Target & Neiman Marcus Are Not Alone: Malware in the Retail Sector

The past few weeks have been full of news regarding cyber attacks in the retail sector. First Target, and then Neiman Marcus. Now news outlets are reporting that three other well-known retailers may announce breaches that occurred in the past year.
The Target data breach is estimated to have affected 110 million people, up from the original estimate of 40 million. While Target has yet to disclose the exact nature of the attack, the narrative emerging from the work of security journalist Brian Krebs and other anonymous sources is that a website operated by Target was vulnerable to attack. This vulnerability allowed the attackers to install malware that provided backdoor access to Target’s internal network. Then, using this backdoor, the attackers distributed malware designed to steal information from point of sale machines in stores across the country.

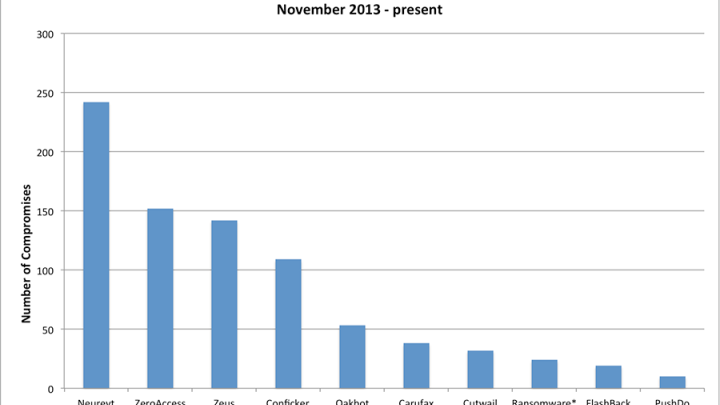
Neurevt was by far the most prevalent malware strain observed by Bitsight during this time period in the retail sector. Neurevt, which exploits Windows systems, is a trojan that steals sensitive data from a compromised machine by modifying its settings and preventing certain security processes from running. This malware, which was first reported in early 2013, can also connect to remote servers to enable attacker access to the infected machine.
ZeroAccess, Zeus, and all of their variations are the next most prevalent malware strains. Both exploit the same platform (Windows), steal data, and allow backdoor access to infected machines. ZeroAccess, also known as max++ and Sirefef, is a peer-to-peer botnet that has been around since mid 2011 and is mostly involved in Bitcoin mining and click fraud. ZeroAccess can also open a backdoor to communicate with a command and control server, which allows a remote attacker to gain control of the machine. In December 2013, Microsoft announced it had successfully disrupted the botnet, in collaboration with Europol and the FBI.
Zeus, first identified in 2007, is an evolving toolkit that includes all of the tools required to build and administer a botnet. The Zeus tools are primarily designed for stealing banking information. However, an attacker can also install any arbitrary application.
We do not know if any of these malware variants enabled compromise or theft inside of Target or Neiman Marcus; however, what is clear is that many U.S. retailers had vulnerabilities that led to compromised systems that were or are currently under the control of a remote adversary. That access is at the very least a loss of confidentiality and could result in damaging data loss for the organizations impacted. Not all of these organizations will be impacted equally and may not begin to rival the scale of the loss at Target; nevertheless, the evidence strongly suggests that Target and Neiman Marcus are not alone.
Once this type of malware is in a system, it is easier for an attacker to obtain access to valuable confidential information for considerable financial gain. As we discussed in Monday’s blog post, Bitsight observed evidence of machines on the Target network that were infected with malware capable of providing similar backdoor access. With the investigation still ongoing, we do not know if any of the compromised systems that we observed are directly or indirectly implicated in the data loss.
At Bitsight, we’ve been advocating for more transparency in the security industry. When breaches occur, we rarely learn all the details of how the attack was carried out. However, knowing how the compromise occurred, which vulnerabilities were exploited, and how the attack was discovered could actually help other organizations avoid falling victim to or recover faster from the same or similar attack.
In this spirit of transparency we have decided to share some of the analysis Bitsight has conducted on malware in the retail sector in hopes that it may help others. We will not provide information on the specific companies but rather aggregate the data at the industry level to minimize potential additional targeting of vulnerable organizations.
For those of you unfamiliar with Bitsight, we gather and process this data from hundreds of sensors deployed globally to derive daily security ratings. We do not conduct any intrusive network testing or gather any information from the rated entity.
Malware Trends in the Retail Sector
Based on our analysis of 139 U.S. retailers from November 1, 2013 through January 12, 2014 we found 1,035 distinct infections communicating out from corporate networks, 7.5 on average per company. The chart below shows the breakdown of malware activity in the retail sector. Many of these malware strains take advantage of system vulnerabilities with the objective of enabling backdoor access to corporate as well as consumer systems.


