Check out our Cybersecurity Risk Rating Solutions Buyers Guide and Recommendations for an in-depth guide to choosing the right security ratings partner for your organization.
How Objectivity, Standardization & Context Reduce Cyber Risk

There are numerous areas of business and enterprise risk that have been measured for years in a standardized fashion — these include financial risk, market risk, operational risk, legal risk, and even IT risk.
But we’ve had to treat cyber risk in a completely different way.
The desire has been to have a consistent way to treat cyber risk — a less tangible, more dynamic risk — in the same way we treat other organizational risks.
Good news: now you can.
There are several key ways that Bitsight Security Ratings allow you to accomplish this:
- Use of security ratings to mitigate cyber risk within your organization
- Visibility into desired parts of your business
- Bi-Directional communication to measure and manage your own cyber risk, convey that risk to interested parties, and understand the risk from your supply chain
Security Ratings
Bitsight rates organizations based on externally-observable data associated with domains and IPs mapped to a rated company. The association of findings to each company is objective and follows the guidelines set out in the US Chamber of Commerce’s Principles for Fair and Accurate Security Ratings.
It’s these ratings — allowing objective, standardized measurements of security posture that can be applied to any company — that companies can use to benchmark themselves against other companies and industries in a way that wasn’t possible before security ratings were created by Bitsight in 2011.
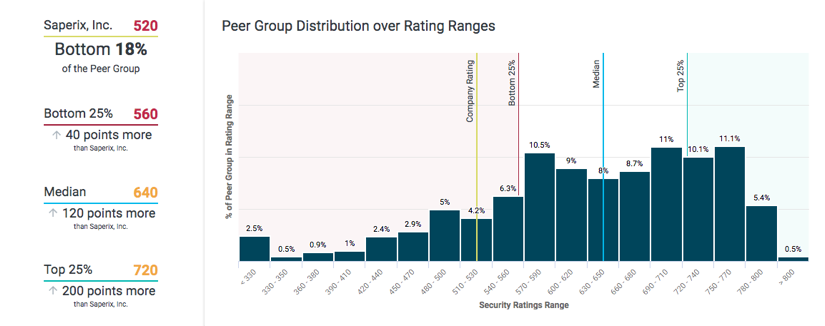
Example of Bitsight Peer Analytics, a service that provides security and risk leaders unprecedented visibility into the relative performance of their security programs against their peers and industry sector, set achievable security performance improvement goals, effectively allocate limited resources, and efficiently prioritize security efforts.
Visibility into Divisions and Segments
However, that value isn’t limited to a single, overarching view of the entirety of your business. Most large businesses don’t operate as one big silo, but rather align their infrastructure to match product lines, geographic regions, and more.
Bitsight goes to great lengths to ensure accurate subsidiary mapping, allowing businesses to monitor their own cybersecurity (or that of their vendors’) using Bitsight’s Company Trees. The depth of visibility Bitsight provides in its reporting allows companies to manage and report cyber risk posture in great detail across any and all subsidiaries - helping them to measurably decrease risk both at the corporate and subsidiary levels.
But sometimes the desire to understand and compare risk goes beyond that top level. With Self-Published Ratings, companies can monitor and manage segments of their business whose structure only they have visibility into. For example, companies can monitor regional offices and compare to one another. Or break out ratings for specific product lines to have a consistent way to measure risks when your company serves as part of a customer’s supply chain.
Companies can also create what is known as a Primary Rating, a type of Self-Published Rating. A Primary Rating allows a company to communicate the risk of the infrastructure it believes most accurately reflects its security posture (e.g. the IPs and Domains that are used in the delivery of services and products your customers buy). Primary Ratings include a Bitsight Security Rating and grades for each of the 23 risk vectors Bitsight measures, but specifically evaluates only the activity associated with the infrastructure you’ve identified as being business-critical.
These Self-Published Ratings (which can be both for internal-use only, or to be shared with other Bitsight users) and Primary Ratings provide a level of context no one else in the Security Ratings industry can match.
