Ransomware Cyber Attacks: Which Industries Are Being Hit The Hardest?
Tags:


Ransomware is rapidly becoming one of the most common forms of malware distributed on systems all over the world.
Its rise to power is attributed to several things:
- First, it’s a relatively straightforward form of malware in terms of its capabilities.
- Second, ransomware provides malicious actors with a more direct conversion of revenue than other malware attacks.
- Finally, it’s effective: the FBI reported that ransomware cyber attacks brought in a combined $1 billion in 2016.
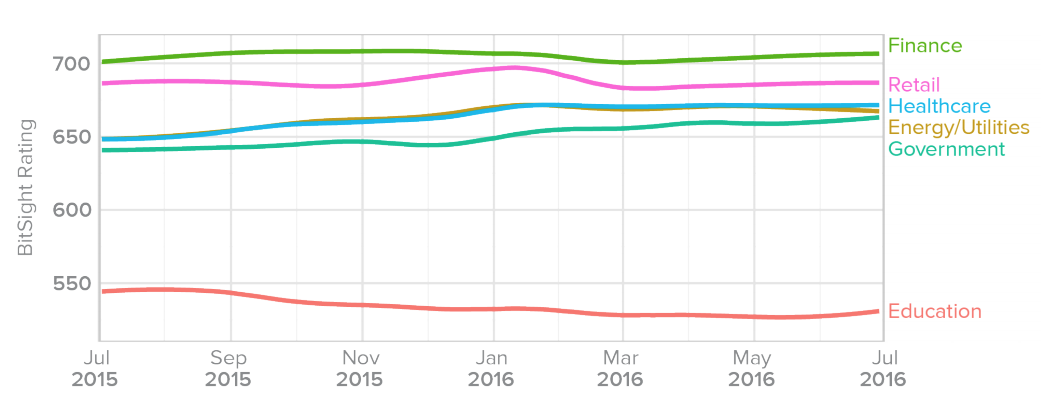
In late 2016, Bitsight released its Insights report on ransomware. To create this report, Bitsight researchers analyzed the growing trend of ransomware across nearly 20,000 companies worldwide. They identified, among other things, which industries are most susceptible to these types of attacks. Bitsight’s researchers found that education, government, energy and utilities, and healthcare industries were most susceptible, as corroborated by their Security Ratings:
Some more recent studies—like NTT Security's 2017 Global Threat Intelligence Report—have emphasized that sectors like “business and professional services” are particularly vulnerable to ransomware as well. Thus, it’s important to remember that every industry could be susceptible to a ransomware attack. To better understand the criticality of ransomware cyber attacks and the impact these attacks have already had on many vulnerable industries, take a look at the industries (in no particular order) below:
1. Healthcare

Ransomware can be particularly troublesome for industries that have a lot of time-sensitive materials on corporate systems, or those that can’t handle being offline for extended periods of time. Unfortunately, healthcare fits both bills. If a number of machines in a hospital go offline because of a ransomware infection, this forces hospital operations to go down—and that could impact lives. Malware authors are aware of this—and since they’re looking for the quickest payout they can—hospitals could potentially be targeted more frequently.
According to this Recode article, U.S.-based drugmaker Merck was impacted by the massive NotPetya ransomware attacks in 2017, as was Heritage Valley Health Systems (a healthcare network in Pennsylvania). And in fact, one surgery at one of the hospitals associated with Heritage Valley had to be postponed as a result. And in a seperate August 2017 attack, the Erie County Medical Center in New York was hit with a ransomware attack that took the trauma center offline for 6 weeks.
2. Education
At the time the Insight study was conducted, Bitsight researchers found that education had the highest rate of ransomware cyber attacks out of all industries examined. In fact, educational institutions had more than three times the rate of ransomware found in healthcare and more than 10 times the rate found in finance.
Unfortunately, educational institutions may be more vulnerable to ransomware cyber attacks simply because they have less control over devices that connect to their networks. A student could bring a malware-infected laptop onto campus and compromise several other systems. Organizations like finance, however, are likely more resilient because they have more enforceable restrictions when it comes to endpoint security and network policy.
According to this Newsweek report, security company SentinelOne questioned universities across the U.K. in 2016 and found that 63% had been hit with ransomware at one time or another. And ransomware isn’t only impacting higher education—school districts and K-12 schools have also been impacted.
3. Government
TT Security's 2017 Global Threat Intelligence Report—as reported in this Dark Reading article—found that 17% of current ransomware cyber attacks are targeted at the government. Keep in mind that Bitsight’s Government industry sector doesn’t only contain federal government organizations, but also state and local municipalities. While smaller government bodies seem more likely to be victimized by ransomware (due to budget, operations, and overall infrastructure), that’s not always the case. For example, the city of Newark, New Jersey, was hit with a ransomware attack in April of 2017, and on a larger scale, the Ukrainian government was also attacked in the NotPetya attacks in 2017.
4. Energy & Utilities
Energy and utility companies are interesting targets, as they can sometimes fall victim to malware (or ransomware) attackers who are particularly interested in damaging a particular city, state, or country. At the same time the Ukrainian government was hit with a ransomware attack, Ukrainian power companies were also impacted. In fact, this Forbes article exclaimed that NotPetya took out the whole power grid in Ukraine during the widespread attacks in spring 2017.
This UtilityDive article describes how the power sector is reacting to the recent wave of ransomware cyber attacks. Additionally, they report that U.S. energy services company Avangrid “severed external communication ties with their international subsidiaries in an effort to ward off any infection from the malicious software.”
Consider Your Ransomware Remediation Strategies & Why They Might Not Be Effective
Regardless of what industry you operate in, the data and findings above highlight the need for a ransomware plan and remediation strategy. There are several things you can do if you’re infected with a ransomware attack—and the first question on anyone’s mind is whether or not to pay. We, along with various government agencies, do not recommend paying the ransom. There are a notable number of cases in which ransoms have been paid but companies do not recover their data.
There are some legitimate remediation strategies you have at hand based on best practices within the field—starting with backing up and restoring your data. To do this, you’ll need a good backup strategy in place so you can retrieve the uninfected data in case of an attack.
Even so, be aware that relying solely on backed up data may be an inadequate strategy, as malware authors are starting to create ransomware families that also encrypt various backup solutions before infecting computers. If this happens to you and you attempt to restore your data with a backup, you would be unable to do so as that version would already be encrypted. This isn’t yet considered a popular ransomware cyber attack method, but it’s something to be cognisant of as you refine your remediation strategy and determine the best way to overcome a potential ransomware disaster.
If you want more background information about ransomware, or any additional data and statistics from our Bitsight researchers, download this Bitsight Insights report today.