Locky ransomware, metrics and protection

Ransomware is a cash-in machine for criminals and we have just spotted another one come alive this week. Since 16th February, AnubisNetworks Labs team is tracking Locky, a malware that given the high volume of its distribution campaigns will rival with the big ones such as CryptoWall.
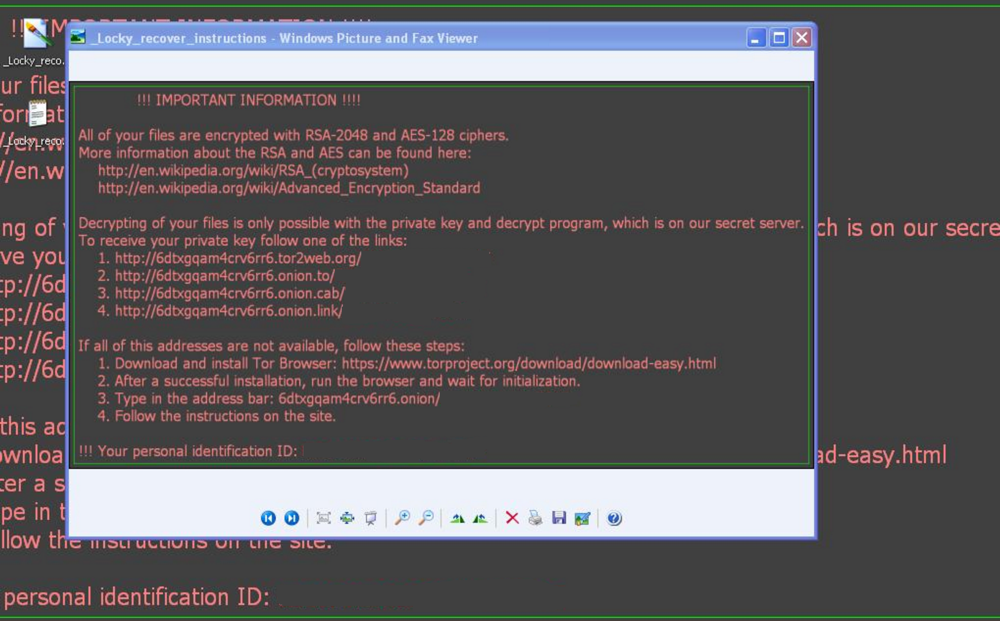
Locky ransom message on an infected system
Delivery
Locky is delivered mostly via email distribution campaigns that have too much in common with another well known threat: Dridex. Actually, the email templates used are almost the same that Bartallex uses to drop Dridex, as you can see here and here.
The email has a Microsoft Office document attached that, when opened and if the user enables macros to run, will download and install the Locky payload.
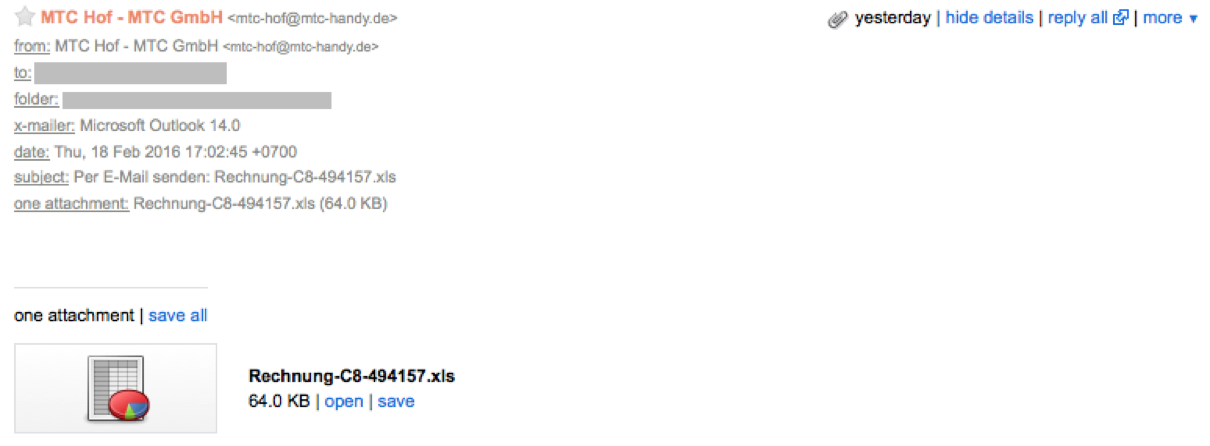
Sample of email message sent to delivery Locky
There are also reports that Neutrino Exploit Kit is being used for delivery, see here and here.
