Dridex Botnets

Dridex is a banking trojan that uses an affiliate system for its botnets. We have documented the Dridex communication and P2P protocols in the past. In this post we want to shed some light about all the known botnets, their respective geographic targets, and how they are organized.
The Dridex operation is segregated into major botnets that use a different command and control (C2) infrastructure, but share the same conceptual network design and architecture. Each major botnet is then segregated into small logical botnets that share the same C2 infrastructure. Each botnet is identified by a botnet ID.
Botnet segregation is employed because of multiple reasons, some are:
- Accountability for each Dridex customer;
- Specify targets per botnet;
- Resilience of the overall C2 infrastructure;
- The ability to aid the logistical effort to extract information from infected systems;
- The ability to differentiate mule networks used to extract money from stolen banking accounts.
Back in 2015, the Dridex ecosystem was constituted by nine botnets (120, 122, 123, 125, 200, 219, 220 and 320). Botnets 120, 200 and 220 were the most active, with predominant infections in Europe, North America and Asia.
In 2016, Dridex operators have removed some of these botnets and created new ones, expanding the geographic targets of their operation. As of May 2016, there were twelve botnets (120, 220, 301, 121, 122, 123, 125, 222, 223, 225, 302 and 322). Between June and August nine new botnets appeared - six of them targeting Switzerland (124, 38923, 1024, 144, 1124, 1234) and three targeting several other countries worldwide (444, 228 and 1044). Between September and October, three more botnets appeared (344, 333 and 404).
The Christmas season is a busy period for most botnet operators, and this year it brought seven more botnets to the Dridex ecosystem (2020, 2302, 3302, 48048, 5302, 420, 5502). One distribution campaign was observed for each of these botnets. Currently, there are 31 known dridex botnets, although not all are active.
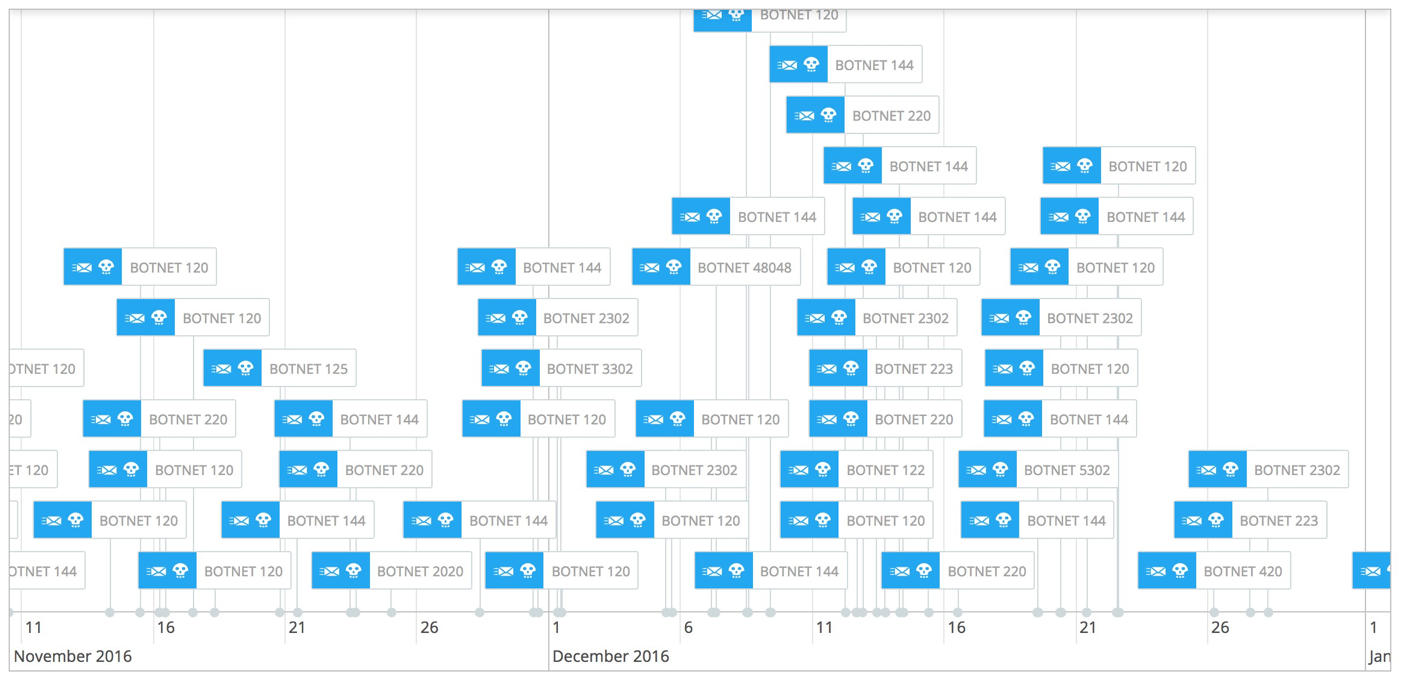
Dridex distribution timeline between November and December
The following table lists each botnet, their respective dates of appearance, and geographic targets:
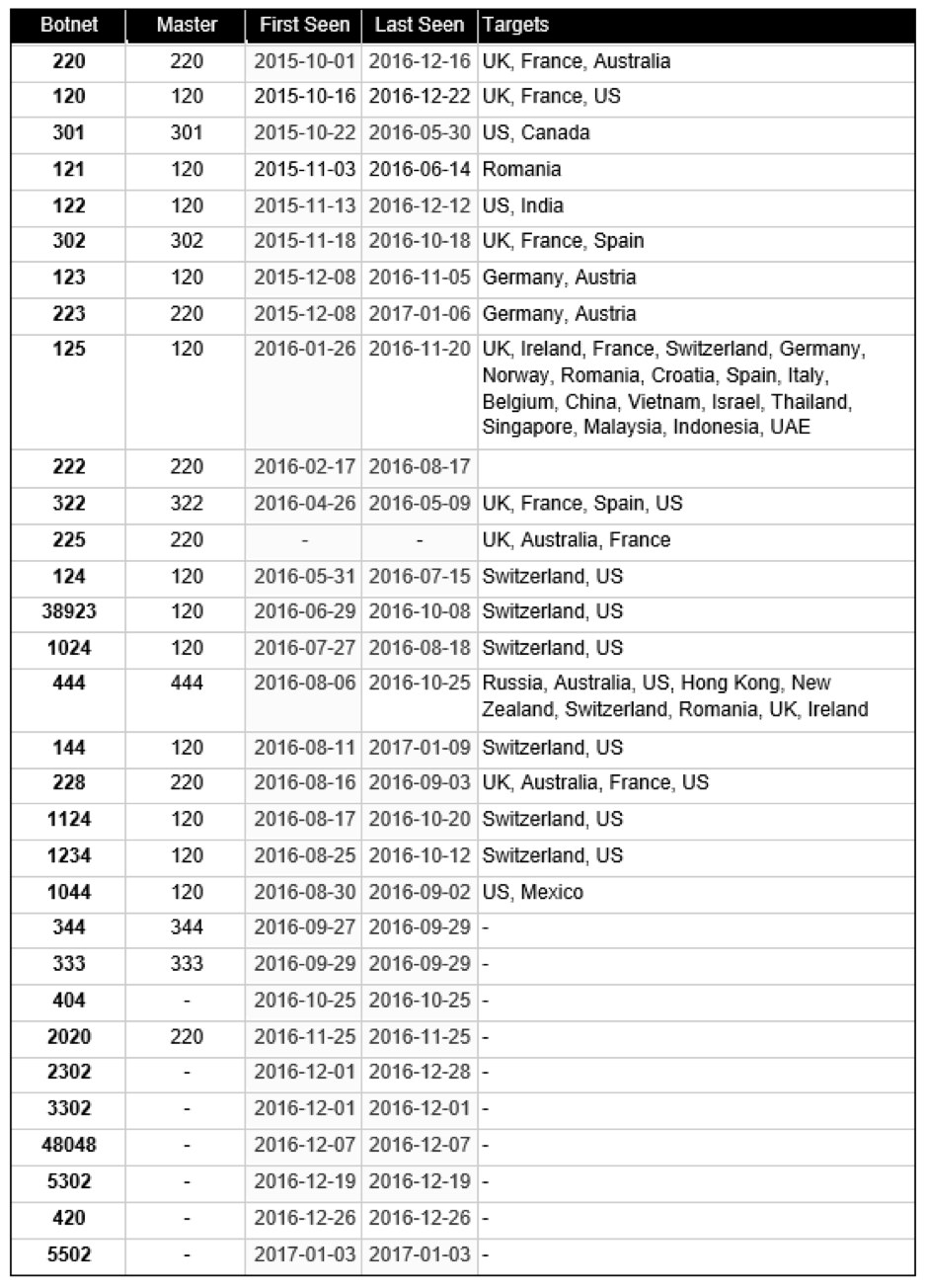
Notes:
- This list features botnets known since October 2015, some of the botnets listed are older.
