A look into Web Application Security


In today's digital age, web applications are the backbone of many businesses, supporting and managing a vast array of sensitive information, from personal details and financial records to critical business data. When we think about any company that we want to know more about, the most common question is: “what is their website”?
But web applications are not just about traditional websites, they encompass far more than just the pages you go to when browsing the Internet. These applications are powerful tools that drive critical functions across various sectors, seamlessly integrating complex processes and providing interactive experiences.
Web applications can be platforms for enterprise resource planning (ERP), managing everything from supply chain logistics to human resources and financial operations. They serve as the backbone for customer relationship management (CRM) systems, helping businesses manage interactions with current and potential customers, streamline processes, and improve profitability. They enable electronic health records (EHR) systems, allowing for the efficient, secure management of patient data. They facilitate telemedicine services, giving patients access to medical consultations and treatment from the comfort of their homes. Learning management systems (LMS) support online courses, virtual classrooms, and digital libraries. Web applications are integral to e-commerce platforms, handling everything from product listings and shopping carts to payment processing and order fulfillment. They also power the very famous and so-called social media platforms, content management systems, and collaboration tools like project management software, video conferencing, and cloud storage solutions. The examples are vast and we use web applications for most online actions that we take, either knowingly or unknowingly.
This web application dependency of the modern world brings along unavoidable cybersecurity risks. If web applications aren't properly secured, they become vulnerable targets for cyber attackers, leading to breaches that can result in the consequences we all came to know in the last couple of decades: financial loss, compromised data, reputational harm, compliance fines, to name a few.
Bitsight’s approach
Properly assessing web application security is hard. There is no substitute for a comprehensive, human driven, security audit when it comes to making sure a web application is as secure and resilient as possible. And even so, more often than not, new vulnerabilities keep popping up, sometimes in critical components used by many different applications, creeping up the supply chain.
There are, however, clear indicators that can be gathered when it comes to understanding if good security practices are being followed by any given web application and, in fact, many of those can be gathered remotely. The Open Web Application Security Project (OWASP) offers a wealth of knowledge and guidelines for developing secure web applications. A cornerstone of their work is the OWASP Top 10, a commonly used list identifying the most critical security risks facing web applications. By focusing on these top threats, businesses can prioritize their security efforts and substantially mitigate the risk of attacks.
Our approach to web application security metrics involves leveraging the OWASP Top 10 as a foundation for our assessments. These assessments are meticulous, providing detailed forensic data and tailored remediation strategies for identified vulnerabilities.
Web Application Headers risk vector
If you are a Bitsight customer for a while now, you are probably familiarized with this risk vector. If you don’t know what Bitsight's risk vectors are, head here for a quick intro. The Web Application Headers risk vector analyzes security-related fields in the header section of communications between browsers and an application. The headers define where the exchanged data is going and who it’s from, date sent, what type of message it is, and other configuration options. They're included in all back-and-forth communications between applications.
Correctly configured headers help protect against malicious behavior, such as man-in-the-middle (MITM) and cross-site scripting (XSS) attacks, and can prevent attackers from eavesdropping and capturing sensitive data, such as credentials, corporate emails, and other customer data. By looking at them we can also analyze other details, such as mixed content, insecure authentication or page redirects.
By scanning the Internet at scale, we gather information about many of these headers and evaluate if they are being correctly used. The headers we are currently measuring include:
| Cache-Control | Content-Security-Policy | Expires |
| HTTP Strict-Transport-Security | X-Content-Type-Options | |
| Location | Set-Cookie | WWW-Authenticate |
| X-Frame-Options | X-XSS-Protection |
There are more headers, but these are the most important to assess when it comes to security. After all those have been collected, the findings are graded in the usual scale (GOOD, FAIR, WARN, BAD,NEUTRAL), weighted and sent to our ratings algorithm for a final risk vector grade.
