State of BlueKeep Exposure & Insight Into Affected Systems


In the weeks since our previous post, we’ve seen development in the security community with
the release of an exploit into a commercial product as well as the announcement of the
unreleased integration of an exploit into Rapid7’s Metasploit framework. During this time, we
wanted to provide an update of affected machines, but also dive a bit deeper into the
characteristics of the individual systems that remain exposed and unpatched.
As of July 23, 2019, approximately 788,214 systems remain vulnerable, a decrease of almost 20,000 systems from July 2nd, which is a much smaller decrease than what we observed between May 31 and July 2, even when factoring in that the period between these observations is 33 days compared to the 21 days of the latest observation. Previously, the average of remediated systems between the two observations were approximately 5,244 systems per day. In the comparison between July 2 and July 23, we’ve observed a simple average decrease of approximately 831 systems per day. As such, about 81% of the exposed vulnerable systems observed on May 31 remain unpatched.
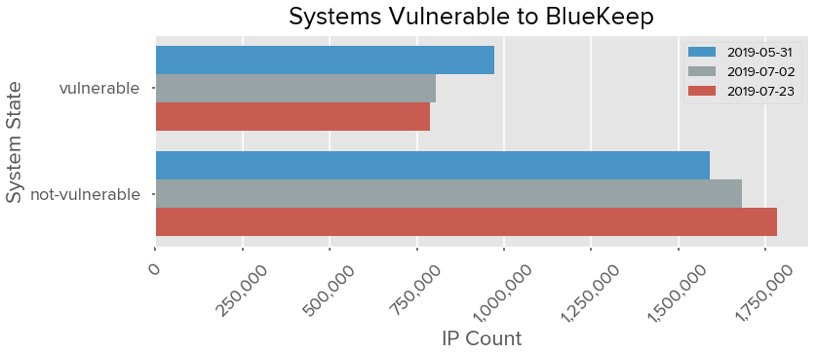 Unfortunately, we might encounter a situation where the rate of patching tapers off leaving
Unfortunately, we might encounter a situation where the rate of patching tapers off leaving
behind a legacy set of systems that remain vulnerable, perhaps unbeknownst to system
operators. A year and a half after the WannaCry attacks, there still remain systems vulnerable
to EternalBlue, and close to 11 years after Conficker was released, there are still close to
500,000 machines infected.
Industry Response
The following chart shows the percent of companies within each industry that still have a
vulnerable system exposed on their network perimeter.
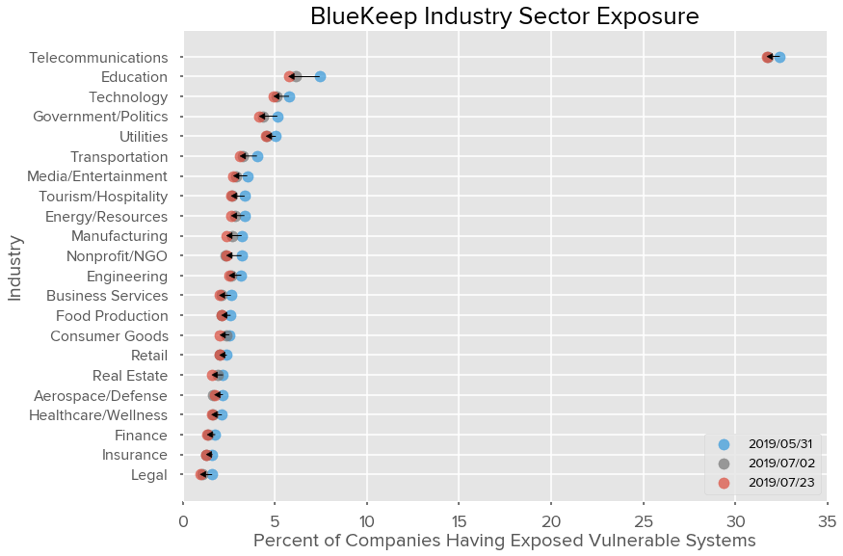 Likewise, we’ve seen slower movement in the number of organizations with BlueKeep publicly
Likewise, we’ve seen slower movement in the number of organizations with BlueKeep publicly
exposed. Real Estate, Consumer Goods, and Manufacturing have shown the largest relative
decrease (16.4%, 14.6%, 10.9% decrease, respectively) since July 2. Utilities are now the
second most affected industry (at 4.53% exposure) after Technology (at 4.94% exposure) if
Telecommunications and Education are excluded.
Geographic Changes
The following chart shows the geographic changes since our previous measurement. The x-axis
is the number of systems with BlueKeep publicly exposed on May 31, which is also represented
as the horizontal line in the middle of the chart. The y-axis measures the fraction of systems
remediated against the vulnerability relative to the country’s value on May 31st. If all exposed
vulnerable systems within a country were remediated then that country’s y-axis value would be -
1.
A blue line between measurements denotes that an improvement was made between the
observations on July 2 and July 23. A red line means a regression has occurred from the last
observation.