- Master refers to the master botnet. Dridex botnets are normally logical segregations of a master botnet.
- Targets are based on the configuration for each botnet.
- Botnets without targets were identified, but not fully analyzed (no config files).They are listed here for reference.
- Last Seen refers to the last date a distribution campaign was observed. It does not refer to the last date the botnet was seen alive.
Samples
Listed below are the latest samples (droppers) distributed for each botnet:
Botnet Date SHA256
144 2017-01-09 608e3eadcba943713926fe21f460b23aa3e9e94203c39450403814dc30b506ff
223 2017-01-06 ce96512e8b6e5ff3ce5560bd9d635fe5a6ce6252ba33d02410d7720011e4c636
5502 2017-01-03 326d9bf458c589d7988886d111b6933db21efc950bfa1b44b1814c9dfdcb674b
2302 2016-12-28 15aa456e374761fe7794fed5586e1993f426321dd4e5aa58a61c8732724392e1
420 2016-12-26 8ef0017a498781030426b878b740e5a365cc4946dcc4fdb22b39ac3685312300
120 2016-12-22 1105eb8facb98be597dbd8e109a0ec3bf884aa65d8ee4148a09f2af8e759cfc2
5302 2016-12-19 c3506ebb5440fcbe926e0daf0c2719ffff6a5df2ebb85fdec65db03da7fca8d6
220 2016-12-16 c72e1cd0b65ad2434ffd3adafc4690fb3926c744dc915e74871f68eb7dc6f81b
122 2016-12-12 b2a11c8b096c114ec33de82d9cbaa742479bafa3ca8907b886ba4c6890e64003
48048 2016-12-07 2b1ed063e603b6512b7e80de71ca5f3c5cd2dbcfab8393d38c5eefa8dcdec605
3302 2016-12-01 3e61666ac9e5f74f20c34a11d000f15ed1efbe35092277e8825716be513af6f5
2020 2016-11-25 0c872f38111dd530657c1fa45aadc8452e4e818214f7dceb089be54d98bad27a
125 2016-11-20 05555f42deff52cf720301b5e160682adbf16b1cc312b39580899224269e9979
123 2016-11-05 0f71b07e1e48ea95d9eb2b469ccda3e6f16f949d10ebf83c10156cd10b91ef38
404 2016-10-25 96b73cc722aa7a1e9577f2cddf15a417674743113172920dd4d73d4e7f0cf45a
444 2016-10-25 28e94dfd974d4e04dfc1ecef9010d4736eb0c7e9601c04748a9df3fb1f7eab9f
1124 2016-10-20 58b1886bbdd4f7d0a261975c7b55c2ca0b849098907a76be489dfd05759da08c
302 2016-10-18 dd1758fc35df5771cd67ccd918db43762e8ab5bafd8c53e75675822005bce5a9
1234 2016-10-12 a523505833f19c37069f2a68a1549d09a08afe36f0e35986ad753892e417c74e
38923 2016-10-08 c632547769b7118abd080a34f7c36d5a8281df8b30fa0eb897011474a0852ffe
344 2016-09-29 5b87f1c4fb67429eecb07fd3e829d0d86b04483eecfff5a7435ef2dd8886b9d9
333 2016-09-29 9a3d814d22f6c0d21850b018edd206908b554136b61c68773080fd800eb7e128
228 2016-09-03 10d3f7455c5055f409328e6a0f6a5b7efa1316ca5307ed96be6a4c73020e5b28
1044 2016-09-02 707cec6955c39f7e952a2440069b0cfc699e56b92f8b63c2d4713c897ba29095
1024 2016-08-18 fc39a8ef9567ce977215b8699762843d4f8a98504d9495bf9f8edad0a60b5fcb
222 2016-08-17 667fe7b25d6f12f016c7d26bf5495a18f89f3bf52feecf75ea16a9e03849133a
124 2016-07-15 207b4ae38b3a5c51614aacd6b9d09bff242b23fab777446e9f752eefde57bac8
121 2016-06-14 bdbb7b76002fe1a27997eccd8bbac20842e8de28923b46121dd4f78ee481e0a8
322 2016-05-09 33ec0703fe7930c2ddd5dfb3873a8d5761824f480c7e1713a8fa969cb9570ad7
301 2016-04-13 d587bd84db774a6f06613ffad515f93e729287212f1d9988e6f21c377d5c4cb1