Execution and C2 Communication
After installation the malware will perform the following actions:
- It will delete Volume Shadow Copies to prevent any system backup stored on the infected computer to be restored.
- Contacts the command and control (C2) systems to check in and request a new public/private key pair to use for encryption.
- C2 generates the public/private key pair on server side and responds to the infected system with the public key.
- The encryption process starts, encrypting files with the extensions listed below with the generated public key.
- When the encryption process finishes, the malware asks for the ransom text to be displayed to the victim, dropping the file _Locky_recover_instructions.txt to every folder that has encrypted files and a new wallpaper _Locky_recover_instructions.bmp.\\
The malware communicates with its command and control using hardcoded IP addresses and a DGA (domain generation algorithm). Thanks to Jørgen at Norwegian HelseCERT, we provide some generated domains in the IOCs section of this post.
Encrypted files
Locky will look for files to encrypt in both local file system as well network shares. The following file types are encrypted with RSA-2048 and AES-128:
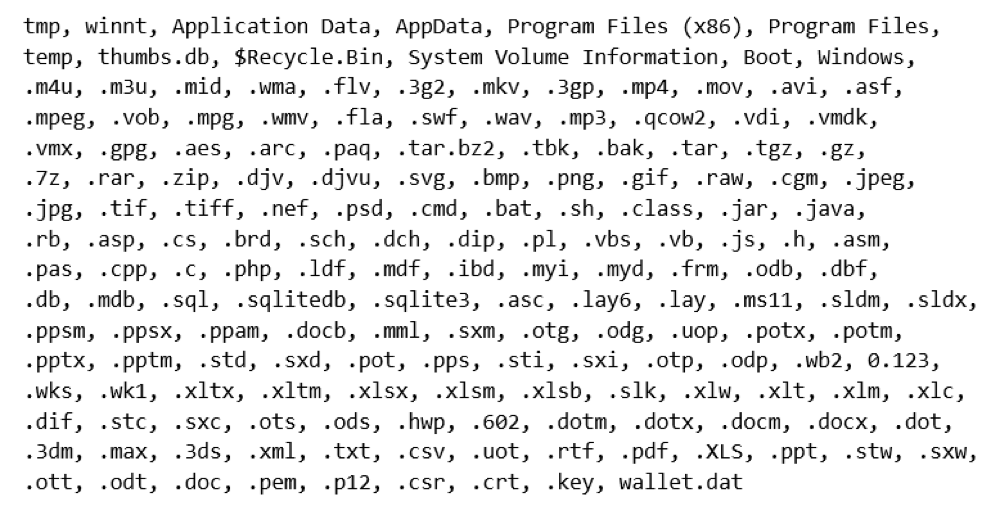
The malware also encrypts the filename of the file, and appends the .locky extension to them.
