Request your free custom report and see how you can start reducing your cyber risk exposure across your digital ecosystem: cloud assets across all geos & subsidiaries; discover shadow IT; security risk findings; and more!
Bitsight Analysis of SolarWinds Orion Breach — Part 1: Prevalence

The cyber attack targeting SolarWinds, a provider of network and system monitoring software, is shaping up to be one of the most significant attacks against a critical supply chain partner, with significant implications for national security. Similar to NotPetya, the attackers compromised a software provider in order to gain access to the trusted update channel. Any organization using specific versions of the SolarWinds Orion Network Configuration Manager (SolarWinds Orion) product is presumed to be at risk.
EXECUTIVE SUMMARY
As security and risk leaders search their supply chain to determine potential exposure to this incident, Bitsight seeks to provide insight into key questions regarding the prevalence of Orion in the business ecosystem and to help organizations assess risk to their own supply chain. We analyzed more than 260,000 organizations across 24 sectors to determine the prevalence of Orion software by organization size, sector, and geographic location, finding:
- Orion is observed most frequently within the Technology sector and Government and among large organizations with more than 10,000 employees.
- At least 14% of Fortune 1000 companies are utilizing Orion.
- Orion is observed most frequently among companies headquartered in the U.S.
Bitsight recommends that security and risk professionals immediately determine the prevalence of SolarWinds Orion within their organization and broader third party supply chain in order to mitigate the risk of exposure. Security and risk professionals should immediately report potential exposure to senior executives and the board as soon as possible. Using clear, concise language is critical for security professionals to most effectively communicate risk.
SolarWinds Breach Summary
Details are still emerging about the SolarWinds hack and the SolarWinds hack timeline, but here’s what we know thus far. Attackers targeted the SolarWinds Orion product and inserted malware into the software update function, allowing them to access multiple targets who rely on the Orion software -- including U.S. government agencies. According to SolarWinds, nearly 18,000 of its customers may have been at risk. On Dec. 13, the U.S. Department of Homeland Security issued an emergency order calling for federal agencies to immediately disconnect SolarWinds Orion, recommending that all organizations assess their exposure. By running specific versions of Orion software, organizations are potentially at risk of malicious actors infiltrating their organization through the remote update feature.
Security and risk leaders should immediately determine their exposure to SolarWinds Orion -- both within their organization and across their third party supply chain. Even if your organization is not using Orion, business partners, vendors, and suppliers who utilize Orion may pose a risk to your organization.
To further understand organization and industry exposure, Bitsight analyzed more than 260,000 organizations across 24 sectors to determine the prevalence of Orion software usage by organization size, sector, and geographic location. Bitsight continuously collects externally observable cybersecurity performance data -- as well as critical supply chain information like software product usage -- to help organizations manage their own cybersecurity posture as well as their extended business ecosystem.
FINDINGS
- Bitsight observes Orion most frequently within the Technology sector and Government. 27% of Bitsight’s observations of Orion occur in Technology companies, followed by Government (9%), Healthcare (8%) and Education (8%).
