizeRAT are 350, 370 and 420, respectively. PrizeRAT is not only a more ubiquitous malware family of these three for the specific botnets we’re observing, it also affects companies that have generally better security controls compared to the others.
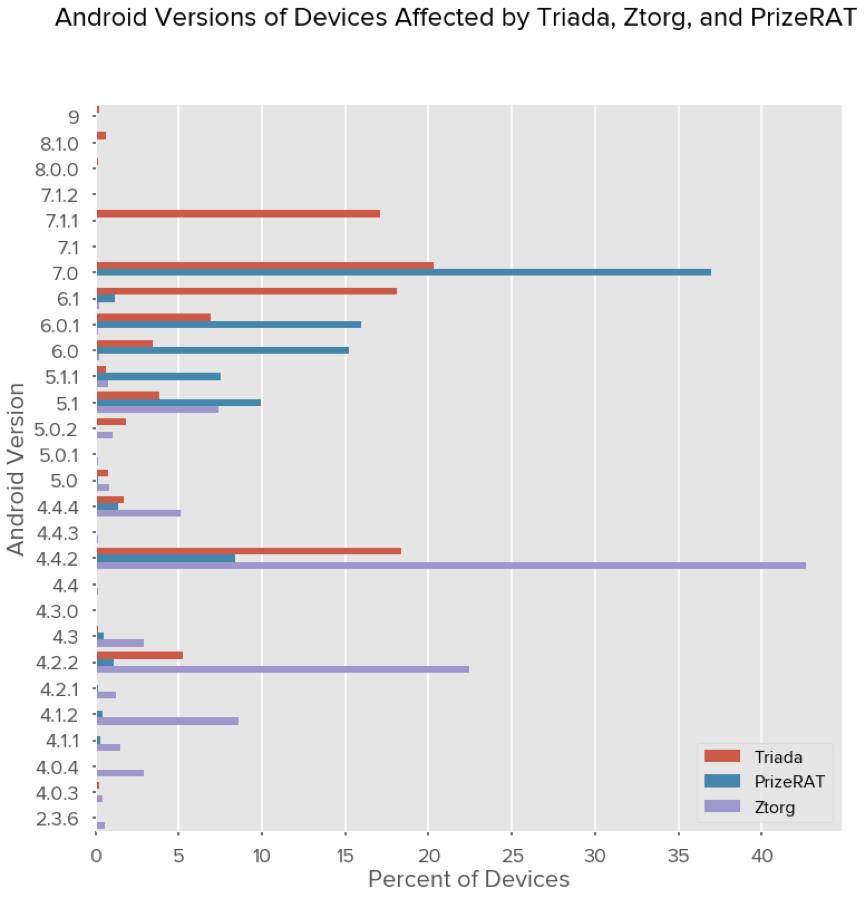
Devices infected with Ztorg are generally older devices, with nearly all of them running Android 5.1.1 or lower. On the other hand, both of the Triada and PrizeRAT botnets we are observing have infected devices running more recent Android versions, including Android 9.0.
Discovering Affected Third Parties
Telemetry regarding all three malware families (Triada, Ztorg, and PrizeRAT) is available in the Bitsight Platform, which allows customers to view these compromised devices across their third-party ecosystem.
Customers may use the “Infection” filter on the Portfolio page to select the appropriate malware of interest to understand the impact to a particular Folder, Tier, or the entirety of their Portfolio.

Once selected, the user can dive further into the “Compromised Systems” section of the Security Report of a given company to view the current infections. Since we have been tracking these families for some time it also allows for customers to be able to assess historical device compromises within those time frames as well.