Emotet spreads itself via email phishing campaigns, using the infected computers to send the malicious emails. The emails can have multiple formats, such as simple emails without any context or replies to stolen email threads. Typically, the emails can carry either an attached Excel/Word document, a password-protected zip file, or a link to download the document. More recently, on April 22, our team spotted Emotet using LNK files instead of the usual Excel files, showing that the threat actors are trying to improve their tactics to increase their infection success rate.
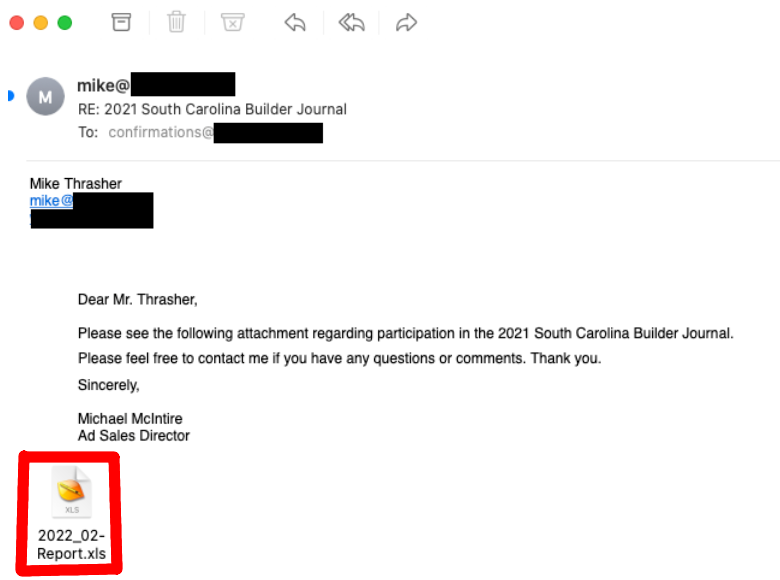
Below is an example of a hijacked email thread with an attached Excel XLS file:
Figure 1. Hijacked email thread (observed by Bitsight)
When opened, the attached Excel file asks the user to enable the macros:
Figure 2. Emotet XLS file (observed by Bitsight)
Once the user clicks “Enable Content,” Excel runs a macro that will try to download and execute the Emotet payload. Below, we can see what a complete process tree looks like when the macros are enabled:
Figure 3. Emotet infection process tree (https://tria.ge/220517-g92l5sgac3/)
As seen above, the process tree ends with Emotet being launched via regsvr32.exe.
If the compromised user has administrator privileges, Emotet sets up persistence by creating a Windows service that will run automatically. If the user has regular permissions, a new key gets added under the Windows registry key "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run".
Once installed, Emotet starts polling tasks from the command and control servers. These tasks can instruct the bot to either execute an Emotet module or a third-party malware.
Typically, we see Emotet trying to steal information (email client passwords, email contacts, email threads, and saved browser credentials) and turn the victim's computer into a spam bot capable of sending emails using the stolen credentials.
In some cases, we see Emotet trying to install third-party malware, which means that the botnet operators will provide access to other threat actors that operate a different type of malware. Since the re-emergence of Emotet, we have seen Emotet delivering malware such as CobaltStrike, Qbot, and SystemBC.
Since March 2022, Bitsight has observed Emotet targeting more than 3 million unique email addresses with spam.
Figure 4. Total targets (observed by Bitsight)
One thing that is interesting to note about Emotet is that there are occasionally time periods where no emails are sent at all. This is typical of Emotet’s behavior, and usually comes when the operators are working on an update to the malware. Time periods of no activity are typically followed by periods of heightened activity when a new wave of spam emails is being sent.
Since March 2022, Bitsight has observed more than 300,000 unique stolen email credentials, suggesting that Emotet is again becoming a significant malware threat.
Figure 5. Total stolen credentials (observed by Bitsight)
Japan and Italy in the Crosshairs
While Bitsight observes a significant number of top-level domains being targeted, Japan stands out as one of the most targeted top-level domains. Our observations are consistent with previous reports from Japan’ s CERT, JPCC, describing the rise in Emotet infections affecting Japanese email addresses. Besides the interest in Japan, Emotet regularly targets Italy with malicious email campaigns.
Since the beginning of March, we have seen .COM, .IT (Italy), and .JP (Japan) as the three most targeted top-level domains within the spam targets. The remaining top-level domains that complete the top 10 list of most targeted TLDs are: .BR, .MX, .NET, .CA, .FR, .ID, and .DE.
Figure 6. Spam targets top 10 TLD (observed by Bitsight)
During the same period, we have observed that .COM, .JP, and .MX (Mexico) are the top-level domains that are observed to have the highest number of stolen email credentials. The remaining top-level domains that complete the top 10 list of TLDs within the stolen credentials are: .IT, .BR, .NET, .ZA, .IN, .ID, and .AR.
Figure 7. Stolen SMTP accounts top 10 TLD (observed by Bitsight)