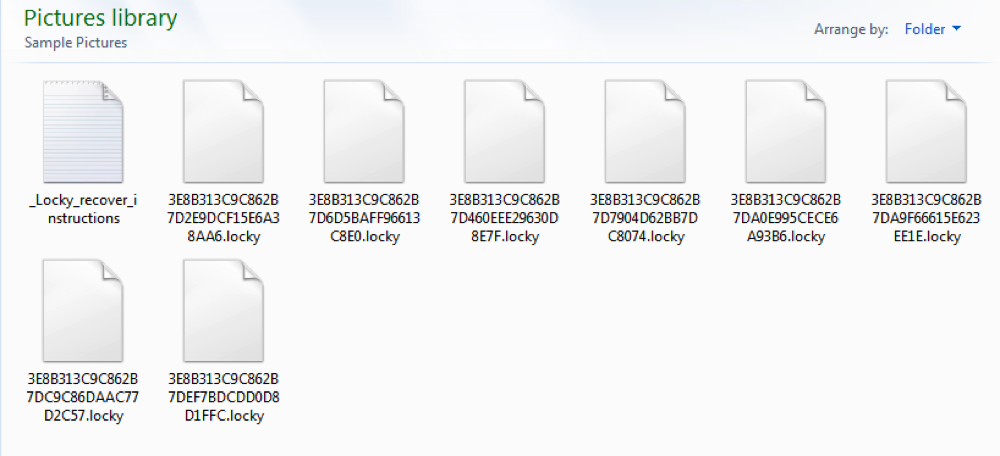
Aspect of the user Pictures Library after the encryption process
The Ransom Page
But, not all is bad news! Locky is “friendly” to its victims and doesn’t put extra pressure on this awful process - unlike other ransomwares, there is no time limit to pay the ransom, at least it’s not advertised at this moment. Normally, ransomware will double the ransom amount after 48h or so.
After paying 0.5 BTC, it’s possible to download the Locky Decrypter.
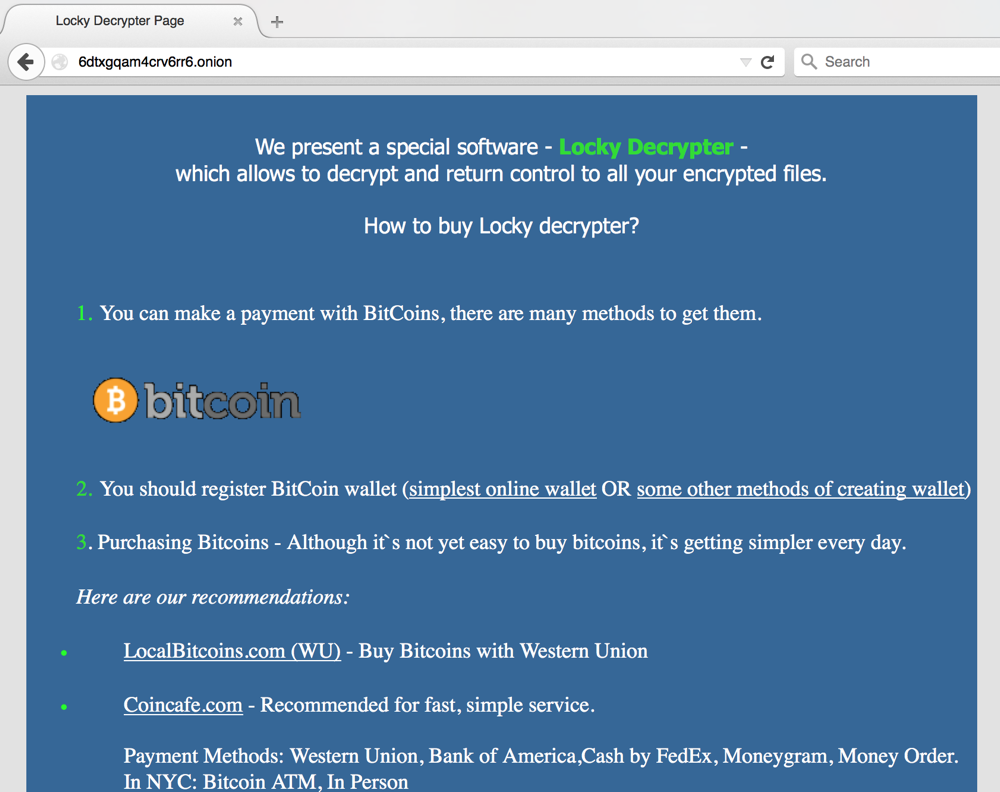
The original payment site
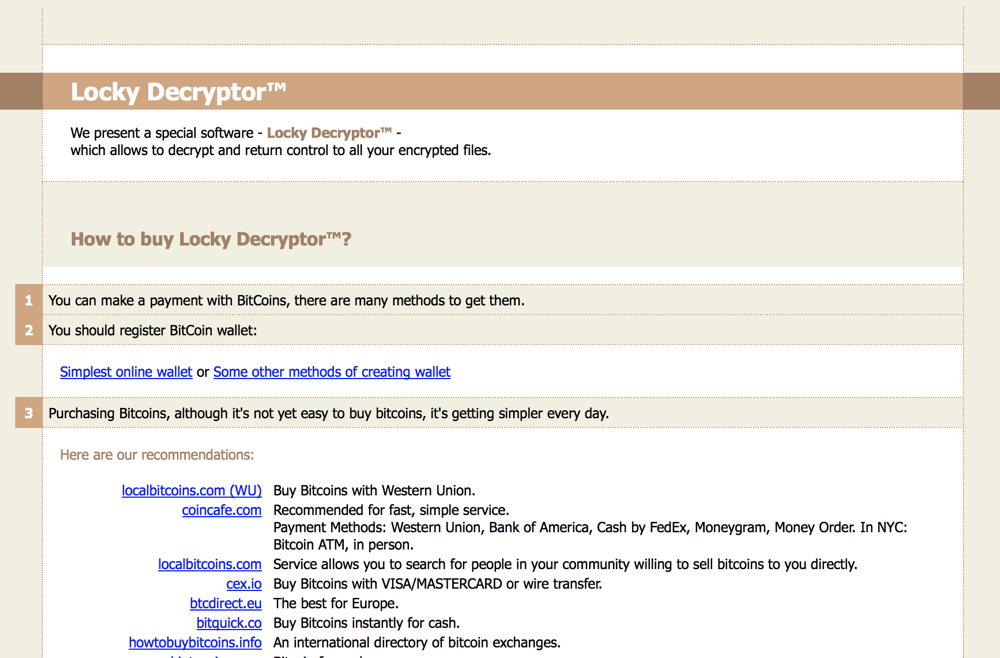
The second version of the payment site
Infections Worldwide