Web Application Security risk vector
Web Application Security, notice that is Security and not Headers, is a newer risk vector that extends the Web Application Headers. Let me first be clear that this risk vector does not currently affect security ratings, but is being evaluated for a period before being factored into our security ratings. The Web Application Security risk vector is assessed by loading a domain in a web browser and capturing the complete page response. Bitsight captures the entire response of the page load, including redirects and all dynamic page content, and performs a set of assessments on that response. We do not crawl the loaded page for additional responses. We also do not send out specific requests to trigger or identify vulnerabilities that may be present on the web application. Instead, our methodology focuses on evaluating vulnerabilities without actively exploiting them. This is important, as we always strive to have the minimal impact possible in any scanning or assessment activities we conduct. The assessments cover areas such as components with known vulnerabilities, broken authentication and access control, sensitive data exposure, cross-site scripting prevention mechanisms, and security misconfigurations.
The reason why the Web Application Security risk vector enhances the Web Application Headers is the usage of an actual browser (a headless browser to be more accurate) in order to access the data in a certain website and simulate real user behavior. Using a browser instead of a simple connection offers many advantages:
Comprehensive Response Capture
Browsers capture the entire response of a web page load, including redirects and dynamic content that may not be visible with simple connection methods. This ensures that all elements of the page are evaluated, providing a more thorough assessment.
Dynamic Content Evaluation
Modern web applications often rely on JavaScript and other dynamic content to load parts of the page. Browsers can execute this dynamic content, which helps in identifying issues that only manifest when the full page is rendered as it would be for a user.
Detection of Third-Party Libraries
Browsers load all resources linked in the page, including third-party scripts and stylesheets. This can reveal risks associated with third-party content, such as libraries with known vulnerabilities or insecure external resources.
Accurate Context
By using a browser, assessments can consider the context in which vulnerabilities appear. For example, issues with Cross-Site Scripting (XSS) prevention like cross domain subresource integrity check, or Content Security Policy (CSP) can be more accurately evaluated when the page is fully rendered as intended.
Real User Simulation
Using a browser simulates the experience of a real user, providing insights into security issues that could affect end-users. This includes identifying mixed content warnings, insecure cookies, and other issues that might not be apparent with a simple HTTP connection.
Other Security Features
Browsers incorporate security features like SameSite cookie attributes, CORS policies, and HTTPS enforcement, which can be tested during the assessment. These features help in identifying misconfigurations and security gaps that might not be evident with basic connections.
Assessments
To sum it up, using a browser provides an even more detailed and accurate picture of the security posture of a web application by leveraging the full capabilities of a browser to simulate real-world users and allows us to observe and evaluate the full dynamic content of modern day web applications. This enables us to conduct a wide range of tests and assessments. The comprehensive list of every aspect we test currently is large, but the assessments can be grouped into five distinct categories.
|
Category |
Description |
|---|---|
| Validation of security measures such as SRI and CSP to ensure no malicious remote resource is included on a web application. | |
| Components with Known Vulnerabilities | Using a library with missing security patches can make your web application exceptionally easy to abuse, making it crucial to ensure that any available security updates are to be applied immediately. |
| Broken Authentication and Access Control |
Access control policies ensure that users cannot act outside their intended permissions. |
| Sensitive Data Exposure |
Ensuring application design includes controls to reduce the exposure of critical and sensitive information. |
| Security Misconfiguration | Assessment of web application implementations regarding security hardening or unnecessary features and privileges. |
Each vulnerability or bad practice is analyzed, each assessment graded in the usual scale as before, weighted and the results are used to determine an overall risk grade for this risk vector. Not all assessments have the entire GOOD, FAIR, WARN, BAD or NEUTRAL rating values range. Some findings have only one or two possible values. For example, “HTTPS to HTTP redirects”, all instances of this finding are always BAD. There is no in between. If you want to learn more about the assessments and how they are graded, you can consult our knowledge base.
In terms of OWASP Top 10 coverage, there is also a clear coverage increase, as we can see in the below comparison table between Web Application Headers and Web Application Security:

Observations
Looking at all the observations that we have been gathering about millions of websites, across all different industry sectors, we can paint a picture on how the Web Application Security landscape looks like. Each month, we are currently recording and grading over 200 million observations in total, in all our different assessments.