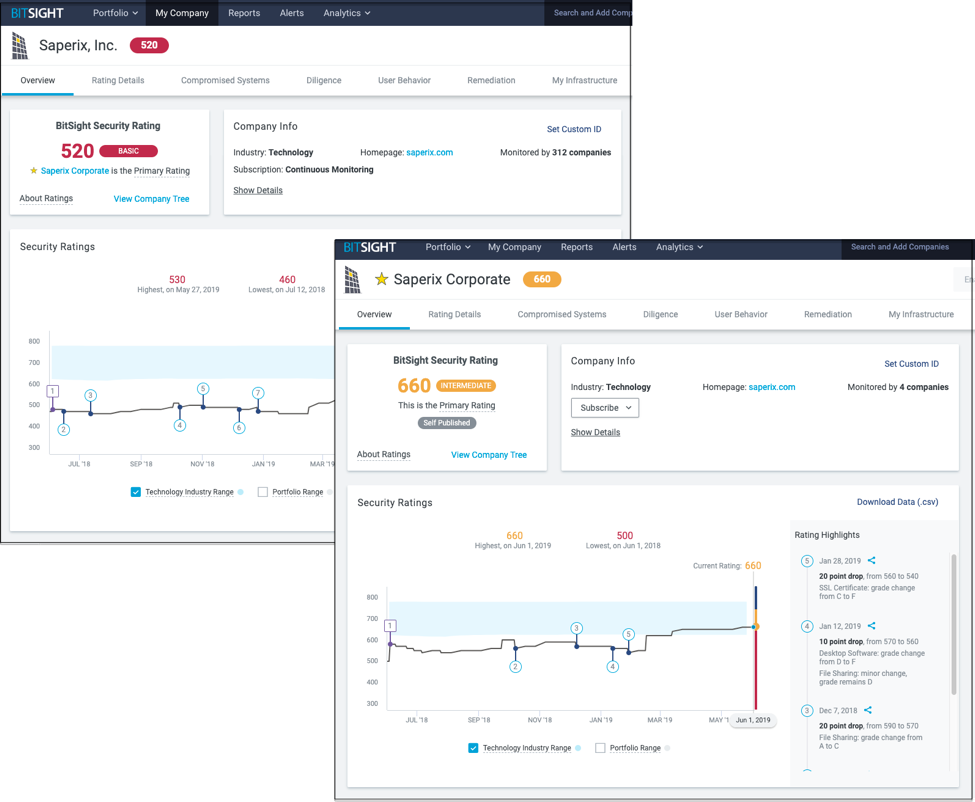
Sample Bitsight Security Rating and Sample Primary Rating
Bi-Directional Communication
As security ratings become the norm, companies are realizing the value of such an objective, standardized means of measuring and discussing risk. As such, communication within these portals — both to your business partners and from — becomes even more valuable.
Companies often “tag” IPs in their organization so that activity picked up from those IPs clearly shows its purpose. If a company has a large guest network, and malware reaches out from that portion of its infrastructure, that company’s ratings details would reflect that tag, and allow companies to understand more about how their organization is structured from a security standpoint.

Those users seeing malware with a “guest network” tag still make their own determination if that activity represents an acceptable level of risk - especially as there are still businesses who haven’t adequately segmented their corporate infrastructure from their guest networks. But that context allows for a better understanding of what couldn’t otherwise be visible outside of a network.
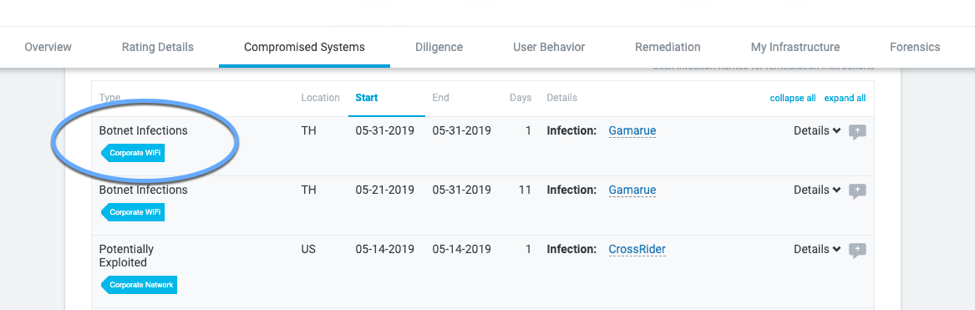
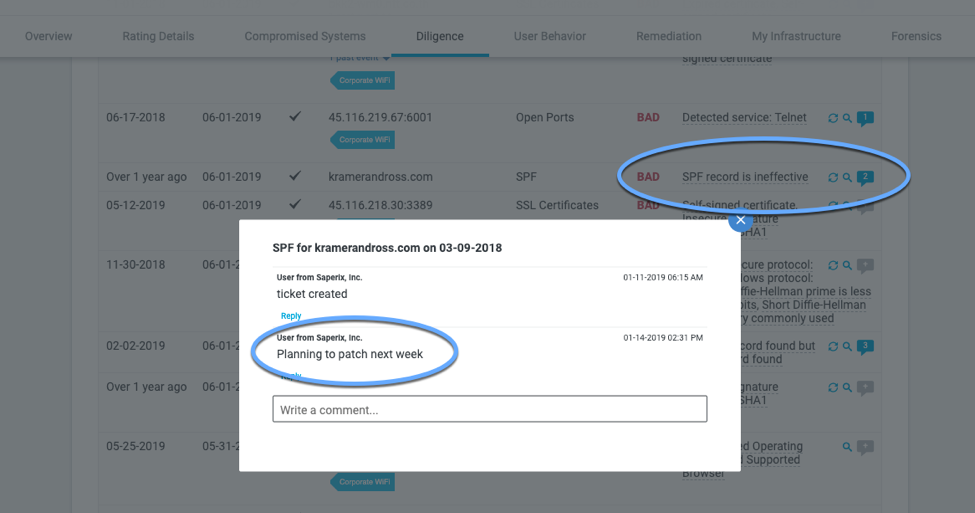
Examples of Tagging and Notations in the Bitsight Platform
Users can also add “annotations” to items in the Bitsight portal. As hard as we all try, sometimes events take place that negatively affect your security rating or IP reputation. Annotations allow companies to communicate specifics with multiple customers at once without having to field constant questions. For example, “Malware reached out due to new firewall with improper setting. Issue remediated.”
Why do these Tags, Annotations, and Self-Published Ratings really bring value?
As the largest ecosystem of security ratings users, the Bitsight Platform is home to more than 25,000 users at 1,700 customers, 135,000 annotations and tags, and more than 2,500 Self-Published Ratings. The level of detail and context provided in the platform is far and above the level of all other SRS solutions’ combined. Recent usage statistics of the Bitsight Platform indicate nearly 1 in 5 users are someone other than a Bitsight customer — users invited to respond to their customers’ security requests by remediating issues Bitsight has found and adding context when necessary. This dialogue within the platform creates more efficient vendor risk management workflows and processes, better internal communications among IT and risk teams, and minimizes meetings and phone calls with customers.