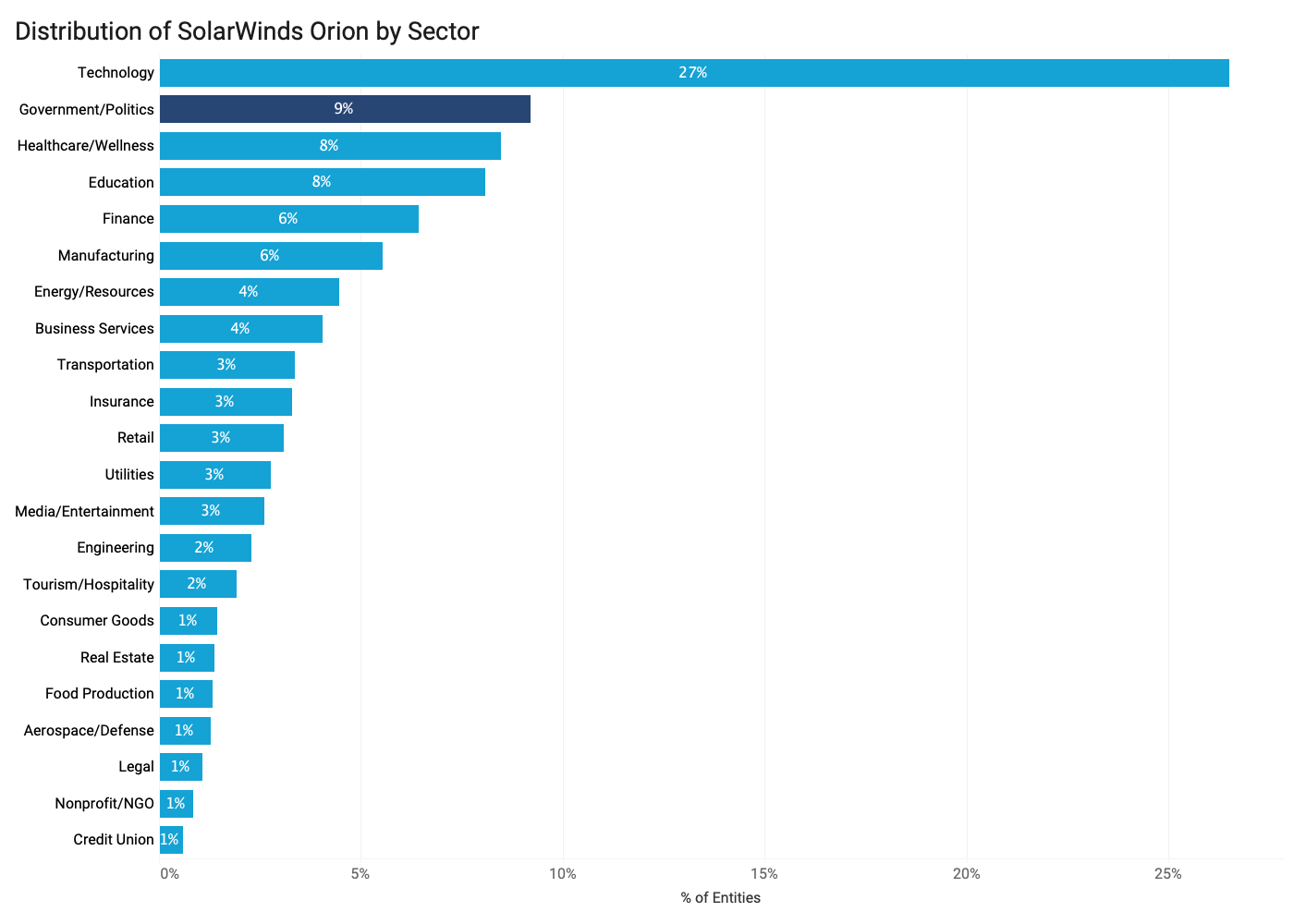
- At least 14% of Fortune 1000 companies are utilizing Orion. Orion is commonly used among Fortune 1000 organizations, with at least 14% of organizations using the software. Among Fortune 1000 organizations observed by Bitsight to have Orion software, the Technology and Manufacturing sectors have the most companies with the software.