We have been collecting Locky telemetry since it was seen on the wild. The following graph shows unique IP addresses infected with Locky that contacted our Cyberfeed platform in a 48 hour time window, collected from 2016-02-16 17:00 UTC to 2016-02-18 17:00 UTC.
The cumulative sum of infected systems is above +4500. These are actual infections where the encryption process already took place.
The real number of infected systems is slightly higher, since those infections are tracked based on their public IP addresses and it’s common on corporate networks that all the infected systems reach the Internet with the same IP address.
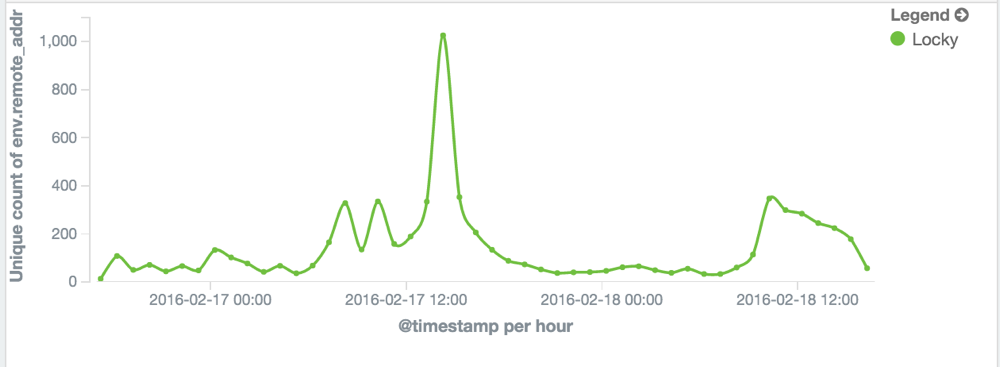
Graph of hits on our sinkholes for a 48h period
You can see volume peaks that represent newly infected systems after massive distribution campaigns.
