Poodle is Back! TLS Targeted by New Vulnerability

 Last October the world was alerted to Poodle, a vulnerability on websites and servers running SSL 3.0. Acting as a "man in the middle," would-be attackers could compromise the secure connection between a browser and a website, and inject JavaScript that enabled them to view these communications, stealing unencrypted data and manipulating traffic flow. The apparent fix at the time was to upgrade from SSL 3.0 to TLS, but new research suggests this may not be the case.
Last October the world was alerted to Poodle, a vulnerability on websites and servers running SSL 3.0. Acting as a "man in the middle," would-be attackers could compromise the secure connection between a browser and a website, and inject JavaScript that enabled them to view these communications, stealing unencrypted data and manipulating traffic flow. The apparent fix at the time was to upgrade from SSL 3.0 to TLS, but new research suggests this may not be the case.
In an article published on December 8, Ivan Rystic of Qualys describes a new version of this vulnerability which attacks TLS: "The main target are browsers, because the attacker must inject malicious JavaScript to initiate the attack. A successful attack will use about 256 requests to uncover one cookie character, or only 4096 requests for a 16-character cookie. This makes the attack quite practical." This is an issue which is estimated to affect 1 in 10 websites. On the Imperial Violet blog, the author, Adam Langley, states that "everything less than TLS 1.2 with an AEAD cipher suite is cryptographically broken."
So far, researchers have only mentioned two vendors whose products are affected by this issue- F5 and A10 Networks. F5 has issued the following guidance for their customers, but we've yet to see news from A10 Networks. Langley has also observed some "odd behavior" on Citrix devices, but says they are "unable to make an attack out of it."
To see if your site is vulnerable to this latest attack, you can check your domain using the Qualys SSL Labs Server Test, available here. Vulnerable sites will receive an F and the scan will report "This server is vulnerable to the Poodle attack against TLS servers." To test this, I scanned a few popular websites and observed the following results for several banks:
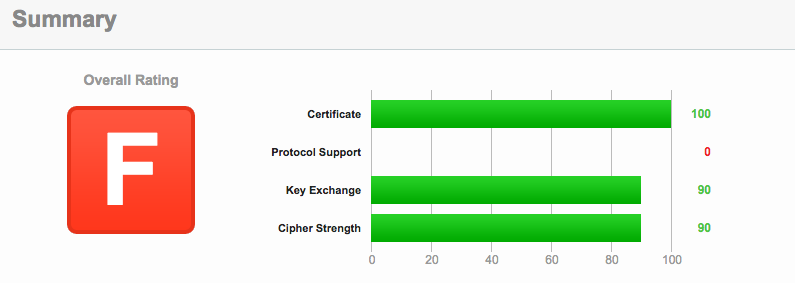
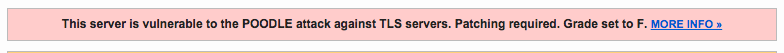
Of course, the first thing companies should do is test to see if their own sites are vulnerable to this latest version of Poodle. However, it's also worth considering whether vendors in your information supply chain are also at risk. While the presence of this vulnerability does not mean your network or vendor has been exploited, it's important to take steps to remediate this issue before an exploit does occur. According to Ivan Ristic, "As problems go, this one should be easy to fix."