Where competitors often take the word of a company that an identified issue shouldn’t be of concern and then remove that item from the record as if it never existed, Bitsight instead remains objective; creates mechanisms for businesses to communicate context, and ultimately helps companies make more informed, better risk-averse decisions.
By having the greatest levels of context and communication within the most robust security ratings platform, businesses can better monitor and manage their own security performance, communicate that performance with partners and customers, and more quickly and efficiently manage third-party risk programs.
While We’re Discussing Context
Bitsight regularly releases new functionality built to help make managing third-party risk and security performance easier and more efficient. A new advancement that could have flown under your radar is that Bitsight now auto-tags most WiFi networks in our platform.
To help companies more quickly understand and mitigate risks on their own networks, this automated tagging allows companies to more quickly identify the origin of security issues emanating from corporate address space, rapidly ascertain if the issues are originating on production or risk-accepted networks like guest WiFi, and also collaborate internally and externally (with partners) around those specific issues in a very data-driven way.
Additionally, the implementation of WiFi automatically helps organizations shine a light on WiFi access points on their network that they may not be aware of (rogue IPs) and continues to deepen our coverage of the ever-increasing challenge of mobility within the enterprise and across the supply chain. Most organizations struggle with Bring Your Own Device (BYOD) and mobility risks. Bitsight's mobility coverage automatically enumerates connections and the mapping of WiFi access points through which mobile devices connect, checks the patching of operating systems and browsers, detects unique versions of malware targets at the mobile operating systems, and assesses the security of the mobile applications that an organization publishes in the Google Play and Apple app stores.
Bitsight's unmatched visibility into one of the most critical and rapidly changing areas of security risk management for organizations enables rapid prioritization and risk reduction of mobile assets both within the enterprise and across the extended ecosystem.
Just another example of Bitsight taking an already industry-best approach to measuring and managing risk, and making it even more useful for customers.