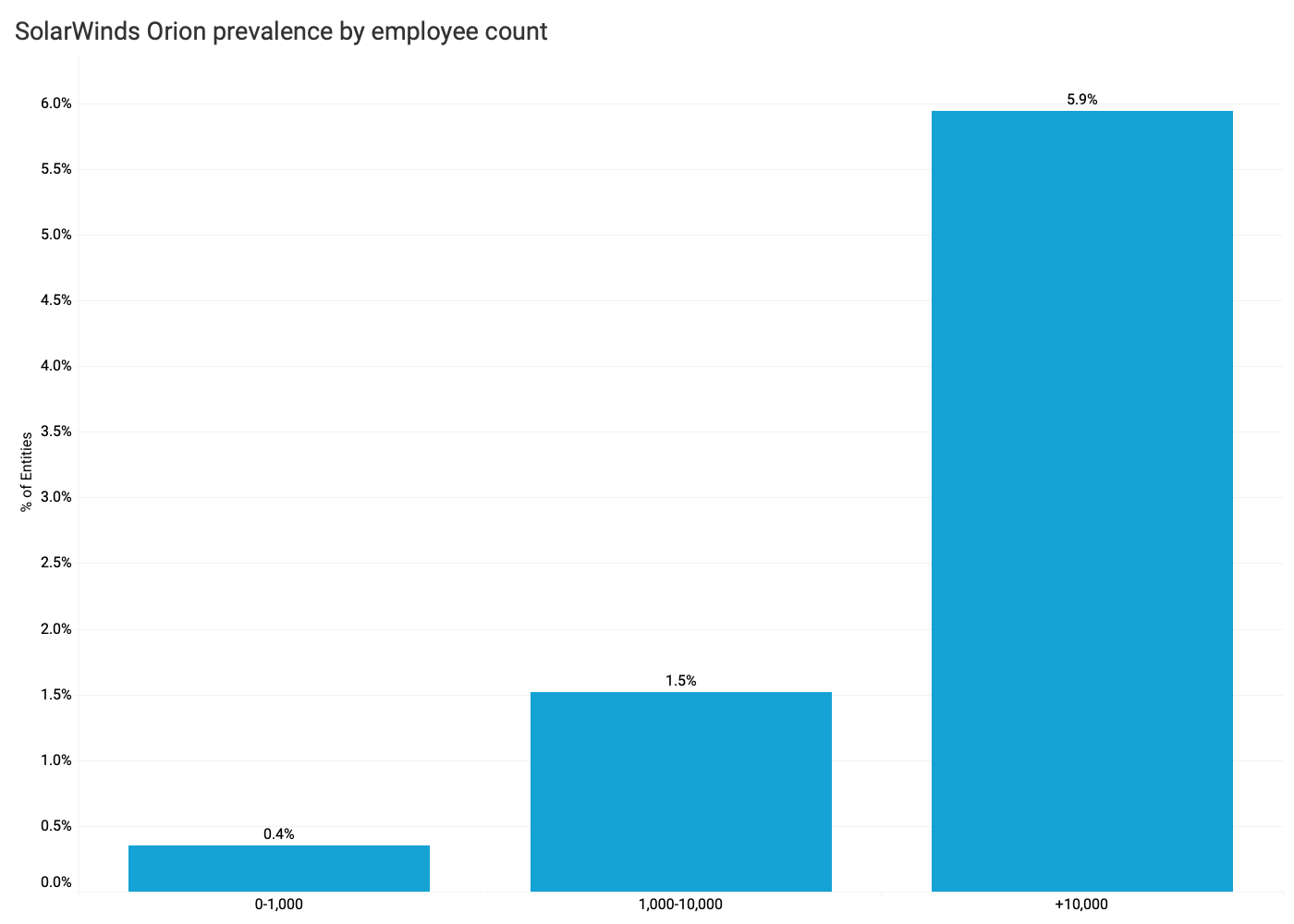
- Bitsight observes Orion more frequently among large organizations with more than 10,000 employees than smaller organizations. Bitsight observes Orion with greater frequency among large organizations with more than 10,000 employees compared to smaller enterprises.
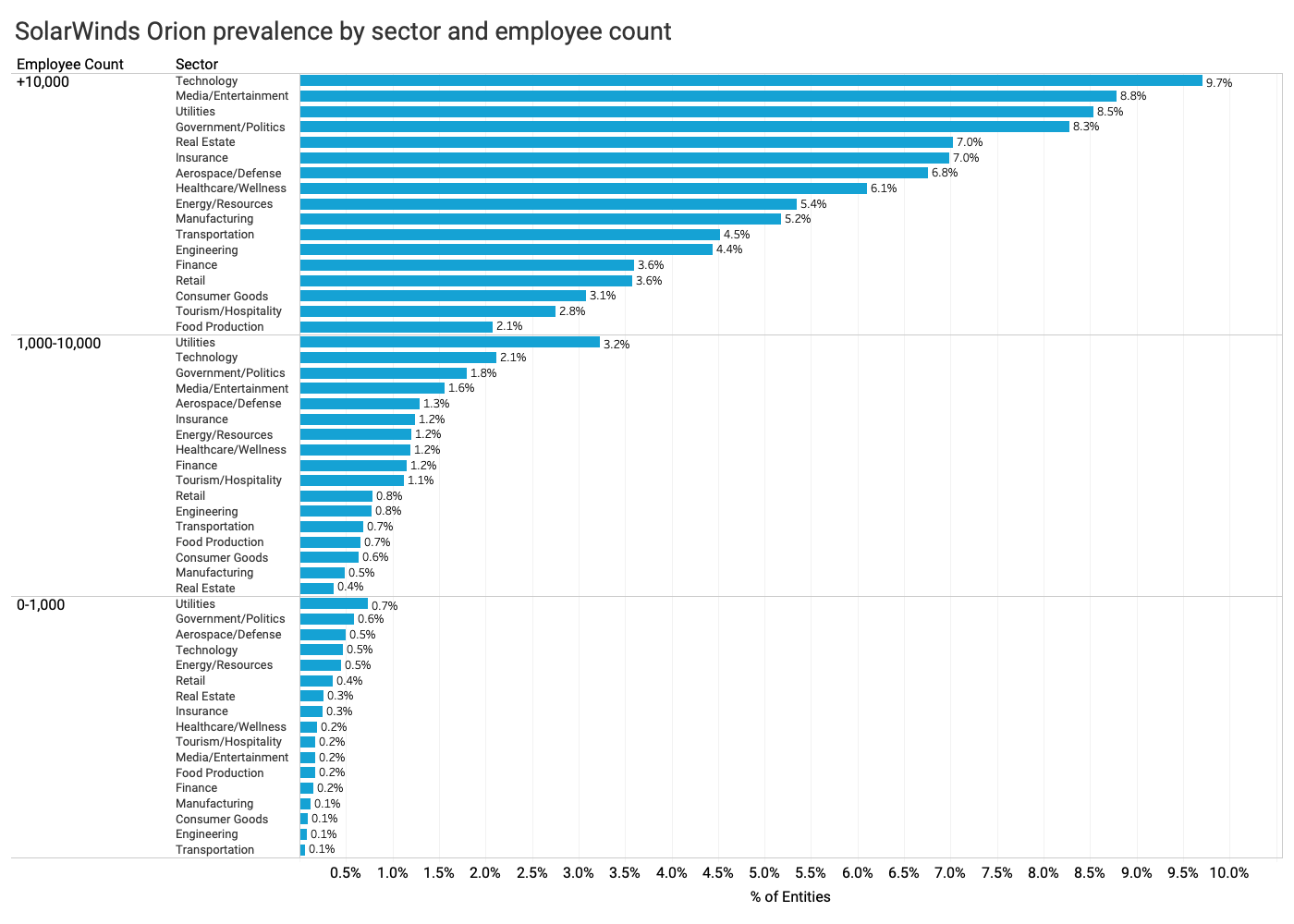
- Bitsight’s Orion observations vary based on sector and employee count. Bitsight observes the presence of Orion among large organizations with more than 10,000 employees in the Technology, Media/Entertainment, Utilities, and Government industries than other sectors. For organizations with 1,000-10,000 employees, Bitsight makes a significantly higher rate of observation of Orion in the Utilities industry than others. Finally, for organizations under 1,000 employees, Bitsight observes Orion most frequently in the Utilities and Government sectors.