Here you can see the geographic dispersion of the infections:
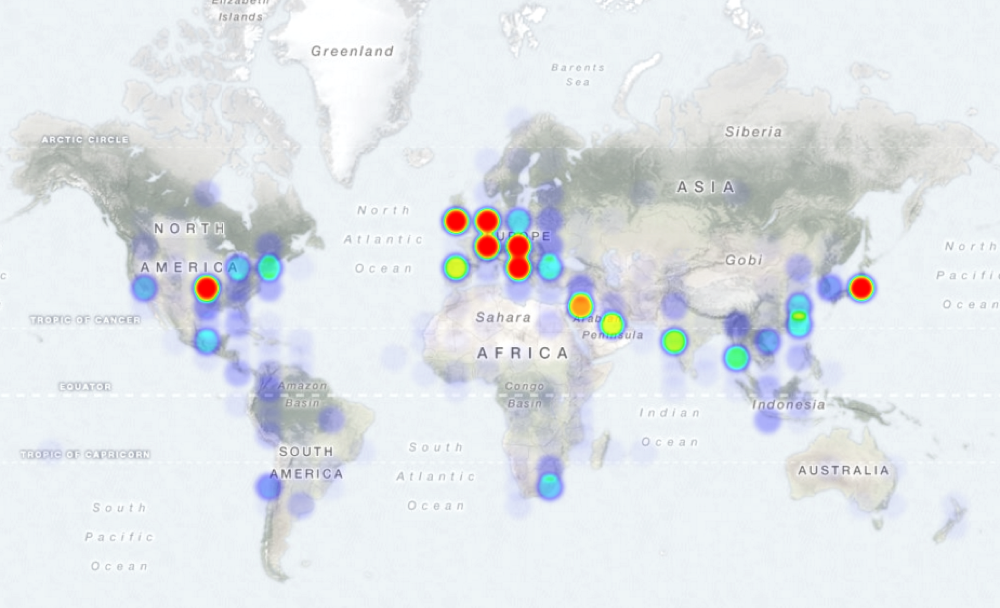
Heatmap of Locky infections
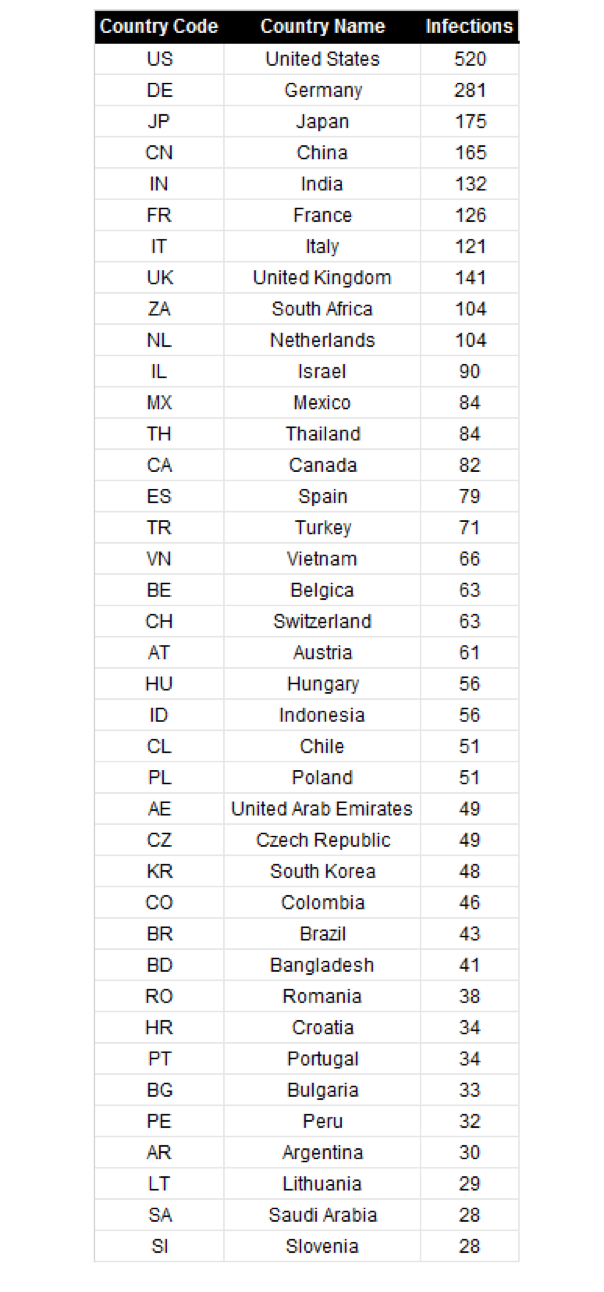
Infections by country - Top 40:
4500 infected systems could appear a small number given the observed email distribution campaigns (see here), but at 0.5 BTC per infection you can do the math and see that criminals are cashing big money with this.