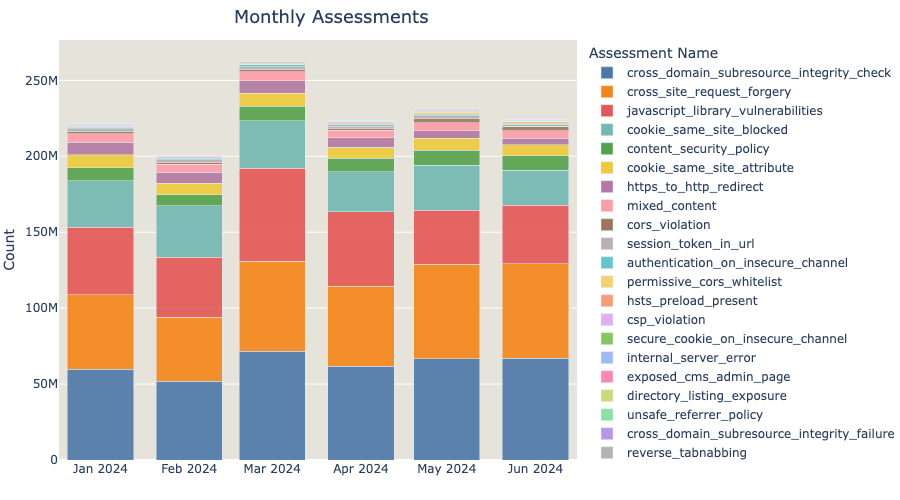
The above chart is an indicative of the scale of our operation and might appear more straightforward to read than it actually is. This is because certain classes have a much higher prevalence in terms of recorded counts but might not be directly comparable between each other. The reasons for this depend on the type of assessment and how we grade them. For example, Subresource Integrity (SRI) is a security feature that enables browsers to verify that resources they fetch (for example, from a CDN) are delivered without unexpected manipulation. This was introduced in 2016 and it is still being adopted. In addition, we record and grade the presence or absence of SRI for all external resources that are loaded on a webpage. In contrast, for example, with HTTPS to HTTP redirects, we only record their existence (which is always marked as BAD).
Sectors
Looking back at the industry sector performance in the last 6 months, the top and bottom 3 most significant sectors can be traced. Overall, there is space for improvement across all sectors, with Government, Education and Tourism sectors struggling the most to keep their Web Application Security in good shape.
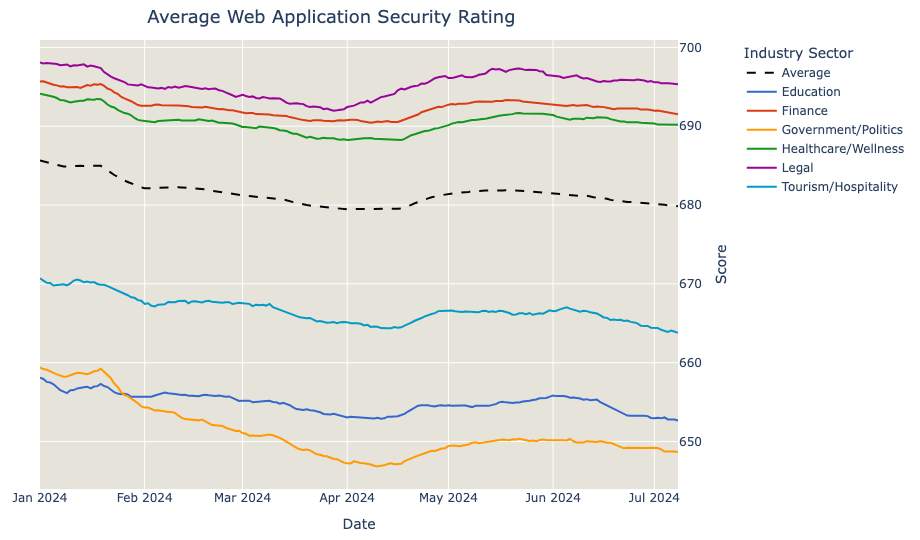
The Legal, Finance and Healthcare sectors are the ones that have shown the most consistent higher ratings across the industries.
Correlations
One of the most interesting observations is the apparent correlation between the Headline score (the Bitsight rating) and the Web Application Security score. Keep in mind that the Web Application Security score is not used nor influences the Bitsight rating at the moment. If you take a look at the heatmap below, what it represents is the Bitsight rating on the Y axis and the Web Application Score on the X axis and the color scale depicts the concentration of organizations, in terms of percentage, on those two scores.
