Stay ahead of the compliance curve. Dive into our playbook curated by Tim Grieveson, Senior Vice President and Global Cyber Risk Advisor. Unearth insights to not just comply but lead in the era of NIS 2, DORA, PS21/3, and emerging cyber regulations.
DORA Compliance 101
Tags:


What is DORA?
The Digital Operational Resilience Act (DORA) is a pivotal regulation aimed at enhancing the operational resilience of financial entities within the European Union. By establishing comprehensive requirements for managing information and communication technology (ICT) risks, DORA ensures that financial institutions can withstand, respond to, and recover from all types of ICT-related disruptions and threats.
The 5 DORA Requirements
Cyber risk management strategies and third-party risk management programs in particular need to evolve to address DORA requirements across five key pillars:
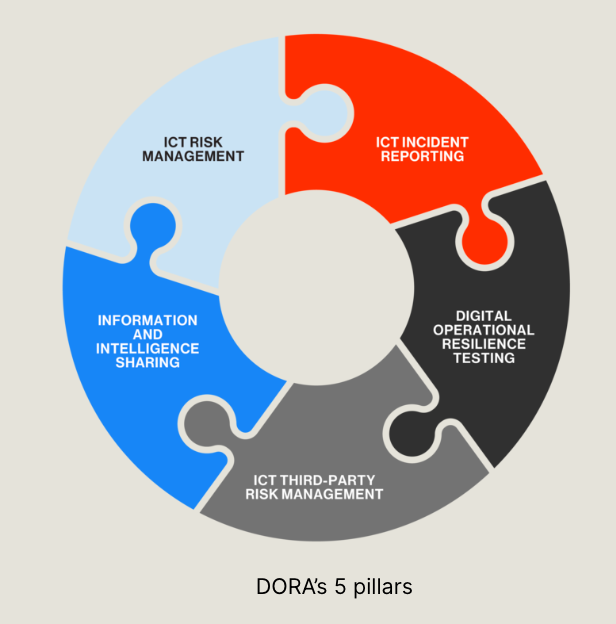
1. ICT Risk Management
Financial entities are required to implement robust Information and Communication Technology (ICT) risk management frameworks. These should be integrated into their overall risk management strategy and encompass identification, protection, detection, response, and recovery measures. The frameworks should also address internal and external risks, including those posed by third-party providers, and ensure governance oversight with clear accountability at the senior management level. Regular assessments and updates are critical to adapt to evolving cyber threats and vulnerabilities.
2. ICT Incident Reporting
DORA mandates a structured process for reporting significant ICT-related incidents, including classifying incidents based on severity and providing details such as impact and response actions. Entities must notify competent authorities without undue delay, ensuring timely responses and facilitating coordinated efforts to mitigate broader impacts across the financial sector.
3. Digital Operational Resilience Testing
Regular testing of digital operational resilience is a core requirement under DORA. Entities must conduct vulnerability assessments, penetration tests, and scenario-based testing that simulate real-world cyber threats. Critical entities may also be required to conduct Advanced Threat-Led Penetration Testing (TLPT). Insights gained from these tests should inform continuous improvements to resilience strategies and cybersecurity frameworks.
4. Information and Intelligence Sharing
DORA encourages the sharing of cyber threat information among financial entities, fostering collaboration to strengthen the sector’s overall defense mechanisms. Information-sharing arrangements, including participation in industry-wide platforms, enhance collective awareness of emerging threats and promote best practices. Regulatory cooperation is also emphasized to support coordinated responses to systemic risks.
5. ICT Third-Party Risk Management
Entities must assess and continuously monitor risks associated with third-party ICT service providers, ensuring that contractual agreements include provisions for security, incident reporting, and operational resilience. Regular vendor risk assessments and continuous monitoring are key to achieve this. Critical ICT third-party providers may be subject to additional oversight to safeguard the financial ecosystem.
Who Does DORA Apply To?
DORA's scope is extensive, encompassing a wide range of financial entities, including:
- Banks and credit institutions
- Insurance and reinsurance companies
- Investment firms
- Payment service providers
- Electronic money institutions
- Crypto-asset service providers
- Financial market infrastructures
DORA extends to third-party ICT service providers that offer services to these financial entities, such as cloud platforms and data analytics firms. It also includes non-EU ICT service providers that work with EU-based financial entities, ensuring consistency in cybersecurity standards across borders.
DORA Compliance Deadline
Financial entities and their ICT service providers are required to comply with DORA by January 17, 2025. This timeline necessitates prompt action to align internal processes, risk management frameworks, and contractual agreements with the regulation's mandates.
With the deadline approaching, organizations should act now to create a compliance roadmap, outlining key milestones such as ICT risk assessments, third-party audits, and operational resilience testing.
DORA Compliance Checklist
To navigate DORA compliance effectively, consider the following steps:
- Governance and Risk Management
- Establish a robust ICT risk management framework integrated into overall risk management strategies.
- Assign clear roles and responsibilities for ICT risk management within the organization.
- ICT Incident Reporting
- Develop procedures for detecting, managing, and reporting ICT-related incidents.
- Ensure timely communication of significant incidents to relevant authorities and stakeholders.
- Operational Resilience Testing
- Conduct regular testing of ICT systems, including vulnerability assessments and penetration tests.
- Implement scenario-based tests to evaluate preparedness for various threat landscapes.
- Third-Party Risk Management
- Assess and monitor risks associated with third-party ICT service providers.
- Formalize contractual agreements outlining service expectations and compliance requirements.
- Information Sharing
- Participate in information-sharing arrangements to stay informed about emerging threats and best practices.
- Collaborate with industry peers and authorities to enhance collective resilience.
To dive deeper into each of these strategies, download our ebook “DORA Compliance: Navigating The New Standard in Financial ICT Security”.
What Are DORA Metrics?
DORA emphasizes the importance of monitoring and measuring ICT risk and resilience. This can be done through specific metrics, including:
- Incident Response Time: Duration taken to detect, respond to, and recover from ICT incidents.
- System Downtime: Total time critical systems are non-operational due to ICT disruptions.
- Third-Party Performance: Evaluation of ICT service providers' adherence to agreed service levels and security standards.
- Testing Effectiveness: Outcomes from resilience testing exercises, indicating the robustness of ICT systems against simulated threats.
DORA metrics should not only capture the current state but also highlight trends over time. For instance, tracking a consistent reduction in incident response times or system downtime can demonstrate ongoing improvement in operational resilience. By diligently tracking these metrics, financial entities can gain insights into their operational resilience and identify areas for improvement.
Achieving DORA compliance is not merely a regulatory obligation but a strategic initiative to fortify the financial sector's stability against evolving digital threats. Proactive engagement with DORA requirements and a comprehensive approach to cybersecurity compliance will position organizations to navigate the complexities of the digital landscape with confidence.
