Get a complete view of your digital footprint—including shadow IT and hidden vulnerabilities. Uncover gaps and secure your perimeter before attackers can find them.
Shaping our 2025 Data Engine Priorities: Industry Evolution and Customer Feedback
Tags:


The effectiveness of external attack surface management (EASM) and third-party risk management (TPRM) capabilities hinges on the depth, breadth, and timeliness of the underlying data they are based on. For this reason, Bitsight makes a significant ongoing investment in:
- Mapping the relationships between entities and assets that make up the global internet
- Observing and assessing the risk posture of connected assets
- Harnessing AI to reveal data-driven intelligence for our customers
The introduction of Bitsight’s next-generation data engine enabled many improvements to our capabilities across all of these areas throughout 2024. Critically, it also gave us the flexible and capable foundation we need to further our market leadership position as the industry evolves in new and exciting ways over the coming years.
In this post, I’ll share some thoughts on the biggest opportunities for enhanced risk insights on the horizon––and our strategy for helping customers capitalize through ongoing enhancements to our data platform in 2025 and beyond.
Key takeaways
- Attack surface management will likely evolve and converge with complementary security disciplines over the next several years.
- Bitsight’s 2025 data engine strategy will keep customers on the leading edge as this industry evolution progresses, enabling high-value product enhancements and new use cases for data-driven insights.
- Speed of data collection, asset mapping, and risk assessment will continue to be a major focus in 2025.
- We will also enrich our EASM and TPRM offerings with cyber threat intelligence (CTI), supported by our recent acquisition of Cybersixgill.
- Deeper visibility and context for assets in cloud service provider environments will ensure that our customers always have a complete picture of their attack surface.
- We will continue our ongoing efforts to refine the Bitsight Security Rating methodology with our annual ratings algorithm update (RAU), faster rating updates post-remediation, and other initiatives.
Broadening the definition of attack surface management
We’ve already proven that mapping the internet’s connected assets, linking them to specific entities, and directly observing risk indicators is an effective formula for revealing high-value insights about first-, third-, and nth-party risk. However, the impact of these capabilities is only maximized if they are integrated tightly with an organization’s broader security tool stack and remediation workflows.
According to Gartner®, “By 2027, EASM will be deployed primarily as an integrated feature of broader threat exposure management solution sets, such as cyberthreat intelligence/digital risk protection services (CTI/DRPS), adversarial exposure validation and exposure assessment platforms.”1
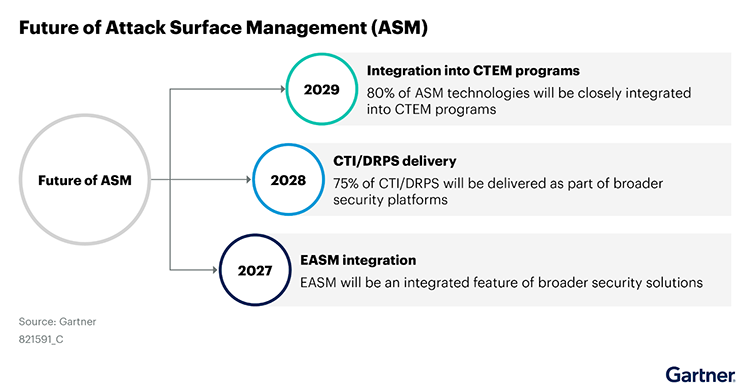
This makes perfect sense. After all, combining specific risk observables with CTI will help security teams prioritize the security weaknesses that are most likely to be targeted. Similarly, using threat data to inform CTEM and vulnerability remediation priorities will make the organizations more resilient over time.
We plan to take meaningful steps towards this vision in 2025, with a particular focus on the following themes:
- Bringing even more speed and flexibility to our core discovery, attribution, and assessment capabilities
- Adding CTI as an entirely new dimension of Bitsight’s EASM and TPRM offerings
- Further expanding our ability to discover, map, and assess the growing number of enterprise assets deployed in shared cloud service provider environments
Here’s an early preview of some of the exciting innovations we have planned in each of these areas for 2025.
Accelerating scanning, attribution, and assessment
In an earlier blog post, we provided an update on the benefits that Bitsight Groma, the internet scanning component of our next-generation data engine, is already bringing to Bitsight customers.