Well, we will do the math for you: 0.5 BTC at the current conversion rate translates to EUR €188 EUR (or USD $210), so 4500 infected systems are a potential gain of almost EUR €850,000 (or USD $943,000) in only two days of operation.
How to Protect
What you should do to not enter the ransom party?
You can start by hunting for infected machines in your network using the Indicators of Compromise (IOCs) provided below, that includes file artifacts left by the malware, C2 IP addresses and domains generated by the Locky DGA. These could help you to produce a decent blocklist for the perimeter that will prevent new infections to reach the Locky C2 and start the encryption process.
But as with every ransomware threat, preparation and defense in-depth works better:
- Don’t allow macros to be executed on Microsoft Office applications;
- Application whitelisting;
- Backups;
- User awareness;
- Antispam;
- Antivirus with updated signatures.
Indicators of Compromise
File artifacts
_Locky_recover_instructions.bmp
_Locky_recover_instructions.txt
*.locky (appended extension to encrypted files)
Registry artifacts
HKEY_CURRENT_USER\Software\Locky
HKEY_CURRENT_USER\Software\Lockyid
HKEY_CURRENT_USER\Software\Lockypubkey
HKEY_CURRENT_USER\Software\Lockypaytext
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Locky
Commands artifacts:
vssadmin.exe Delete Shadows /All /Quiet
C2 - URL payload download
hxxp://www[.]iglobali[.]com/34gf5y/r34f3345g.exe
hxxp://www[.]southlife[.]church/34gf5y/r34f3345g.exe
hxxp://www[.]villaggio[.]airwave[.]at/34gf5y/r34f3345g.exe
hxxp://mondero[.]ru/system/logs/56y4g45gh45h
hxxp://tcpos[.]com[.]vn/system/logs/56y4g45gh45h
hxxp://www[.]bag-online[.]com/system/logs/56y4g45gh45h
hxxp://173.214.183[.]81/~tomorrowhope/09u8h76f/65fg67n
hxxp://iynus[.]net/~test/09u8h76f/65fg67n
hxxp://66.133.129[.]5/~chuckgilbert/09u8h76f/65fg67n
hxxp://www[.]jesusdenazaret[.]com[.]ve/34gf5y/r34f3345g.exe
C2 - IP addresses
85.25.149.246
185.46.11.239
46.4.239.76
94.242.57.45
109.234.38.35
C2 - Tor payment pages (also tor2web variants)
6dtxgqam4crv6rr6.onion
6dtxgqam4crv6rr6.tor2web.org
6dtxgqam4crv6rr6.onion.to
6dtxgqam4crv6rr6.onion.cab
C2 - examples of the DGA generated domains
pvwinlrmwvccuo.eu
ssojravpf.be
gioaqjklhoxf.eu
txlmnqnunppnpuq.ru
lneqqkvxxogomu.eu
kpybuhnosdrm.in
dkoipg.pw
wblejsfob.pw
cgavqeodnop.it
nquvsq.pm
SHA256 - Office attachments samples
46cf36241696d4127b5d32cbde63a672d9a037d9d47bd59ae8346d83424b53c9
566878276748089f6e87b20fd18bfab4018d9e33fae6e28cb87ffb43b1b80582
5ad06eda999a9f2f28c2057ba40bd2f7b6a7cb2e1915104b2724753649e97de5