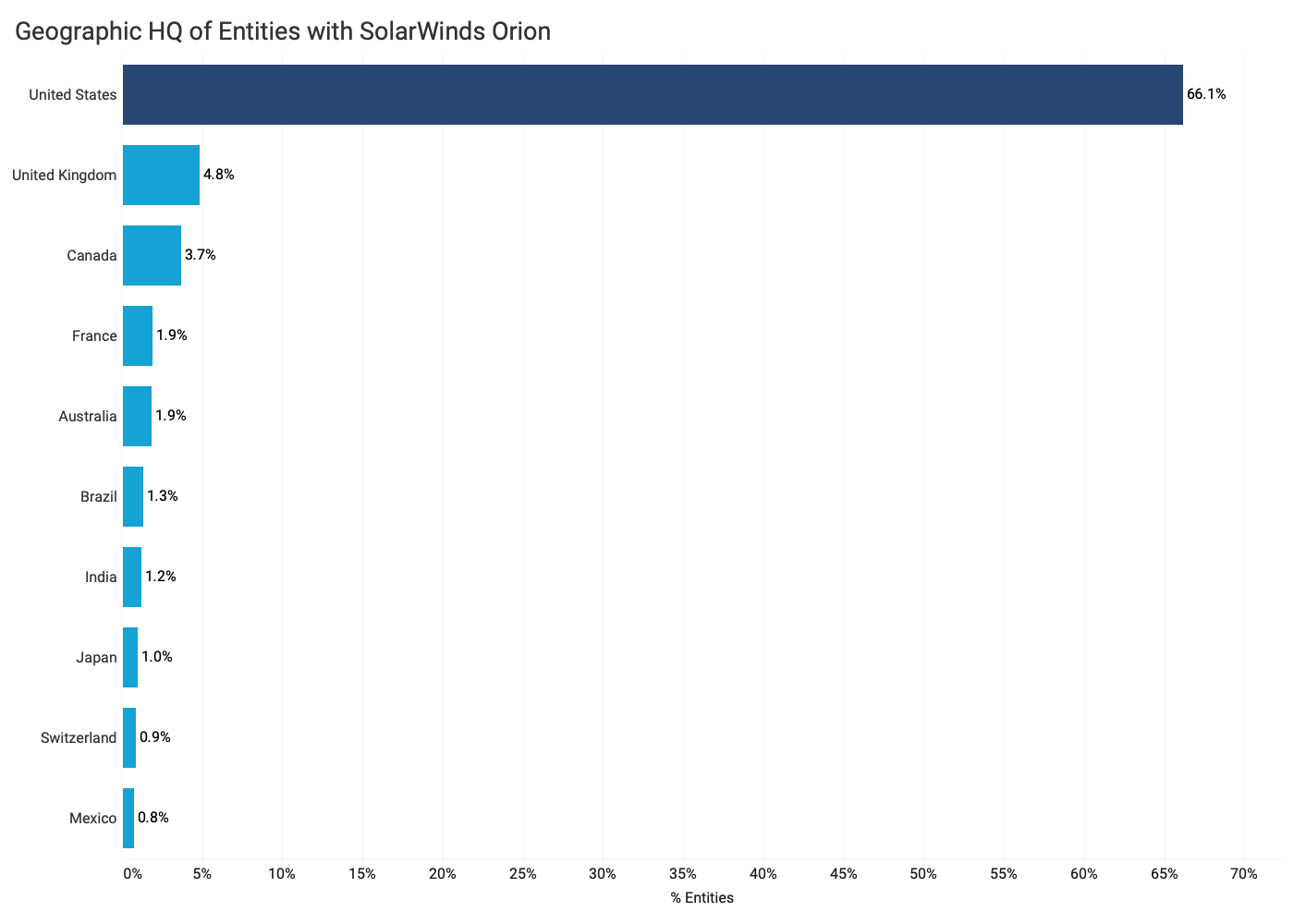
- Companies who use Orion are far more likely to be headquartered in the United States. Bitsight observes that entities who use Orion are far more likely to be headquartered in the U.S. compared with other countries.
HOW BITSIGHT CAN HELP
As the industry continues compiling information regarding the massive SolarWinds hack, there are three critical steps that security and risk leaders must take to protect their organizations:
- Assess prevalence of SolarWinds Orion within the supply chain. Bitsight recommends that security and risk professionals immediately determine the prevalence of SolarWinds Orion within their organization and broader third party supply chain. In addition to the information provided above, consider utilizing Bitsight’s complimentary vendor risk assessment tool to help determine your exposure.
- Report to senior executives and the board. This incident is of significant concern to corporate officers and directors who are responsible for overseeing risks to the enterprise. Security and risk professionals should immediately report potential exposure to senior executives and the board as soon as possible. Using clear, concise language is critical for security professionals to most effectively communicate risk.
- Update your third party cyber risk management program. Security and risk professionals should take this opportunity to examine the effectiveness of their third-party cyber risk management programs. A critical step here is conducting continuous security monitoring of third parties. An effective program should also involve assessing the cyber risk of third parties, properly tiering vendors or suppliers, and collaborating with partners to reduce risk and exposure. Bitsight also allows organizations to freely share critical cybersecurity information with their third party vendors in an automated fashion, creating a strong collaboration among business partners to work together to reduce exposure and improve security performance.
Want to know how you can reduce the risk in your digital supply chain?
