Pre-installed Android Threats: Data Insights
Tags:


We used to think of malicious software — or malware as it’s more commonly known — as a threat to laptops and desktop computers. But as we are increasingly using mobile devices for many important things in our daily lives such as banking, cybercriminals are targeting smartphones and tablets more often. Consequently, Apple iOS and Android, which are the most popular mobile operating systems, have become targets for cybercriminals. Android still remains the most targeted because it has more market share and it’s open source, contrary to its direct competitor.
Potentially Harmful Applications (PHAs) are Android apps that can put users, user data, devices and, ultimately, companies at risk. Data exfiltration or even destruction of data and/or physical assets may cause considerable damage to organizations. These apps are often generically referred to as malware. Pre-installed PHAs are a trend that security companies have frequently investigated and reported about. Earlier this year, pre-installed malware was found on US government-funded smartphones. Going back to the Android threat landscape of 2018, Google reported a considerable increase of PHAs:
“Malicious actors are increasing their efforts to embed PHAs into the supply chain using two main entry points: new devices sold with pre-installed PHAs and over the air (OTA) updates that bundle legitimate system updates with PHAs. Neither entry point requires action from users. (...) The developers of pre-installed PHAs only need to deceive the device manufacturer or another company in the supply chain instead of large numbers of users, so it’s easier to achieve large-scale distribution. (...) Pre-installed PHAs can gain more privileged access to the device, so it’s easier to execute malicious behavior that would usually be blocked by Android’s security model”.
PHAs are usually pre-installed in low-cost devices from budget vendors with a weak control over the software that is installed in their devices. In June 2019, Triada malware, which Bitsight has visibility into, was found pre-installed in some low-cost devices. In August 2019, at BlackHat, Google again talked about the importance of this trending threat.
Managing mobile device security and the data stored on them is still today one of the biggest challenges organizations face. On one hand, the users demand the ability to use and choose their own devices with little or no concern over the security of their choices. On the other hand, businesses demand that employees are constantly reachable, keep their emails on mobile devices, or use mobile applications that process and store other business data. Companies allowing employees to store company data on devices with pre-installed PHA could be allowing malicious outsiders to access company information on those devices. The same is true for companies that use mobile applications as a means to interact with their users. In fact, employee‑owned devices were culpable in 51% of corporate data breaches in 2017, according to an AT&T report. In addition, nearly one‑third of senior executives surveyed by PwC cited mobile devices as the leading cause of their organization’s security breaches. It is clear that companies must rethink their enterprise mobility policies.
Bitsight is able to obtain a unique view at how these mobile threats are growing due to its long-running sinkhole operation. Currently, we observe connections from over 20 million IPs used by compromised/insecure systems/devices daily. Since we first sinkholed a mobile botnet in 2014, the number of mobile botnets observed through our sinkholes has constantly increased, and currently, a large part of the compromised systems we observe are mobile devices. Specifically regarding Pre-installed Android Threats, we observed daily connections from over 3.4 million IPs used by devices that are affected by at least one of the following threats:
- Cooee - Trojan pre-installed on some Phillips smartphones that displays annoying advertisements and downloads and installs different software without user knowledge. In a period of 24h, we observed connections from over 1m unique IPs.
- PrizeRAT - Remote access trojan (RAT) pre-installed on some uleFone smartphones that silently sends SMS messages to a list of hard coded numbers without the user's consent in order to receive instructions from their command and control server. It also collects personal information, such as phone numbers and geo-location. In a period of 24h, we observed connections from over 340k unique IPs.
- SSuggest - Stock app pre-installed on old Samsung smartphones which can be a vector to push malicious apps directly on smartphones. In a period of 24h, we observed over 220k unique IPs.
- RagentekOTA - Insecure implementation of an OTA (Over-the-air) mechanism for device updates, associated to the software company Ragentek Group, affecting low-cost devices from BLU, Infinix, Doogee, Leagoo, and Xolo brands. It allows adversaries to remotely execute commands on the devices as a privileged user if they were in a position to conduct a Man-in-the-Middle attack. In a period of 24h, we observed connections from over 100k unique IPs.
- ActivateTBKS - TCL stock app pre-installed on some TCL and Alcatel smartphones that has the capabilities to silently install and uninstall other apps and also infiltrates device and user data. In a period of 24h, we observed connections from over 2m unique IPs.
The threats mentioned above make an interesting sample since they cover different types of threats (e.g. trojans, RATs and backdoors). We’ve aggregated all botnet events from the previously mentioned threats from a timeframe of 24h. The following chart shows the top 25 countries most affected by these Android threats.