6cb7c240baae725f22de4ba18f008862a4c08a23c928f9f3617404dda34b67fc
70804dd059ab99aeecd2019d471295e08f004d399fb4cfa5b097d126fdffb306
eee4f20577c2bb49d5d298dd747075e9d21cca981077f941b6222564adf4df2e
SHA256 - PE EXE Locky payload samples
02b00f7615e1fd9091d947dad00dfe60528d9015b694374df2b5525ea6dd1301
05b76b4a79118abd849c22b9d78e37c64802427776e63d690953c7a49ba2811b
0adeb1b7c46b0b33690d8f0c33fa5944e441516cff2b80ca9a6b00555e07c10f
17c3d74e3c0645edb4b5145335b342d2929c92dff856cca1a5e79fa5d935fec2
266826db0014263c857577d1b61cb6ec67707ea3ce6f0b41855098f8b316d84a
2d6120701bd48c6395aa199211ebe5db01229ac48d98eada89da962769d05122
3eb1e97e1bd96b919170c0439307a326aa28acc84b1f644e81e17d24794b9b57
47b27cb727b1ada6c65c7bf30b57537b26080f1f5a6730be91b767427945d731
4da4801c5ae6e801b978c430fb733e28443e98510af818246f34101f5686556c
4e66d9a60ce3829e27aa07f9b8485dd6fe1cb58f147c87e0b5517d7a2a02a8ce
4fd7543247c1f7f2fb5d1c7f99b52ad0a41fb07aa9f388c46a6c5920a848c19a
5434b9ecdb4aba3f8e89ea41917a25bda462e0a2d3958460fd92b8418717ad32
5685955f0cf5fd4159d32c7238c5fa24097c8104876872f1dae42a2b40f996c3
5e945c1d27c9ad77a2b63ae10af46aee7d29a6a43605a9bfbf35cebbcff184d8
658e17adf469ec61f1cc62a0c3932185e94f9557597dcf4714575706efd71141
73c41e29e75e998a186e6fc74b81fbc537f3b232a5d07b5621e8fd3485506b87
77d66d710acddbe66a4f88b9db8775466a35948bad8716c188490ae0aca9a2f9
77dac064d0096dccd5e67c02b9862d02f2671aa3aab12cf09f1d4d14c99b060b
78e9558a9762cf778a3ba9ba61e0ec73e8d81c22d0945e56ea75d197c512883a
7b23fee16740c54dffe9bedae6b37f18072331051012e54747675f4e8c5dea75
7d0adcd0dd84a4941138806cecb1dba5e243af9b33bd09c0dddc382c37eeda8e
7d69f3934be22a9bdcf0e20059d6c0a851218abe9aa07b83795c54e696be6142
99acfca8e9a8bc59f77403e68c88f82f9e5c6fd2ab285b6153e9b57388c5a5e1
9dbed54e6775e26f9669087479795b8f76635a323c80ad6619a86f84f008b23e
a342da44b1d951bf87059344f0c4da9264c9fc041bf9dcf52f59bbfd75e5cf13
acee75cd346795ceb02fc30aa822d13c4132e64fd36b5244dd822199a5a0c0a7
bc98c8b22461a2c2631b2feec399208fdc4ecd1cd2229066c2f385caa958daa3
bf5f58a6fde64003eb0409d2709a28e86d502af7257b265c8ab5db1a06bb9720
c866dcfa95c50443ed5e0b4d2c0b63c1443ad330cb7d384370a244c6f58ce8a5
e95cde1e6fa2ce300bf778f3e9f17dfc6a3e499cb0081070ef5d3d15507f367b
ee6abe4a9530b78e997d9c28394356216778eaf2d46aa3503999e7d6bfbefe90
ee8ac0136fac0ed78903e1f8c8afb934d6970b4dedd70ae526196a328a3d74ee
f4e4cf516f1a6918530d778f1a0c87a9fb2708f8e840e5fed3ed0cf933042d9b
f56655bfbd1be9eab245dc283b7c71991881a845f3caf8fb930f7baabae51059
f96d20ae047e1c9cfd824eb175b0947dda87f2782bfd0b720a34610833ee663e
fbd035d1a91846cb492ffe553d7c76c41c4a8e338320d8a2f9367fec30e3d175
fe7ec54b8049e6dbaba7862da6b349d64de139e88fa37c98102103fca3d13cd2