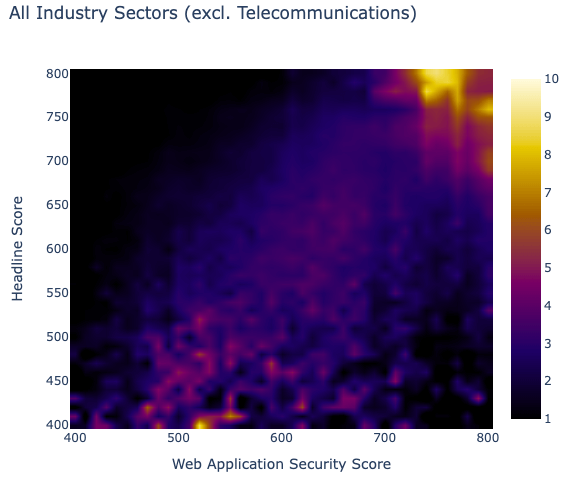
Looking at the above heatmap, one can note that if your organization has a high Bitsight rating, it will most likely have a high Web Application Security score too (top right). It seems to indicate that an organization that has an overall good security posture, measured in all the risk vectors we evaluate in order to assess the Bitsight rating, is very likely to assume that good posture in Web Application Security. As the ratings drop, we can observe that the Web Application Security score tends to dilute somehow, and then concentrates again more near the lower scores (bottom left).
All sectors present this type of concentration in the upper right area of the heatmap. Most sectors show fuzzier concentration when the scores drop, although some show a very clear picture of what we intuitively expect to see, like the Government or Education sectors below.
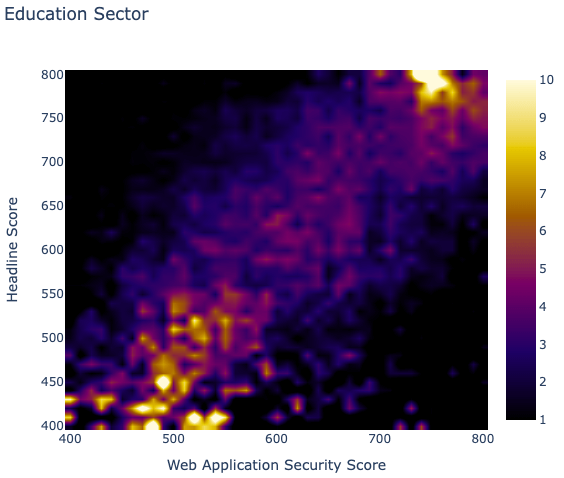
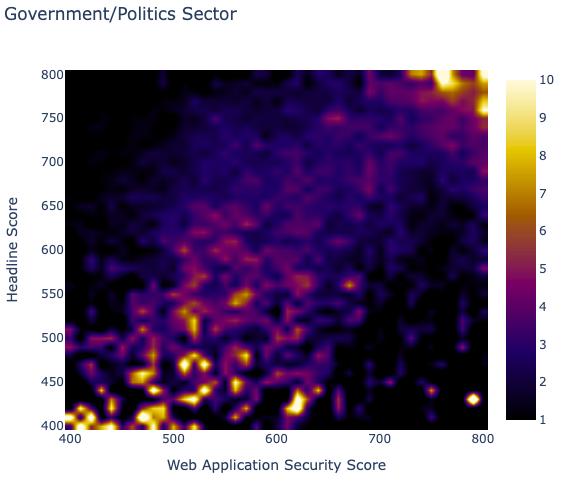
This is an expected and intuitive result, but having the numbers to substantiate these assumptions is what differentiates beliefs and hard evidence.
Conclusions
From our observations, it appears that the organizations that carry a good security posture in all other risk vectors we are assessing, also tend to pay close attention to Web Application Security, generally speaking.
As a whole, Web Application Security is indispensable for safeguarding sensitive information, ensuring operational integrity, and meeting regulatory requirements. By adhering to best practices and utilizing resources such as those provided by OWASP, businesses can strengthen their defenses against the evolving landscape of cyber threats.
Each of our assessments compiles findings based on captured evidence, presenting them in a way that highlights their relevance and impact. With this risk vector, our goal is to measure Web Application Security at an Internet wide scale, and structure our assessments in a way that can deliver clear and actionable insights.