By a large difference, Brazil is the most affected country with nearly 600k unique IPs daily contacting our sinkhole, followed by Russia with around 200k IPs and India with around 170k IPs. Brazil, Russia, and India are in the top 5 countries with most smartphone users, according to Newzoo's Annual Global Mobile Market Report, and are in the top 4 largest emerging markets, which may explain the amount of low-cost devices in those countries.
Looking at the industry perspective, the following charts show the most affected industry sectors. The Telecommunications sector represents 90% of the IPs that communicate with us due to the fact that mobile devices often communicate through cellular networks, so most of the IPs are from ISPs.
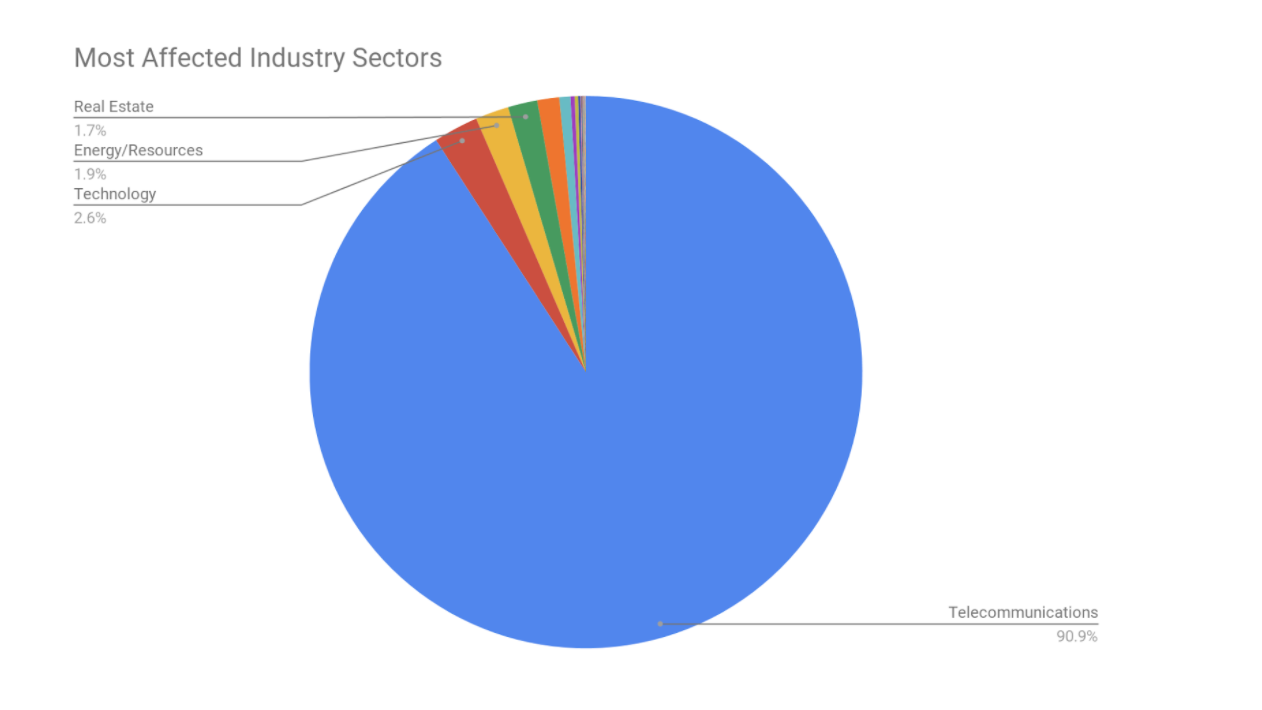
In order to better compare industry sectors, the following chart shows the top 10 most affected, discarding the Telecommunications sector:

Technology, Energy/Resources, and Real Estate are the most affected sectors. Critical sectors, such as Finance, seem to also be affected by these threats. We can also observe that there is a vast disparity between the top and the bottom sectors.
Companies affected by these kind of threats may need to improve some security controls, such as their Inventory and Control of Hardware Assets, their Secure Configuration for Software on Mobile Devices, and their Malware Defenses, in order to have enhanced device and network protection against these threats, consequently lowering the probability of having a security incident. We recommended the following tactics and tools to be deployed by CISOs in order to proactively mitigate risk:
- Establish or enforce/rethink enterprise mobility policies, such as Bring Your Own Device (BYOD), Choose Your Own Device (CYOD), Company Owned/Personally Enabled (COPE), and Company Owned/Business Only (COBO);
- Consider mobile device management (MDM) software, regardless of whether employees use their own device or one provided by the company. A typical MDM toolset will monitor not just devices but their connected networks and the data they send and receive;
- Protect endpoints with anti-malware or other endpoint protection solutions;
- Educate employees about mobile choices and corresponding risks.