Notable highlights included:
- A 3x increase in our vulnerability coverage
- A 5x increase in our hostname coverage
- Typical discovery of new internet assets within 2 hours of their appearance online
- Greatly expanded coverage for specialized industrial control system (ICS) and operational technology (OT) protocols
- Significant increases in findings across key areas like web application headers, SSL certificates, and SSL configurations
You can expect to see further advances in the speed, breadth, and depth of our internet-scale scanning in 2025. One example that we’re particularly excited about is a new capability we’re developing that will provide the option for Bitsight customers to perform continuous daily scanning of their organization’s assets. This will shorten the window between when a weakness or software vulnerability appears and when the security team becomes aware of it and responds. This is critical for making the jump to true CTEM workflows with data-driven prioritization.
Using cyber threat intelligence to drive prioritization
Along with accelerating discovery of vulnerable assets, it is also essential to give security teams more signals to use to prioritize their response and remediation efforts effectively. After all, CTEM and similar frameworks are based on the premise that some vulnerabilities require more urgent attention than others. Using data to prioritize how a finite set of security resources can be deployed most effectively will maximize overall impact on risk posture.
While assumptions about asset criticality and severity of the security issue factor into these prioritizations today, timely CTI brings a powerful new dimension to the equation. Cross-referencing observed vulnerabilities collected by Groma with the latest threat information helps form a more precise assessment of the likelihood that specific vulnerable assets will be targeted by threat actors.
Our recent acquisition of Cybersixgill propels us into a leadership position in this critical area, and we plan to move quickly to bring additional context from threat intelligence into our EASM and TPRM offerings in 2025.
Contextualizing and assessing cloud-hosted assets
One of the biggest obstacles to effective EASM and TPRM is the fact that an increasing number of enterprise assets now reside in shared cloud service provider environments. This makes asset attribution challenging, since assets are provisioned and de-provisioned dynamically by the cloud providers on behalf of end users. These environments often use IP address blocks that span many different organizations.
We made significant strides in this critical area in 2024, including major enhancements to our delegated security controls model for cloud providers. In addition, we streamlined the integration process by extending support to all three major cloud service providers: Amazon Web Services, Microsoft Azure, and Google Cloud Platform.
You can expect to see further innovations in this area as well in 2025, such as:
- Additional detail about where cloud assets are located
- Identification of the specific cloud services in use
- Identification and assessment of cloud storage resources
This additional context will enhance risk management efforts by making it easier to validate that cloud resources are being deployed in accordance with security policies and proactively identifying cloud storage that is vulnerable to unauthorized access.
Refining the Bitsight Security Rating algorithm and accelerating the refresh process
As our data engine capabilities evolve, we continually seek ways to apply these improvements to the methodology we use to calculate the Bitsight Security Rating. Our annual Rating Algorithm Update (RAU) process is highly methodical and is reviewed and validated with customers over several months. This deliberate approach reflects our understanding that stability and consistency in the Bitsight Security Rating are crucial for the many organizations that rely on it to set priorities and make critical business decisions.
Planning and development is already underway for some exciting new enhancements that will be included in our 2025 RAU. The primary focus of RAU this year will be expanded coverage of important web application security issues in the Bitsight Security Rating. As in previous years, we are committed to a multi-channel, thorough communication approach to ensure customers understand and leverage the most of the RAU.
Aside from kicking off 2025 RAU, we are also excited to begin the phased rollout of our new Dynamic Remediation initiative next month. As outlined in our December preview blog post, this highly requested initiative will significantly accelerate the impact of customers’ remediation efforts on their Bitsight Security Ratings, while also giving them more control over the refresh process for their assets and findings. With this enhancement, findings observed as remediated will immediately impact the affected organization’s Bitsight Security Rating. Additionally, customers of Bitsight Security Performance Management (SPM) will have faster results from an on-demand scan when they use the “refresh” button in their findings view. Bitsight Third Party Risk. Bitsight Third-Party Risk Management (TPRM) will have access to a new “refresh” button in their findings view, empowering them to initiate an on-demand rescan. Keep an eye out for our upcoming Customer Newsletter and webinar to see first-hand how this exciting new capability works.
Enabling data-driven insights for your organization in 2025
I hope this quick preview of some of the exciting plans we have for our data platform gets you thinking about new ideas for how data-driven insights can unlock new business value for your organization in 2025. As we begin a new year, it’s a great time to assess the effectiveness of your existing security and governance workflows and look for ways to empower your team to work more efficiently and effectively.
We look forward to collaborating with both new and existing customers on this in the months ahead, whether it’s through one-on-one dialogue with our customer success team, feedback and input to our product team, participation in beta programs, or all of the above.
1 Gartner, Emerging Tech: The Future of Attack Surface Management, By Ruggero Contu, Jonathan Nunez, 25 November 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.