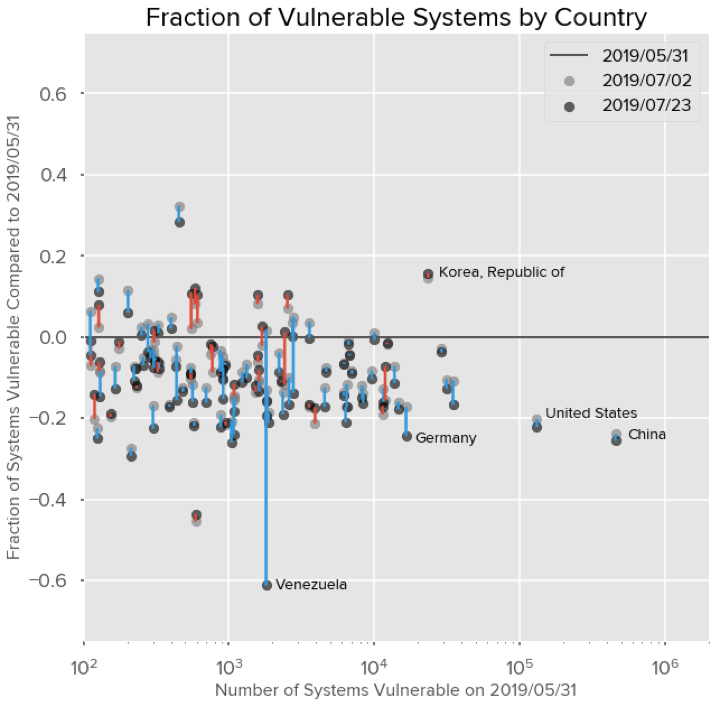
For example, about 20.2% of US-based systems were remediated on July 2 compared to May
31 and this has since increased to 22.2% as observed on July 23. For countries with over
10,000 exposed vulnerable systems on May 31, China has seen the greatest improvement with
a reduction of 25.6% as of July 23. Germany follows at a reduction of 24.3% systems with the
US afterwards.
Most countries saw an improvement in reducing the number of exposed systems that are
vulnerable, with fewer countries regressing. Minor variability is to be expected as the remote
accessibility of systems might not be guaranteed or reliable between observations.
Characteristics of Affected Systems
Beyond assessing how the number of exposed vulnerable systems have changed over time, we
wanted to begin to explore the characteristics of these systems and how those have also
changed since we have started observations. In this first endeavor, we decided to investigate
the operating system families and editions of the vulnerable systems that remain externally
exposed.
In the original announcement, Microsoft stated that Windows XP, Windows Server 2003,
Windows 7, Windows Server 2008, and Windows Server 2008 R2 and its editions were
vulnerable to BlueKeep, which aligns with what we’ve observed with our most recent analysis.
Of the 972,829 vulnerable exposed systems observed on May 31 and 788,214 vulnerable
exposed systems observed on July 23, we were able to ascertain the operating system with
high confidence for 517,654 (53.21%) and 462,923 (58.73%) systems respectively based on
attributes of the RDP protocol, such as using the visual design of the authentication screen to
infer the operating system. Results were dropped where the confidence was not high, perhaps
due to customizations by third-party products or other changes that removed the ability to
precisely determine the family and edition.
The following chart shows the distributions of each major Windows family for systems exposed
externally to BlueKeep on both May 31 and July 23. The percent cited for each family indicates
the change between the two observations. A negative percent represents a reduction in
exposed vulnerable systems.
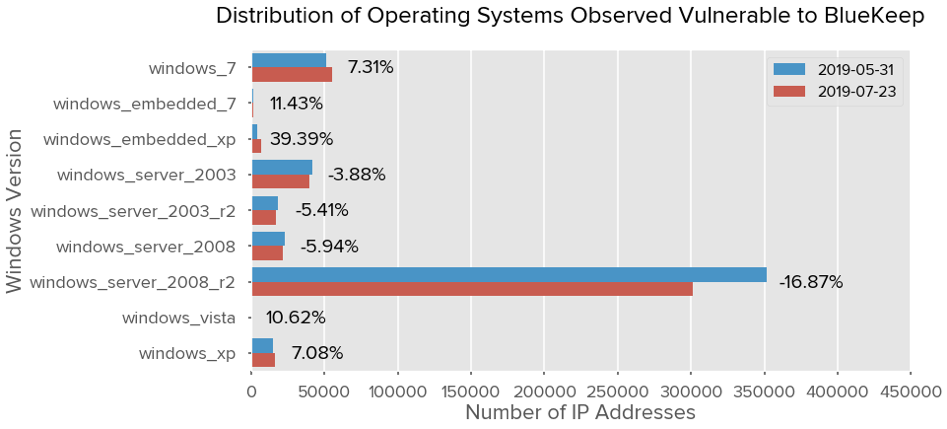
The largest family to change between these two observations is Windows Server 2008 R2,
which is also the latest family of Windows (of those that are susceptible to this vulnerability). We
also identified a non-trivial number of embedded flavors of the Windows platform susceptible to
this issue, although they make up a small fraction relative to the total population. It’s important
to note that there might be devices and systems considered to be “embedded systems”, or more
specifically, systems that generally do not have a user interacting with the core aspects of the
operating system, that are not running the embedded version of Windows. As such, this likely
reflects the minimal number of exposed vulnerable systems which are truly embedded devices
using the Windows platform.
