Eradicate Cyber Threats: Launch Your Third-Party Risk Management Program
Tags:

When launching a third-party risk management (TPRM) program, one of the best places to begin to be proactive about mitigating cyber risk from your third parties is by examining the vulnerabilities present on their network. Despite global knowledge of the harm that vulnerabilities can do to users and businesses alike, they still continue to persist and cause business interruption worldwide.
Today’s digital environmental offers tremendous opportunities for modern organizations. At the same time, there is more risk. Vulnerabilities and infections plague organizations around the globe — and their numbers continue to rise. In 2018, the annual volume of vulnerabilities reached an all-time high of 15,872 CVEs. And as organizations increase their reliance on third-party vendors for outsourced services and solutions, they expand their attack surface.
Understandably, when it comes to managing risk internally proactive controls can be put into place when a vulnerability is identified on the network. However, the struggle lies in identifying and mitigating risk across your supply chain. How can you ensure control across your third-party ecosystem and the potential vulnerabilities that exist there? Once this foundation is established within your TPRM program, you can build on it and shift to a more proactive approach to managing third-party risk — and limiting your exposure.
Bitsight recently published a white paper on vulnerabilities and third-party risk management, “5 Tips to Manage Third-Party Risk”, which highlighted some of our research on vulnerabilities affecting businesses on a global scale and the trends we can see related to them.
With the number of reported vulnerabilities and infections increasing year over year, cyber threats, such as data breaches and attacks causing business interruption, are a top concern for organizations as their supply chain continues to expand and cyber risk threatens their environment.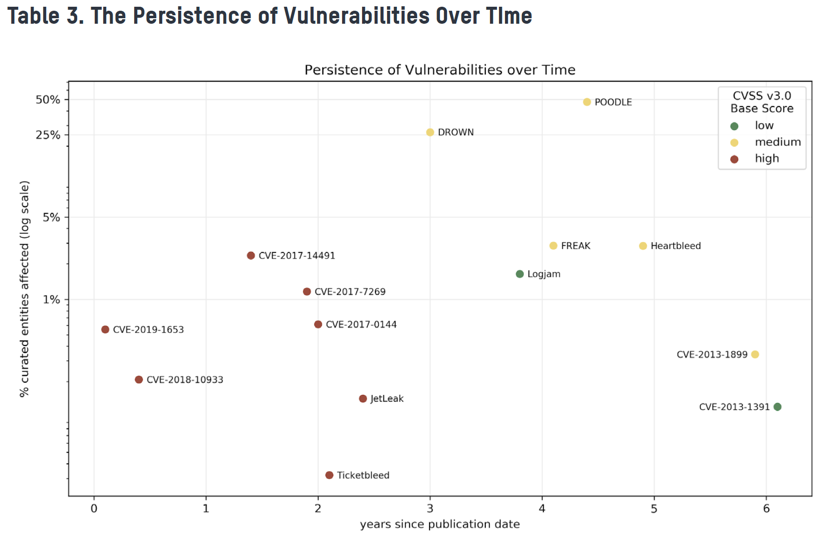 The image above, taken from Bitsight’s newest report, implies that the window for those vulnerabilities and infections to continue to plague organizations through third-party relationships, or their own infrastructure can be as long as two years. Some organizations do not have visibility into that infection time.
The image above, taken from Bitsight’s newest report, implies that the window for those vulnerabilities and infections to continue to plague organizations through third-party relationships, or their own infrastructure can be as long as two years. Some organizations do not have visibility into that infection time.
So how can you launch a third-party risk management program when you have limited visibility into the security posture of your third parties— which are the quickly expanding attack surface of potential cyber threats? One best practice is to start with a quick review of your vendor’s security posture. By using data-centric solutions like security ratings, you can review initial knowledge prior to doing more in-depth assessments like vendor questionnaires.
Every vendor risk manager or TPRM team knows that you need to start somewhere. Initially, you should focus on the areas of your critical third parties’ cybersecurity posture that could have an immediate impact — such as the presence of vulnerabilities or infections.
Bitsight immediately exposes cyber risk within your supply chain, whether you’re launching or scaling your TPRM program, helping you focus your resources and working alongside you and your vendors, to give you the confidence to make faster, more strategic cyber risk management decisions with the resources you have today.


