Bitsight Observations Into the HAFNIUM Attacks: Part One


On March 2, Microsoft announced that it has detected multiple zero-day exploits being used to attack on-premises versions of Microsoft Exchange Server. According to Microsoft, in the attacks observed, cybersecurity threat actors used this vulnerability to access on-premises Exchange servers, which enabled access to email accounts, and installed additional malware to facilitate long-term access to victim environments.
Since Microsoft’s announcement, the Department of Homeland Security has issued an emergency alert for federal agencies to take emergency actions to combat these cybersecurity threats.
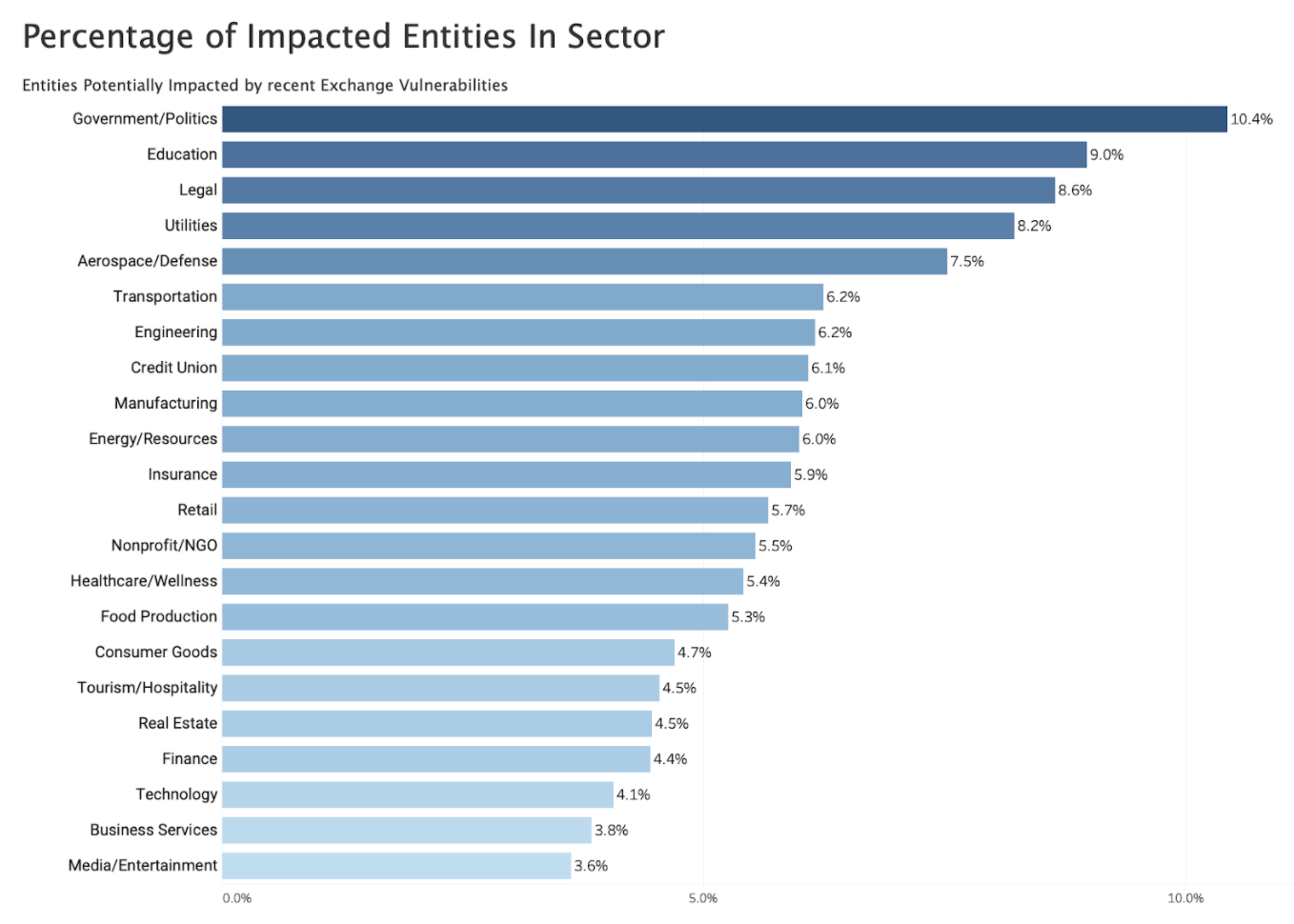
Shortly after Microsoft’s announcement, Bitsight observed at least 30,000 global organizations potentially vulnerable to exploitation. Bitsight examined the prevalence of organizations running Microsoft Exchange Server by sector, finding that the Government sector has the highest prevalence of Microsoft Exchange among all sectors:
Bitsight also examined the prevalence of potentially vulnerable organizations running Microsoft Exchange Server by country, finding that the highest concentration of organizations is within the United States (29%), Germany (13%), UK (8.5%), Canada (5%), France (5%), Netherlands (4%), Italy (4%), Switzerland (4%), Austria (3.5%) and Australia (3%).

This is a notable attack. MS Exchange is extremely popular software and the fact that a state-sponsored actor may be involved presents significant cybersecurity threat risk. Furthermore, with most of these types of severe vulnerabilities, a patching and remediation process is able to take place prior to weaponization; in this case, systems cannot be remediated that have already been exploited.
Organizations are seeking to determine if they or their vendors may be utilizing vulnerable versions of Microsoft Exchange Server in order to understand their cybersecurity threat exposure. Bitsight is currently showing data of potentially vulnerable exchange servers in the vulnerability catalog. Customers can search for any of the Exchange CVEs in the attack chain, by searching for any of the CVEs:
- CVE-2021-26855
- CVE-2021-26857
- CVE-2021-26858
- CVE-2021-27065
Bitsight will continue to update this research with additional telemetry. Please reach out to Bitsight if you have specific questions about the impact of this incident to your vendor ecosystem.