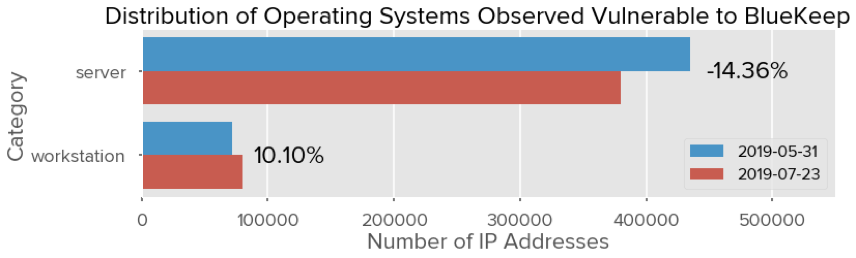
Systems running server-based operating systems saw an overall decrease in the number of
vulnerable exposed systems between these two observations, while operating systems
associated with workstations showed minimal change, and in some cases increased between
these two periods. This is easily visible in the following chart, where each Windows family and
edition was categorized into either “workstation” or “server” distributions.
Each family outlined in the earlier step is an aggregation of many Windows editions, the number
of which varies per family. For example, “Windows Server 2003” is the combination of the
“Standard”, “Enterprise”, “Datacenter”, “Web”, and “Small Business Server” editions. A full
breakdown by operating system and edition can be found below.
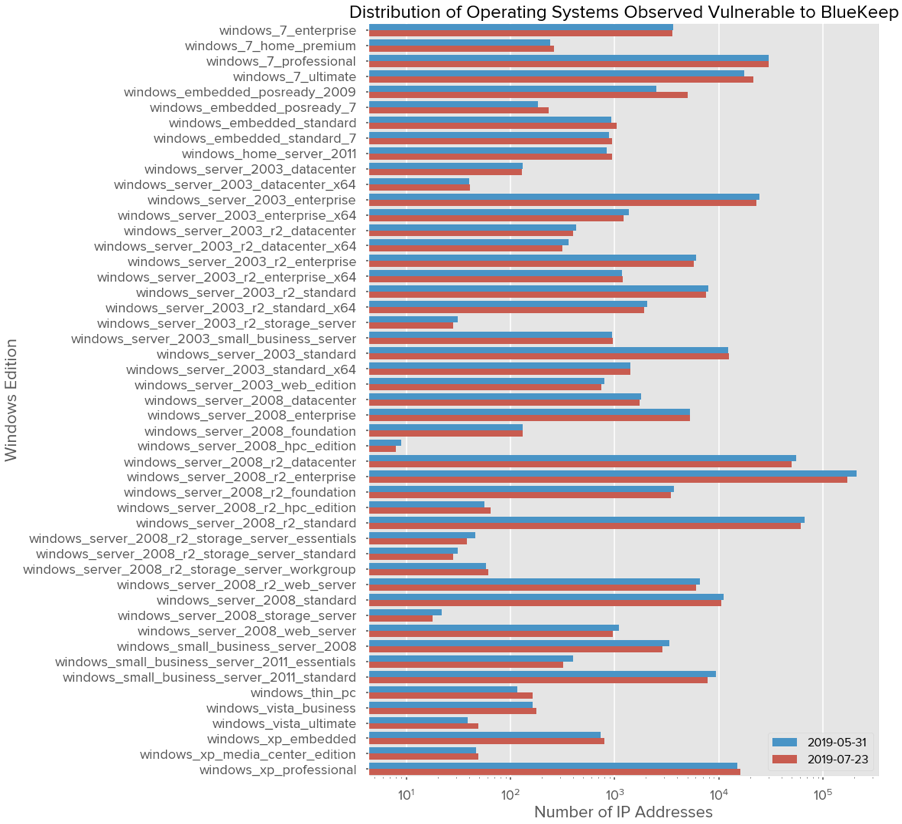 Note that unlike the previous charts, the x-axis is logarithmic, allowing better readability for
Note that unlike the previous charts, the x-axis is logarithmic, allowing better readability for
operating system editions with very few exposed vulnerable systems, such as the case of
Windows Server 2008 HPC Edition (High Performance Computing) or Windows Server 2003 R2
Storage Server.
We’ve observed the presence of nearly every edition for each Windows family affected. Most
interestingly, flavors such as Windows Server 2008 R2 HPC Edition and various Small Business
Servers are noticeably present amongst the rest of the editions. The overall popularity of
individual editions observed on exposed vulnerable systems most plausibly reflects the
popularity of the edition in the entire population of all Windows systems in the world.